Section 1.7. The Blue E: The Achilles Heel of Windows Security
|
1.7. The Blue E: The Achilles Heel of Windows SecurityMicrosoft's decision to amalgamate its web browser and its operating system made it harder for the U.S. government to argue that the company should separate the two pieces of software, but the consolidation was technically unnecessary and has in fact been enormously problematic. If Microsoft wanted to provide a library that other third-party companies and programmers could use to web-enable their software, it could have done so without welding those libraries into every nook and cranny of Windows and its own software. Since everything is amalgamated, though, a vulnerability in the browser means that the operating system itself is threatened, and a problem in the OS can likewise affect the web browser. This has happened time and time again over the past several years, as Microsoft has been forced to issue security alert after security alert for attacks that can be triggered simply by reading email or listening to music using Windows Media Player.
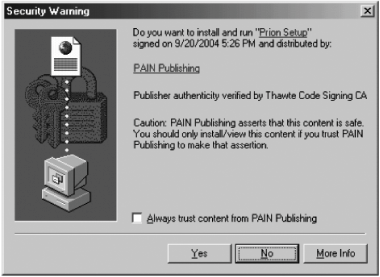
1.7.1. Sneaky, Malicious ActiveX ProgramsMicrosoft's ActiveX is another source of problems for IE. ActiveX is a technology that enables interactive programs, called controls, to load from web pages and run inside IE, with the same privilege levels as the user running the browser. In other words, if you're running as Administrator, and can therefore do whatever you want on your PC, any ActiveX control you load in IE has full access to your PC as well. Microsoft's solution? ActiveX controls must be marked "Safe For Scripting," which means that the ActiveX control is supposedly safe to run on your PC. Ah, but who determines that the ActiveX control is safe? Why, the guy who programmed the control! Imagine that late one dark night you get a knock on your door. "Who is it?" you ask. "The police," says the voice outside. "What's your proof?" you ask. "Oh, I'm looking at my badge, and it clearly says I'm a policeman. So let me in!" says the voice. You gonna let that person in? Take a look at [click here]. This fictional example is the kind of apparently safe, yet fraudulent, prompt that a hacker might display in IE when you visit a web page that is trying to load a dangerous ActiveX control onto your computer.
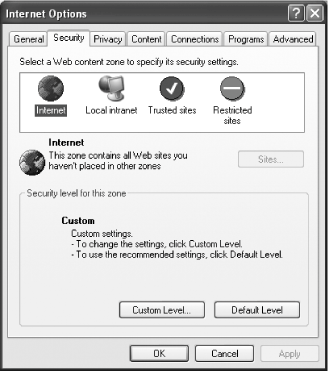
PAIN Publishing says that Prion Setup is safe. They assert it strongly. Heck, you can even check a box saying that you will always trust them. Go ahead and press Yes. Prion Setup installs on your PC, and now your computer has Mad Cow Disease. Oops. That's the situation you're in with ActiveX controls. If an ActiveX control says it's safe, and you run it, it can do anything on the computer that you can. Sure, Windows XP's Service Pack 2 now prevents web sites from automatically installing ActiveX controls on your PC. However, by forcing ActiveX as the only solution for plug-ins and a major solution for other interactive programs, Microsoft has painted themselves into a corner, as the new SP2 settings will probably cause a lot of web sites to break due to reduced functionality. Furthermore, SP2 will still allow users to install malicious ActiveX controls if they're not careful, and, even worse, only XP users benefit from the new changes. Millions and millions of computers are still running Windows 2000, NT, ME, 98, and even 95, and those machines are still extremely vulnerable. 1.7.2. IE's Approach to SecurityWhen Microsoft is pushed on its security record, it falls back on its notion of security zones, first introduced in IE 4, which you can see in Figure 1-8.
Essentially, all web sites are placed into one of four zones:
By default, all unplaced web sites are in the Internet zone, but you can specify that specific sites should have their permissions set by other zones. Out of the box, IE has default permissions set up for each zonethe settings for Trusted sites are far more lenient than for sites in the Internet zone, for example, while Restricted sites are allowed to do very, very little. Zones have a couple of problems. First, Microsoft assumes that the average user is going to know what a zone is, and that he will take the trouble to insert a URL (assuming he even knows what a URL is) into the proper zones. Riiiight. Zones are too complicated for most folks to figure out and use. Other browsers make it real simplea feature is either on or offbut while IE allows you to turn a feature on or off, it often adds a third choice, prompt, and you need to make your choices about all the features in 4 different zones, so 25 choices are actually 100. On top of that, if a bad guy emails you a web page and gets you to open it, it will run in the hidden fifth zone, My Computer or Local, which by default has almost all permissions enabled. In other words, that web page will have pretty much free rein on your computer. Uh-oh.
Worse than bad security is the time it can take Microsoft to fix holes when they're found. Secunia, a security research company, reports 70 advisories for IE 6 in 2003-2004, 35% of which are still unfixed at the time of this writing (http://secunia.com/product/11/ ). Remember the Download.Ject vulnerability that I discussed at the beginning of this chapter, in which IE users faced back doors and keyloggers being installed on their computers by compromised web servers? It was actually a bit more complicated than I explained then. SecurityFocus columnist Tim Mullen identified the real cause of that mess: "multiple vulnerabilities in IE, at least one spanning back months, which have remained un-patched by Microsoft" (http://www.securityfocus.com/columnists/251). Microsoft's initial fix came out over a week after the attack was discovered, but within a day or two security researchers had announced that its solution was ineffective and that IE was still vulnerable. It wasn't until a month later that Microsoft finally released a patch that solved the problem. So, in other words, while IE users remained vulnerable to a serious hole in their web browsers that exposed them to great harm, it took the most powerful software company in the worlda business employing more than 30,000 programmersover a month to fix a severe problem with its browser. Clearly, IE has a serious problem with security. One argument Microsoft and others use in an attempt to blunt criticism of IE's security record has to do with its ubiquitynamely, they claim that IE is attacked constantly because it is in such widespread use, and that if a different browser had IE's vast share of the market, that browser would also be the continual target of security attacks. This argument is problematic. First, the assertion that ubiquity, or near ubiquity, automatically results in security attacks that expose vulnerabilities is quite simply untrue. For example, Apache is the world's most widely used web server software (with 68% of the market compared to Microsoft's 21%), and has been for several years, yet it has seen far fewer serious security holes and attacks than Microsoft's web server. Second, the real reason that IE (and other Microsoft software) is so often attacked is because these attacks are so easy. Microsoft tends to allow marketing goals to govern the direction of software engineeringhence the decisions to tie the browser and the operating system together (not for a good technical reason, but instead to push IE and score points during the antitrust trial), and the constant rush to add more and more features to its software without first making sure that everything is locked down as much as possible. This is well known to those in the technology field as "Microsoft's dirty little secret," but it's a secret only to the wider public, who by and large have no knowledge of this consistent behavior on the part of Microsoft.
Microsoft has said that it is attempting to change, and that security will become its highest priority as it goes forward. So far, the results have been mixedand that's being kind. Security vulnerabilities continue to be discoveredand exploited by hackerson a regular basis, while Microsoft's not-so-subtle message continues to be, "Upgrade! Upgrade! Upgrade to Windows XP, and then upgrade to Longhorn when that gets released in a few years! Upgrade, and all will be fixed!" This attitude conveniently ignores the fact that millions of people and businesses find older versions of Windows, which they paid good money for, otherwise satisfactoryespecially since they could always download a free upgrade to the latest version of IE to acquire security patches as new holes were exposed. However, as discussed earlier in "No More Free Lunch," that's no longer going to be an option for IE users. Surely there has to be a better way. Are we stuck with IE, and now with needing to purchase an entire operating system in order to upgrade it so we can avoid its security holes? Is there no alternative? |
|
EAN: N/A
Pages: 93