Security Tools
The security tools menu is your friend; it organizes all the security-related functions that you should be aware of, if not implementing, into one menu. Type GO SECTOOLS and you will see the screen in Figure 13.2. Rolling forward on this menu gives you the auditing and reports sections shown in Figure 13.3. Rolling forward again will show more reports, as shown in Figure 13.4, while rolling forward a final time will yield the general security functions shown in Figure 13.5.
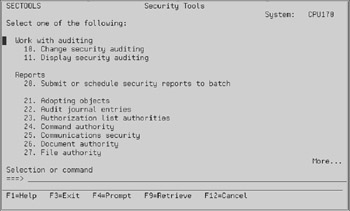
Figure 13.2: Security Tools menu.
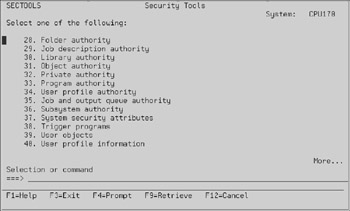
Figure 13.3: Auditing and reports in the Security Tools menu.
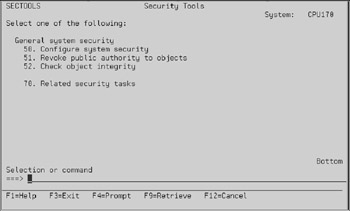
Figure 13.4: More reports in the Security Tools menu.
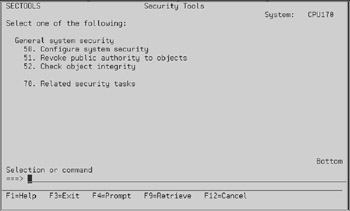
Figure 13.5: General security in the Security Tools menu.
-
Analyze default passwords (ANZDFTPWD):
This option reports (and optionally allows you to change) user profiles that have a password that is the same as the user profile name. The system ships with this huge security breach.
-
Display active profile list (DSPACTPRFL):
Option 2 displays or prints a list of user profiles that are exempt from the analyze profile activity function provided with option 4.
-
Change active profile list (CHGACTPRFL):
Option 3 allows you to maintain the list of user profiles that are exempt from the analyze profile activity function provided with option 4.
-
Analyze profile activity (ANZPRFACT):
The analyze profile activity command disables user profiles that have been inactive for a specified number of days. Use the command to set the number of days, and a nightly job will be submitted to actually disable the user profiles.
-
Display activation schedule (DSPACTSCD):
Use option 5 to display (or print) the schedule of enabling/disabling user profiles created by using option 6.
-
Change activation schedule entry (CHGACTSCDE):
Use option 6 to enable or disable user profiles at certain times of the day. For each user profile you add, the system creates job schedule entries to enable/disable the user profile at the indicated time. Use option 5 to see the scheduled entries.
-
Display expiration schedule (DSPEXPSCD):
Use this option to display (or print) a list of user profiles that are scheduled to be disabled or removed from the system. This schedule is maintained/created using option 8.
-
Change expiration schedule entry (CHGEXPSCDE):
Use option 8 to schedule a specific user profile to be removed from the system at a future time. If any user profiles are on the list, a job will be scheduled to run at 1 minute after midnight to either disable or remove the user profile.
-
Print profile internals (PRTPRFINT):
This option prints a report about the number of entries contained in a user profile. The more entries contained, the larger the user profile.
-
Change security auditing (CHGSECAUD):
This menu option makes it very easy to set up the system value, QAUDLVL. You can specify *ALL to set up all audit level settings, or *DFTSET to set up the most commonly used ones.
When you use this menu option, the security audit journal, QAUDJRN, will be created automatically if it doesn't already exist. You must plan for managing this journal, because it will rapidly eat up disk space.
-
Display security auditing (DSPSECAUD):
Use option 11 to display information about the security audit journal used for auditing security. It also shows system values that control security auditing.
-
Submit or schedule security reports in batch:
This option brings up a menu of options to submit any of the reports to batch. Batch is the preferred method of running reports. All the report options listed on the SECTOOLS menu are also listed on the SECBATCH menu.
-
Adopting objects (PRTADPOBJ):
This option prints a list of objects that adopt the authority of the specified user profile. You can look for a specific user profile (such as QSECOFR), use a generic search, or look at all user profiles.
The report has an option that allows you to print differences between objects that are currently on the system (that meet the selection criteria) and objects that were on the system the last time you ran the report.
-
Audit journal entries (DSPAUDJRNE):
This option displays (or prints) information about entries in the security audit journal. You can filter on entry type, users, and/or a time period.
-
Authorization list authorities (PRTPVTAUT):
Option 23 prints a report of objects (specified by type and/or library) that have private authorities. This report comes in three variations: You can list all objects that meet the selection criteria; you can list only objects that are currently on and are different from the last time you ran the report; or you can run a deleted report that shows users whose authority has been deleted since you last ran the report.
-
Command authority (PRTPUBAUT):
This option prints all commands whose public authority is not *EXCLUDE. This will print information about every command that every user on the system can access.
Because this can be a very large report, you have two options: print all objects that meet the selection criteria or print differences between objects currently on the system and objects that were on the system the last time you ran the report.
-
Communications security (PRTCMNSEC):
Use this option to print security-relevant settings for objects that affect communications on your system. These settings control how users and jobs can enter your system.
-
Document authority (PRTPUBAUT):
This option prints all documents whose public authority is not *EXCLUDE. This will print information about every document that every user on the system can access.
Because this can be a very large report, you have two options: print all objects that meet the selection criteria or print differences between objects currently on the system and objects that were on the system the last time you ran the report.
-
File authority (PRTPUBAUT):
This option prints all files whose public authority is not *EXCLUDE. This will print information about every file that every user on the system can access.
Because this can be a very large report, you have two options: print all objects that meet the selection criteria, or print differences between objects currently on the system and objects that were on the system the last time you ran the report.
-
Folder authority (PRTPUBAUT):
This option prints all folders whose public authority is not *EXCLUDE. This will print information about every folder that every user on the system can access.
Because this can be a very large report, you have two options: print all objects that meet the selection criteria, or print differences between objects currently on the system and objects that were on the system the last time you ran the report.
-
Job description authority (PRTJOBDAUT):
This option prints a list of job descriptions that specify a user profile and have public authority that is not *EXCLUDE.
-
Library authority (PRTPUBAUT):
This option prints a list of libraries that have public authority that is not *EXCLUDE. This will list all libraries that can be accessed by anyone on the system.
-
Object authority (PRTPUBAUT):
This option prints a list of all objects that have public authority that is not *EXCLUDE. This will list all objects that can be accessed by anyone on the system.
-
Private authority (PRTPVTAUT):
This option prints a list of the private authorities to objects. You specify the object type and library when you run the command. You can run the standard three options of reports: all, changed, or deleted.
-
Program authority (PRTPUBAUT):
This option prints a list of all programs that have public authority that is not *EXCLUDE. This will list all programs that can be accessed by anyone on the system.
-
User profile authority (PRTPUBAUT):
This option prints a list of user profiles that have public authority that is not *EXCLUDE.
-
Job and output queue authority (PRTQAUT):
This option prints a list of security settings that affect output queues and job queues on your system. This will list settings that control who can view/change entries in the queues. This report has two options: all or changed only.
-
Subsystem authority (PRTSBSDAUT):
This option prints a list of communication settings for subsystem descriptions that pertain to security on your system. It will only include a subsystem description on the report if it contains communication entries that specify a user profile name. It will list settings that control how work enters your system and how jobs run.
-
System security attributes (PRTSYSSECA):
Option 37 prints a list of system values and network attributes that pertain to security. This report is especially helpful because it not only shows what the values are currently set to, but also makes recommendations about what they should be set to.
-
Trigger programs (PRTTRGPGM):
This option prints a list of trigger programs that are attached to files on your system. Trigger programs provide a hacker with a way to create a Trojan horse on your system. The trigger program runs when some valid function is performed on the database file it is associated with. The system ships with this ability restricted.
This report has two options: all and changed only.
-
User objects (PRTUSROBJ):
Option 39 lists all user objects in a library. User objects are objects that are not supplied by IBM. You can use this report to locate programs that are put into system libraries (such as QSYS) and would therefore probably be in all jobs' library list. This report has two options: all and changed only.
-
User profile information (PRTUSRPRF):
This option allows you to analyze user profiles based on special authorities, user class, or a mismatch between special authorities and user class.
-
Configure system security:
This option activates system security features. It will turn on security auditing, change security system values, and modify system supplied user profiles. Do not run this command if you have already set up security parameters on your system.
To see what this menu option does, retrieve the CL source for the program QSECCFGS. Figure 13.6 shows the retrieved CL source for the configuration option.
QSYS/PGM QSYS/DCL VAR(&IBMREG) TYPE(*CHAR) LEN(300) VALUE('Copyright, - 5799XDH, 5763SS1, 5716SS1, (C) Copyright IBM Corp. 1996. All Rights - Reserved; US Government Users Restricted Rights - Use, duplication or- disclosure restricted by GSA ADP Schedule Contract with IBM Corp. - Licensed Materials - Property of IBM. ') QSYS/DCL VAR(&IBMREG2) TYPE(*CHAR) LEN(300) QSYS/DCL VAR(&LMTCHRTXTM) TYPE(*CHAR) LEN(7) VALUE('CPXB302') QSYS/DCL VAR(&DFTVALUE) TYPE(*CHAR) LEN(10) QSYS/DCL VAR(&APPID) TYPE(*CHAR) LEN(8) QSYS/DCL VAR(&PNLGRP) TYPE(*CHAR) LEN(20) VALUE('QGSECCSS *LIBL- ') QSYS/DCL VAR(&FUNC) TYPE(*CHAR) LEN(4) VALUE(' ') QSYS/DCL VAR(&ENTERVALUE) TYPE(*DEC) LEN(4) VALUE(100) QSYS/DCL VAR(&ERRCD) TYPE(*CHAR) LEN(8) VALUE(X'0000000000000000-') QSYS/DCL VAR(&AUTIND) TYPE(*CHAR) LEN(1) QSYS/DCL VAR(&AUTS) TYPE(*CHAR) LEN(30) VALUE('*ALLOBJ *SECADM- *AUDIT ') QSYS/DCL VAR(&NUMAUTS) TYPE(*CHAR) LEN(4) VALUE(X'00000003') QSYS/DCL VAR(&CALLLVL) TYPE(*CHAR) LEN(4) VALUE(X'00000000') QSYS/MONMSG MSGID(CPF0000) QSYS/CHGVAR VAR(&IBMREG2) VALUE(&IBMREG) QSYS/CALL PGM(QSYS/QSYCUSRS) PARM(&AUTIND *CURRENT &AUTS -&NUMAUTS &CALLLVL &ERRCD) QSYS/IF COND(&AUTIND *EQ 'N') THEN(QSYS/SNDPGMMSG MSGID(CPFB304)- MSGF(*LIBL/QCPFMSG) MSGTYPE(*ESCAPE)) QSYS/CALL PGM(QSYS/QUIOPNDA) PARM(&APPID &PNLGRP -1 0 N &ERRCD) QSYS/MONMSG MSGID(CPF0000) EXEC(GOTO CMDLBL(SKIPUIM)) QSYS/CALL PGM(QSYS/QUIDSPP) PARM(&APPID &FUNC 'CONCSS' N &ERRCD) QSYS/CALL PGM(QSYS/QUICLOA) PARM(&APPID M &ERRCD) QSYS/IF COND(%BIN(&FUNC) *NE &ENTERVALUE) THEN(QSYS/RETURN) SKIPUIM: QSYS/CHGSECAUD QAUDCTL(*ALL) QAUDLVL(*DFTSET) QSYS/CHGSYSVAL SYSVAL(QALWOBJRST) VALUE('*NONE') QSYS/CHGSYSVAL SYSVAL(QAUTOCFG) VALUE('0') QSYS/CHGSYSVAL SYSVAL(QAUTOVRT) VALUE(0) QSYS/CHGSYSVAL SYSVAL(QDEVRCYACN) VALUE('*DSCMSG') QSYS/CHGSYSVAL SYSVAL(QDSCJOBITV) VALUE('120') QSYS/CHGSYSVAL SYSVAL(QDSPSGNINF) VALUE('1') QSYS/CHGSYSVAL SYSVAL(QINACTITV) VALUE('60') QSYS/CHGSYSVAL SYSVAL(QINACTMSGQ) VALUE('*ENDJOB') QSYS/CHGSYSVAL SYSVAL(QLMTDEVSSN) VALUE('1') QSYS/CHGSYSVAL SYSVAL(QLMTSECOFR) VALUE('1') QSYS/CHGSYSVAL SYSVAL(QMAXSGNACN) VALUE('3') QSYS/CHGSYSVAL SYSVAL(QMAXSIGN) VALUE('3') QSYS/CHGSYSVAL SYSVAL(QRMTSIGN) VALUE('*FRCSIGNON') QSYS/CHGSYSVAL SYSVAL(QRMTSRVATR) VALUE('0') QSYS/CHGSYSVAL SYSVAL(QSECURITY) VALUE('50') QSYS/CHGSYSVAL SYSVAL(QPWDEXPITV) VALUE('60') QSYS/CHGSYSVAL SYSVAL(QPWDMINLEN) VALUE(6) QSYS/CHGSYSVAL SYSVAL(QPWDMAXLEN) VALUE(8) QSYS/CHGSYSVAL SYSVAL(QPWDPOSDIF) VALUE('1') QSYS/RTVMSG MSGID(&LMTCHRTXTM) MSGF(QCPFMSG) MSG(&DFTVALUE) QSYS/CHGSYSVAL SYSVAL(QPWDLMTCHR) VALUE(&DFTVALUE) QSYS/CHGSYSVAL SYSVAL(QPWDLMTAJC) VALUE('1') QSYS/CHGSYSVAL SYSVAL(QPWDLMTREP) VALUE('2') QSYS/CHGSYSVAL SYSVAL(QPWDRQDDGT) VALUE('1') QSYS/CHGSYSVAL SYSVAL(QPWDRQDDIF) VALUE('1') QSYS/CHGSYSVAL SYSVAL(QPWDVLDPGM) VALUE('*NONE') QSYS/CHGUSRPRF USRPRF(QSYSOPR) PASSWORD(*NONE) QSYS/CHGUSRPRF USRPRF(QPGMR) PASSWORD(*NONE) QSYS/CHGUSRPRF USRPRF(QUSER) PASSWORD(*NONE) QSYS/CHGUSRPRF USRPRF(QSRV) PASSWORD(*NONE) QSYS/CHGUSRPRF USRPRF(QSRVBAS) PASSWORD(*NONE) QSYS/ENDPGM Figure 13.6: Sample program automatically configuring security (part 1 of 2).
You will be presented with a panel warning you of the potential problems with running this command:
-
Revoke public authority to objects:
This option changes to *EXCLUDE the public authority to programs and commands. To see what it actually does, retrieve the CL source to the QSECRVKP program in QSYS. Figure 13.7 shows the source retrieved from that program.

QSYS/PGM PARM(&LIBRARY) QSYS/DCL VAR(&IBMREG) TYPE(*CHAR) LEN(300) VALUE('Copyright, - 5799XDH, 5763SS1, 5716SS1 (C) Copyright IBM Corp. 1996. All Rights - Reserved; US Government Users Restricted Rights - Use, duplication or- disclosure restricted by GSA ADP Schedule Contract with IBM Corp. - Licensed Materials - Property of IBM. ') QSYS/DCL VAR(&IBMREG2) TYPE(*CHAR) LEN(300) QSYS/DCL VAR(&LIBRARY) TYPE(*CHAR) LEN(10) QSYS/DCL VAR(&APPID) TYPE(*CHAR) LEN(8) QSYS/DCL VAR(&PNLGRP) TYPE(*CHAR) LEN(20) VALUE('QGSECRPA *LIBL- ') QSYS/DCL VAR(&FUNC) TYPE(*CHAR) LEN(4) VALUE(' ') QSYS/DCL VAR(&ENTERVALUE) TYPE(*DEC) LEN(4) VALUE(100) QSYS/DCL VAR(&ERRCD) TYPE(*CHAR) LEN(8) VALUE(X'0000000000000000- ') QSYS/DCL VAR(&AUTIND) TYPE(*CHAR) LEN(1) QSYS/DCL VAR(&AUTS) TYPE(*CHAR) LEN(10) VALUE('*ALLOBJ ') QSYS/DCL VAR(&NUMAUTS) TYPE(*CHAR) LEN(4) VALUE(X'00000001') QSYS/DCL VAR(&CALLLVL) TYPE(*CHAR) LEN(4) VALUE(X'00000000') QSYS/MONMSG MSGID(CPF0000) QSYS/CHGVAR VAR(&IBMREG2) VALUE(&IBMREG) QSYS/CALL PGM(QSYS/QSYCUSRS) PARM(&AUTIND *CURRENT &AUTS - &NUMAUTS &CALLLVL &ERRCD) QSYS/IF COND(&AUTIND *EQ 'N') THEN(QSYS/SNDPGMMSG MSGID(CPFB304)- MSGF(*LIBL/QCPFMSG) MSGTYPE(*ESCAPE)) QSYS/CALL PGM(QSYS/QUIOPNDA) PARM(&APPID &PNLGRP -1 0 N &ERRCD) QSYS/MONMSG MSGID(CPF0000) EXEC(GOTO CMDLBL(SKIPUIM)) QSYS/CALL PGM(QSYS/QUIDSPP) PARM(&APPID &FUNC 'CONRPA' N &ERRCD) QSYS/CALL PGM(QSYS/QUICLOA) PARM(&APPID M &ERRCD) QSYS/IF COND(%BIN(&FUNC) *NE &ENTERVALUE) THEN(QSYS/RETURN) SKIPUIM: QSYS/GRTOBJAUT OBJ(&LIBRARY/ADDAJE) OBJTYPE(*CMD) USER(*PUBLIC) - AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/ADDCFGLE) OBJTYPE(*CMD) USER(*PUBLIC) - AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/ADDCMNE) OBJTYPE(*CMD) USER(*PUBLIC)- AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/ADDJOBQE) OBJTYPE(*CMD) - USER(*PUBLIC) AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/ADDPJE) OBJTYPE(*CMD) USER(*PUBLIC) - AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/ADDRTGE) OBJTYPE(*CMD) USER(*PUBLIC)- AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/ADDWSE) OBJTYPE(*CMD) USER(*PUBLIC) - AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/CHGAJE) OBJTYPE(*CMD) USER(*PUBLIC) - AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/CHGCFGL) OBJTYPE(*CMD) USER(*PUBLIC)- AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/CHGCFGLE) OBJTYPE(*CMD) - USER(*PUBLIC) AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/CHGCMNE) OBJTYPE(*CMD) USER(*PUBLIC)- AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/CHGCTLAPPC) OBJTYPE(*CMD) - USER(*PUBLIC) AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/CHGDEVAPPC) OBJTYPE(*CMD) - USER(*PUBLIC) AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/CHGJOBQE) OBJTYPE(*CMD) - USER(*PUBLIC) AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/CHGPJE) OBJTYPE(*CMD) - USER(*PUBLIC) AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/CHGRTGE) OBJTYPE(*CMD)- USER(*PUBLIC) AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/CHGSBSD) OBJTYPE(*CMD)- USER(*PUBLIC) AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/CHGWSE) OBJTYPE(*CMD) - USER(*PUBLIC) AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/CPYCFGL) OBJTYPE(*CMD)- USER(*PUBLIC) AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/CRTCFGL) OBJTYPE(*CMD) - USER(*PUBLIC) AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/CRTCTLAPPC) OBJTYPE(*CMD) - USER(*PUBLIC) AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/CRTDEVAPPC) OBJTYPE(*CMD) - USER(*PUBLIC) AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/CRTSBSD) OBJTYPE(*CMD) USER(*PUBLIC)- AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/ENDRMTSPT) OBJTYPE(*CMD) - USER(*PUBLIC) AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/RMVAJE) OBJTYPE(*CMD) USER(*PUBLIC) - AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/RMVCFGLE) OBJTYPE(*CMD) - USER(*PUBLIC) AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/RMVCMNE) OBJTYPE(*CMD) USER(*PUBLIC)- AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/RMVJOBQE) OBJTYPE(*CMD) - USER(*PUBLIC) AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/RMVPJE) OBJTYPE(*CMD) USER(*PUBLIC) - AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/RMVRTGE) OBJTYPE(*CMD) USER(*PUBLIC)- AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/RMVWSE) OBJTYPE(*CMD) USER(*PUBLIC) - AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/RSTLIB) OBJTYPE(*CMD) USER(*PUBLIC) - AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/RSTOBJ) OBJTYPE(*CMD) USER(*PUBLIC) - AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/RSTS36F) OBJTYPE(*CMD) USER(*PUBLIC)- AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/RSTS36FLR) OBJTYPE(*CMD) - USER(*PUBLIC) AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/RSTS36LIBM) OBJTYPE(*CMD) - USER(*PUBLIC) AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/STRRMTSPT) OBJTYPE(*CMD) - SER(*PUBLIC) AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/STRSBS) OBJTYPE(*CMD) USER(*PUBLIC) - AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(&LIBRARY/STRSBS) OBJTYPE(*CMD) USER(QPGMR) - AUT(*USE) QSYS/GRTOBJAUT OBJ(&LIBRARY/WRKCFGL) OBJTYPE(*CMD) USER(*PUBLIC)- AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(QSYS/QTIENDSUP) OBJTYPE(*PGM) USER(*PUBLIC) - AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(QSYS/QTISTRSUP) OBJTYPE(*PGM) USER(*PUBLIC) - AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(QSYS/QWTCTLTR) OBJTYPE(*PGM) USER(*PUBLIC) - AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(QSYS/QWTSETTR) OBJTYPE(*PGM) USER(*PUBLIC) - AUT(*EXCLUDE) QSYS/GRTOBJAUT OBJ(QSYS/QY2FTML) OBJTYPE(*PGM) USER(*PUBLIC) - AUT(*EXCLUDE) QSYS/CHGAUT OBJ(/) USER(*PUBLIC) DTAAUT(*RX) OBJAUT(*NONE) QSYS/ENDPGM
Figure 13.7: Sample program revoking public authority (part 1 of 4). -
Check object integrity (CHKOBJITG)
This option lists programs that have been changed without using a compiler. This can help you detect attempts to introduce a virus program to your system.
-
Related security tasks:
This option takes you to the Security menu. It is equivalent to keying GO SECURITY.
EAN: N/A
Pages: 245
- Chapter V Consumer Complaint Behavior in the Online Environment
- Chapter VI Web Site Quality and Usability in E-Commerce
- Chapter X Converting Browsers to Buyers: Key Considerations in Designing Business-to-Consumer Web Sites
- Chapter XII Web Design and E-Commerce
- Chapter XVIII Web Systems Design, Litigation, and Online Consumer Behavior