Some Implementations in Ciphers
Some Implementations in CiphersThe purpose of using ciphers is simply to provide confidentiality of data. The data that needs to be kept private could be stored on a hard disk or be transported through a network. The data is kept private to most people, but can be viewed by some other users (people or systems) that possess the key to decrypt the information. The key needs to always be kept in a secure location, accessed by only a select few. The problem with many systems is their inability to hide the implementations. For example, if a key is kept in a database and an application server accesses the database, the application server must also be secure. If the application server saves the password and user ID in a readable configuration file, such as XML, as some do, now the key's security is based on the security of the configuration file. Proprietary information and securityThere are a multitude of strategies and ways that organizations have tried to hide keys and mask the operations of ciphers. One clever way in the days of floppy disks was to cut a track and look for the cut in the track before granting access to software. Other ideas have been to mask the key or the password to retrieve the key in the offset of a device driver. Some ideas range from the complex to the very complex. Ciphers are simply a means of adding mathematical complexities to data. If everyone understood the complexities in great detail, another strategy would have to be formed . One strategy to avoid hackers has always been to implement software and only let a select few know how it is implemented. The term proprietary information has been derived from this notion. The same tactics need to be well thought out and applied to the security world. Security is simply a means of protecting one's information and assets. Another complexity of confusion that is added to cipher, in many cases, is to abstract out the operations of the data. By using Operating System internals to add to the complexity of ciphers, only those that understand these internals can understand where to get the keys and access to the ciphers. Before the Internet was popular, this scheme was quite secure because no one knew how to access it, but as people discovered how to access it, it became less and less secure. The lesson is that to keep something secure, simply don't let anyone know about it. There has been a lot of work in native libraries, Operating Systems, and device drivers to secure data with ciphers and accessing the data through the devices. This chapter talked a little about a CipherInputStream , but stream drivers and stream development with ciphers have been around for a long time; ciphers are used to encrypt data. The critical point always becomes the key storage. The X.509 certificate offers a way to protect keys by using third parties called Certificate Authorities (CA) to provide authentication to access the key in the certificate.
The idea behind X.509Public Key Infrastructure (PKI) is the idea behind the X.509, and the concept becomes to organize the entire company, or Internet, around security concepts. The cipher is just one component in the security concepts. Throughout the book I have mentioned several others, but the cipher is used to wrap data specifically for privacy. There are basically two storage mediums where data has the potential to be wrapped: the file system and the network system . You can consider (for security purposes) any data that can be stored on a hard drive, including databases and applications, as a file system. Any data that is communicated between two or more machines, again for security purposes, can be thought of as a network system. Some ways to secure data through a network are to use JSSE, OpenSSL, or even to provide an SPI layer using native libraries. Many organizations have issues implementing security techniques because people don't want to take the time to implement them. The organizations can make the security invisible to the user or provide a network interface that is invisible to the user. Figure 14-4 demonstrates a possibility to put a cipher layer in between applications and the network card. Another way to do this is to make sure that all the network applications are using JSSE and to have a JSSE infrastructure set up throughout the organization. 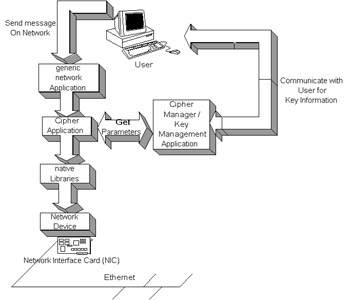 Figure 14-4: A native network cipher example
To provide data security on hard disks, a secure network file system could be used as displayed in Figure 14-5. The example in Figure 14-5 demonstrates a centralized server where sensitive information could be stored and managed. LDAP would be prime candidate for managing data in an organization in this manner. Protocols for authentication such as Kerberos and the Java GSS-API could be used to manage the authentication. The idea that I am trying to express is that the cipher is only as secure as the keys and the infrastructure. Use all of the security components together to complement the ciphers, and the ciphers can be managed to fulfill their roles and keep data private. The application of a cipher in most scenarios is not just a method call, but an infrastructure. One of the components used in Java to help keep the data private is the smart card. 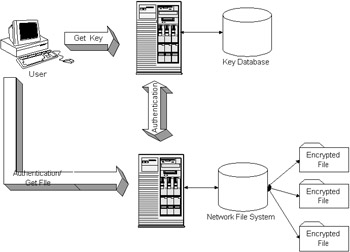 Figure 14-5: A secure network file system example
Java Security Solutions ISBN: 0764549286
EAN: 2147483647 Year: 2001
Pages: 222 Authors: Rich Helton, Johennie Helton
flylib.com © 2008-2017. If you may any questions please contact us: flylib@qtcs.net |