Validation
|
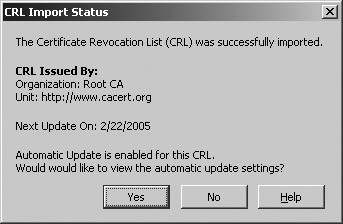
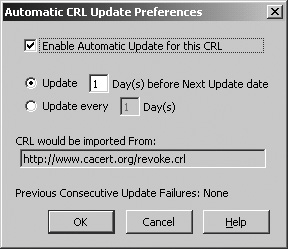
| As you've seen in this appendix, certificates use public and private keys and a standardized cryptographic procedure for identification. When you access another person's details or certificate information or a secure website that presents a certificate as his or her identification, you need to be able to validate the information to make sure that the certificate is accurate, that it hasn't expired, and that the CA is one that you trust to issue such a certificate. If there are failures along the way, or if there is reason to believe that the certificate may have been compromised, you can check the CA's Certificate Revocation List (CRL) to see if the certificate has been revoked"disavowed," if you likeby the CA. (This process is almost exactly like phoning a credit card company to see if the card that's being handed to you for payment is in fact authorized for use.) The Validation options are shown in Figure F-13. Figure F-13. The Options screen showing the Validation option.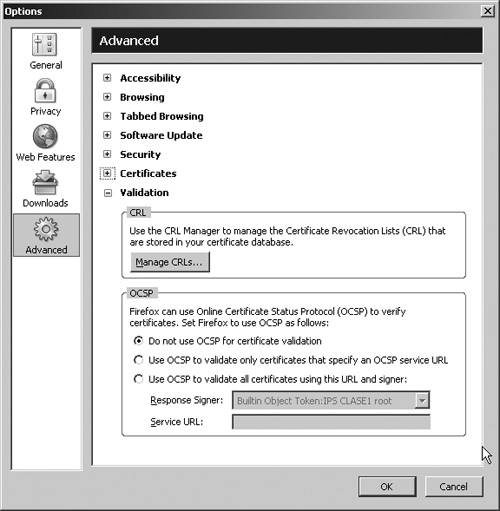 CRLFirefox checks CRLs automatically, you have to download and manage them yourself. Click Manage CRLs to display the Manage CRLs screen, shown in Figure F-14. Figure F-14. The Manage CRLs screen.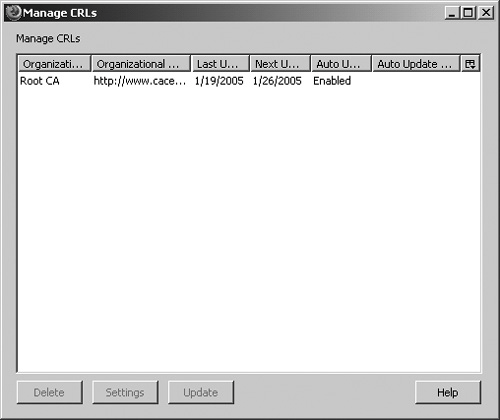 Although Figure F-14 shows a CRL already loaded, when you first load Firefox, there are no CRLs in the list. You can get CRLs from the websites for the CAs. When you download a CRL, Firefox displays a CRL Import Status screen like the one shown in Figure F-15. Figure F-15. The CRL Import Status screen. The CRL Import Status screen shows when the next update will be made to this CA's CRL and also allows you to tell Firefox to update the CRL automatically. When you click Yes, you see the Automatic CRL Update Preferences screen, shown in Figure F-16. Figure F-16. The Automatic CRL Update Preferences screen. In this screen, you can tell Firefox to update the CRL automatically and when and how often to update the CRL. Click OK to save the information. You need to repeat this process to get CRLs and configure the download options for each one. You can change a CRL's configuration by highlighting the CRL in the Manage CRLs screen and then clicking Settings to display the Automatic CRL Update Preferences screen. Make your changes and then click OK. To force an update, click Update. Firefox gets the current CRL and displays the download information on the CRL Import Status screen. OCSPSetting up CRLs can be a bit of a pest, particularly if you've got a lot of CAs in your list. You may also not have the very latest data. For example, if the next CRL is due out on Friday but a certificate is revoked on Tuesday, you may want a way to check the certificate directly against the latest information for the tightest validation security. OCSP (Online Certificate Status Protocol) lets you check a certificate's validity each time Firefox uses or views the certificate. Instead of checking against a downloaded CRL list, Firefox checks against the CRL list maintained at the CA's website. The default option is not to use OCSP. The Certificate Manager checks certificates to make sure that they haven't expired and that the issuing CA is recognized by Firefox and is trusted to issue that kind of certificate. If you select Use OCSP to validate only certificates that specify an OCSP service URL, Firefox checks a certificate's validity only if the certificate contains a URL for verification. Firefox again verifies that the certificate hasn't expired and that the CA is trusted to issue this kind of certificate, but it also uses the URL to see if the certificate is listed there as valid. For the tightest validation, select Use OCSP to validate all certificates using this URL and signer. Firefox verifies each certificate online every time. From the dropdown list for Response Signer, choose the appropriate certificate for OCSP. A correpsonding URL generally appears in Service URL; if not, you need to enter the URL yourself. This OCSP setting is fairly restrictive: a certificate is validated only if it is recognized with an appropriate OCSP response signed by the Response Signer certificate or by a certificate that chains to it in some way.
Digital certicates are a fascinating subject worth exploring if you're interested in security on the Internet. The best place to start is by reading some of the references available at http://www.cacert.org, http://www.dekart.com, and http://www.thawte.com. You can also experiment with different levels of digital certificates to see what effect they have. But if you prefer not to bother with all this, you can always leave things up to Firefox, and you'll be okay. |
|
EAN: 2147483647
Pages: 185