Overview of EIGRP in an Enterprise Network EIGRP is an enhanced version of IGRP, hence the name . It uses the same distance vector technology as IGRP. The changes were effected in the convergence properties and the operating efficiency of the protocol. EIGRP has some characteristics similar to those of a link-state routing protocol. Therefore, it is sometimes referred to as a hybrid routing protocol , although Cisco calls it an advanced distance vector protocol . EIGRP is an efficient, although proprietary, solution to networking large environments because it scales well. Its ability to scale is, like OSPF, dependent on the design of the network. EIGRP Terminology To understand how EIGRP works, you must be familiar with the terminology. Table 13-2 defines the main components and concepts. Table 13-2. Terminology for EIGRP for IP | Term | Definition | | Neighbor | A router running EIGRP that is directly connected. | | Neighbor table | A list of every neighbor, including the IP address, the outgoing interface, the holdtime, smooth round-trip time (SRTT), and uptime, or how long since the neighbor was added to the table. This table is built from information on Hellos received from adjacent routers (neighbors). | | Route table | The routing table, or list of available networks and the best paths. A path is moved from the topology table to the routing table when a feasible successor is identified. | | Topology table | A table that contains all the paths advertised by neighbors to all the known networks. This is a list of all the successors, feasible successors, the feasible distance, the advertised distance, and the outgoing interface. DUAL acts on the topology table to determine successors and feasible successors by which to build a routing table. | | Hello | Messages used to find and maintain neighbors in the topology table. They are sent periodically and are sent unreliably. | | Update | An EIGRP packet containing change information about the network. It is sent reliably. It is sent only when there is a change in the network to affected routers: -
When a neighbor first comes up -
When a neighbor transitions from active to passive for a destination -
When there is a change in calculated metric for a destination | | Query | Sent from the router when it loses a path to a network. If there is no alternate route (feasible successor), it will send out queries to neighbors inquiring whether they have a feasible successor. This makes the route state change to active. The queries are sent reliably. | | Reply | A response to the query. If a router has no information to send in a reply, it will send queries to all its neighbors. A unicast is sent reliably. | | ACK | A Hello packet with no data that is an acknowledgment of packets sent reliably. | | Holdtime | Value set in the Hello packet. It determines how long the router waits for Hellos from a neighbor before declaring it unavailable. This information is held in the neighbor table. | | Smooth Round-Trip Time (SRTT) | The time that the router waits after sending a packet reliably to hear an acknowledgment. This is held in the neighbor table and is used to calculate the RTO. | | Retransmission Timeout (RTO) | Timer calculated in reference to the SRTT. RTO determines how long the router waits for an ACK before retransmitting the packet. | | Reliable Transport Protocol (RTP) | Mechanism used to determine requirements that the packets be delivered in sequence and guaranteed . | | Diffusing Update Algorithm (DUAL) | An algorithm performed on the topology table to converge the network. It is based on a router detecting a network change within a finite time, with the change being sent reliably and in sequence. As the algorithm is calculated simultaneously , in order, and within a finite time frame on all affected routers, it ensures a loop-free network. | | Advertised distance (AD) | The cost of the path to the remote network from the neighbor (the metric from the next -hop router). | | Feasible distance (FD) | The lowest -cost distance (metric) to a remote network. | | Feasible condition (FC) | When a neighbor reports a path cost (AD) that is lower than the router's FD to a network. The neighbor's (next-hop router's) path has a lower metric than the router's path. | | Feasible successor (FS) | The neighbor reporting the AD that is lower than the router's FD becomes the feasible successor. The next-hop router that meets the FC. | | Successor | The next-hop router that passes the FC. It is chosen from the FSs as having the lowest metric to the remote network. | | Stuck in Active (SIA) | State reached when a router has sent out network packets and is waiting for ACKs from all its neighbors. The route is active until all the ACKs have been received. If they do not appear after a certain time, the router is SIA for the route. | | Query scoping | Network design to limit the scope of the query range, that is, how far the query is allowed to propagate in search of a feasible successor. This is necessary to prevent SIA, which can cause multiple problems for the network. | | Active | Route state when there is a network change, but after examining the topology table, no FS is found. The route is set to active mode, and the router queries its neighbors for alternative routes. | | Passive | An operational route is passive. If the path is lost, the router examines the topology table to find an FS. If there is an FS, it is placed in the routing table; otherwise , the router queries its neighbors, sending the route into active mode. | Understanding EIGRP Features and Advantages The goal of EIGRP is to solve the scaling limitations that IGRP faces, using the distance vector technology from which it grew. EIGRP increases the potential growth of a network by reducing the convergence time. This is achieved by the following features: -
DUAL -
Loop-free networks -
Incremental updates -
Multicast addressing for updates -
Advanced distance vector protocol -
Loop-free routing tables -
Support for different topologies -
Rapid convergence -
Reduced bandwidth use -
Protocol independence at Layer 3 -
Compatibility with IGRP -
Easy configuration -
Use of a composite metric -
Unequal-cost load balancing A full understanding of the concepts and operation of EIGRP will aid you in the design, implementation, and maintenance of EIGRP networks and will definitely help you pass an exam on the subject. The following sections describe each of these features in more detail. DUAL DUAL is one of the main features of EIGRP. It diffuses the routing computation over multiple routers. A more detailed discussion of DUAL is provided in the section "Components of EIGRP." Loop-Free Networks The DUAL algorithm is used to ensure a loop-free network. The calculation of an FS means that the backup route is downstream from the router. The FS is chosen only because it has a lower metric to the destination route than that reported by the router. This prevents any routes that lead back to the router from being chosen, thus eliminating loops . Incremental Updates EIGRP sends nonperiodic, partially bounded updates. That is, they are sent whenever there is a change to be reported and not at regular intervals. When a network change is made, the updates include only those changes that are needed to update the affected routers. Multicast Addressing for Updates EIGRP uses an RTP that guarantees delivery. This is essential when the routing updates are not sent periodically; otherwise, if the receiving router is not expecting an update, it cannot realize that an update was missed, indicating a network problem. Updates are therefore sent using a reliable multicast. The address is the reserved class D address, 224.0.0.10. When the neighbor receives a multicast, it acknowledges receipt of the packet with an unreliable unicast. Advanced Distance Vector Protocol EIGRP has solved many of the problems inherent in distance vector protocols, which prevent them from effectively supporting large networks. The features of distance vector technology that prohibit network growth include the use of broadcasts and hop count, neither of which is used by EIGRP. Other characteristics that advance EIGRP beyond an ordinary distance vector protocol come from its status as a classless routing protocol. Without the use of areas, EIGRP allows summarization anywhere in the network. Summarization reduces the need for network resources. Because the classless protocols send the subnet mask with the update, this also means that classless protocols support discontiguous networks and, of course, variable-length subnet mask (VLSM). Loop-Free Routing Tables The criteria for selecting the primary and backup routes in the topology table and the routing table ensure that the routes offered are loop-free. The primary route that is placed in the routing table is chosen for the lowest metric, which means it cannot be looped. The backup route (feasible successor) is dependent on the downstream router (next hop advertising the alternative route) advertising a lower cost for the route than the one stored in the routing table. This ensures that the backup route does not loop back through the router. Support for Different Topologies EIGRP, as a new protocol, has been able to anticipate recent topologies, such as NBMA clouds. There is no complex configuration required for these topologies, though additional configuration is available for tuning the update operation of EIGRP. Rapid Convergence The use of the DUAL algorithm stores not only the best path to the destination, but also the close contenders. If a network fails, the router can immediately switch to the alternate route. If there are no alternative routes, then the router will query neighbors to see whether they have a path to the destination. Reduced Bandwidth Use Using multicast and unicast addressing to send and acknowledge updates restricts the potential use of both bandwidth and the other system's CPU to the essential requirements. EIGRP also uses only incremental updates, as opposed to periodic updates. Protocol Independence at Layer 3 EIGRP functions as the routing protocol for IP, AppleTalk, and IPX. A different routing table is maintained for each Layer 3 protocol. EIGRP will automatically redistribute IPX RIP, AppleTalk RTMP, and IP IGRP within the same autonomous system. Compatibility with IGRP Because it grew out of IGRP, EIGRP is backward-compatible with IGRP. This allows for seamless transitions to EIGRP and support for older, smaller networks that have neither the need nor the capability to upgrade. EIGRP automatically redistributes IP routes learned into the IGRP process as long as the autonomous system number used to configure the processes is the same. Easy Configuration Because EIGRP was designed for the hardware on which it runs, the protocol not only is tuned for efficiency, but also is simple and straightforward to configure. Another benefit is that EIGRP has fewer design constraints than OSPF; for example, EIGRP supports point-to-point, in addition to NBMA point-to-point and multipoint. EIGRP requires no additional configuration other than tuning the bandwidth utilization, if desired. Use of a Composite Metric EIGRP uses the same metric as IGRP (bandwidth and delay as the default), though EIGRP has expanded the metric to 32-bit, allowing for greater scaling and granularity. An intelligent metric will select the shortest path. Unequal-Cost Load Balancing Unequal-cost load balancing allows all links to a destination to be used to carry data without saturating the slower links. NOTE A broadcast domain identifies devices that are within the same Layer 2 domain. Although they might not be directly connected to the same physical cable, if they are in a switched environment, from a logical Layer 2 or Layer 3 perspective, they are on the same link. If a broadcast is sent out, all the devices within the broadcast domain will hear the message and will expend resources determining whether it is addressed to them. A Layer 3 device is a broadcast firewall in that a router does not forward broadcasts.
Components of EIGRP Cisco identifies four main components of EIGRP: The following sections describe each of these components in more detail. Protocol-Dependent Modules EIGRP functions as the routing protocol for IP, AppleTalk, and IPX. A different routing table is maintained for each Layer 3 protocol. RTP EIGRP uses both multicast and unicast addressing. Some of these packets are sent reliably using RTP, meaning that they require an acknowledgment. These packets are also sent with sequence numbers to make the transmission of data reliable. Hellos and ACKs do not require acknowledgement , but the incremental updates cannot be anticipated. Therefore, the update, query, and reply packets must be acknowledged by the receiving neighbor or the packet is retransmitted up to 16 times. Neighbor Discovery and Recovery EIGRP operates between neighbors that share routing tables and information about the state of their connections. In this way, the routing protocol localizes as much information as possible, reducing the bandwidth and CPU requirements of the network and speeding up convergence. DUAL EIGRP uses DUAL to maintain the network databases. It selects the shortest path to a destination and then maintains a backup path if available, making network convergence almost instantaneous. Using the terminology for EIGRP, the term successor refers to the path to a destination. The successor is chosen using DUAL from all of the known paths or feasible successors to the end destination. If the selected path dies for any reason, an alternative route is chosen from the feasible successors. If a feasible successor is found, the route stays in passive mode, and there is no disruption to the network. However, if an alternative path is not immediately available, the router queries its neighbors, placing the route in active mode. The Operation of EIGRP One of the main strengths of EIGRP is that it limits the scope of network computation, keeping all knowledge of network change as local as possible. EIGRP is a protocol that works on a "need to know" basis. Even if the computation of the network is local, the router must know about the entire network. The explanation of the routing protocol is given through the viewpoint of one router. Once you understand the network communication between the routers running EIGRP, the operation of EIGRP becomes clear; the concepts and terms are placed in context. This facilitates your understanding of the subject; rote memorization is no longer necessary. There are three main tables in EIGRP: -
The neighbor table -
The topology table -
The routing table Creating the Neighbor Table The neighbor table is maintained by means of the Hello protocol, a small packet sent out to dynamically learn of other routing devices that are in the same broadcast domain. It informs neighbors that connections are live and active and keeps track of all the packets sent between the neighbors. This table is therefore maintained not only by the Hello protocol, but also by actively monitoring all traffic between the directly connected systems. Each Layer 3 protocol supported by EIGRP (IP, IPX, and AppleTalk) has its own neighbor table, which makes sense because the neighbor, topology, and routing tables differ greatly. Although all the information is held in one table, the different EIGRP processes all have to access the same table, which complicates and slows down the lookup. The Contents of the Neighbor Table The neighbor table includes the following information: -
The address of the neighbor. -
The interface through which the neighbor's Hello was heard . -
The holdtime, or how long the neighbor table waits without hearing a Hello from a neighbor, before declaring the neighbor unavailable and purging the database. This is three times the value of the Hello timer by default. -
The uptime, or how long since the router first heard from the neighbor. -
The sequence number. The neighbor table tracks all the packets sent between the neighbors. It tracks both the last sequence number sent to the neighbor and the last sequence number received from the neighbor. Although the Hello protocol is a connectionless protocol, other protocols used by EIGRP are connection-oriented. The sequence number is in reference to these protocols. -
SRTT. This calculates the RTO. This is the time in milliseconds that it takes a packet to be sent to a neighbor and a reply to be received. -
RTO. This states how long the router will wait on a connection-oriented protocol without an acknowledgment before retransmitting the packet. If the original packet that was unacknowledged was multicast, the retransmitted packets will be unicast. -
The number of packets in a queue. This is a means by which administrators can monitor congestion on the network. Becoming a Neighbor The EIGRP Hello protocol uses a multicast address of 224.0.0.10, and all routers periodically send Hellos. On hearing Hellos, the router creates a table of its neighbors. The continued receipt of these packets maintains the neighbor table. If a Hello from a known neighbor is not heard within a predetermined amount of time, as stated in the holdtime, the router will decide that the neighbor is no longer operational and will take the appropriate action. The holdtime is set at the default of three times the Hello timer. Therefore, if the router misses three Hellos, the neighbor is declared dead. The Hello timer on a LAN is set to 5 seconds; the holdtime, therefore, is 15 seconds. On a WAN link, the Hello timer is 60 seconds, and the holdtime correspondingly is 180 seconds. To become a neighbor, the following conditions must be met: -
The router must hear a Hello packet or an ACK from a neighbor. -
The autonomous system number in the packet header must be the same as that of the receiving router. -
The neighbor's metric settings must be the same as that of the receiving router. Figure 13-1 demonstrates building the neighbor table. Figure 13-1. Building the Neighbor Table 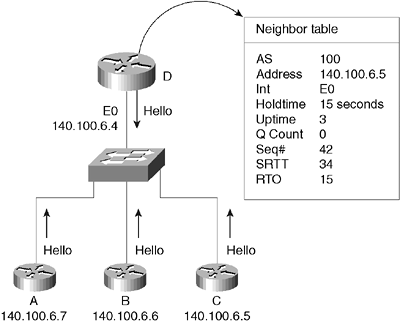 Creating the Topology Table After the router knows who its neighbors are, it is able to create a database of feasible successors. The neighbors and available feasible successors are held in the topology table. Contrary to popular belief, the topology table has a record of all known network routes within the organization, not simply the feasible successors and successors. The other routes are referred to as possibilities . The topology table in EIGRP manages the selection of routes to be added to the routing table. The topology table includes the following information: -
Whether the route is passive or active. -
That an update has been sent to the neighbors. -
That a query packet has been sent to the neighbors. If this field is positive, at least one route will be marked as active. -
If a query packet has been sent, another field will track whether any replies have been received from the neighbors. -
That a reply packet has been sent in response to a query packet received from a neighbor. -
The remote networks. -
The prefix or mask for the remote network. -
The metric for the remote network, the FD. -
The metric for the remote network advertised by the next logical hop, the AD. -
The next hop. -
The outgoing interface to be used to reach the next logical hop. -
The successors, the path to the remote network stated in hops. The table is built from the update packets that are exchanged by the neighbors and by replies to queries sent by the router. Replies are sent in response to queries, inquiring about suspect routes. The queries and responses used by EIGRP for DUAL are sent reliably as multicasts using RTP, which was created by and is proprietary to Cisco. If a router does not hear an acknowledgment within the allotted time, it retransmits the packet as a unicast. If there is no response after 16 attempts, the router marks the neighbor as dead. Each time the router sends a packet, RTP increments the sequence number by one. The router must hear an acknowledgment from every router before it can send the next packet. The capability to send unicast retransmissions decreases the time that it takes to build the tables. When the router has an understanding of the network, it runs DUAL to determine the best path to the remote network. The result is entered into the routing table. Maintaining the Topology Table The following three reasons might cause a topology table to be recalculated: -
The router hears a change when a new network is available because of one of the following reasons: -
- The topology table receives an update stating that there is a new remote network. -
- The interface for a directly connected EIGRP network comes online. -
The router changes the successor in the topology table and routing table in these circumstances: -
- The topology table receives a reply or a query from a neighbor. -
- There is local configuration of a directly connected interface to change the cost of the link. -
The router hears a change from a neighbor when a network has become unavailable because of one of the following reasons: -
- The topology table receives a query, reply, or update stating that the remote network is down. -
- The neighbor table does not receive a Hello within the holdtime. -
- The network is directly connected, and the router senses a loss of carrier. Figure 13-2 illustrates the traffic flow seen when a router loses a direct connection. Figure 13-2. Maintaining the Topology Tablethe Traffic Flow 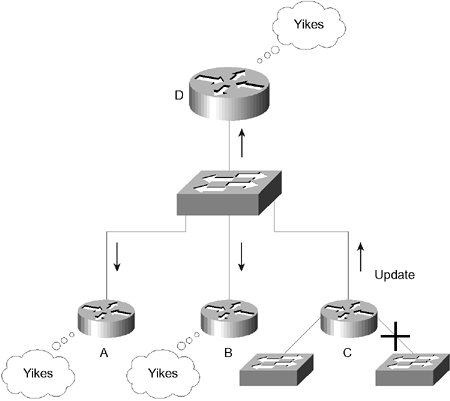 Just as the neighbor table tracks the receipt of the EIGRP packets, the topology table records the packets that have been sent by the router to the neighbors. It also identifies the status of the networks in the table. A healthy network is marked as passive ; it is labeled as active if the router is attempting to find an alternative path to the remote network that is believed to be down. Because the routing table is built from the topology table, the topology table must have the information required by the routing table. This includes the next hop, or the address of the neighbor that sent the update with that network. The routing table also calculates the metric to the remote network. Adding a Network to the Topology Table Figure 13-3 shows the topology for this section. Figure 13-3. EIGRPUpdating the Topology Table with a New Router 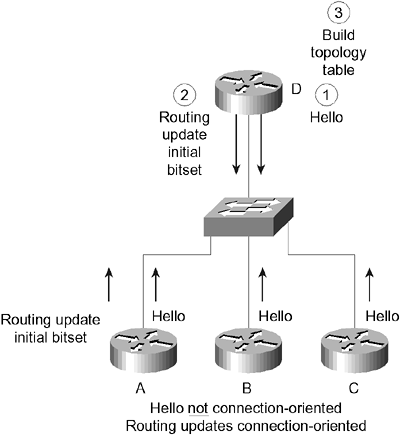 Imagine an access layer router (Router A) that connects to a new network. The administrator has connected and configured another Ethernet interface to service a department that has moved into the building. The following list describes how the new network is propagated to all the routers in the EIGRP autonomous system: -
As soon as Router A becomes aware of the new network, it starts to send Hello packets out of the new interface. No one answers because this is an access router giving connectivity to the workstations and other end devices. There are no new entries in the neighbor table because no neighbors have responded to the Hello protocol. There is a new entry in the topology table, however, because this is a new network. -
EIGRP, sensing a change, is obliged to send an update to all its neighbors, informing them of the new network. The updates set a bit in the flag field of the update header. The initial bit shows that the update includes route entries that are the first in the setup of a new neighbor relationship. These updates are tracked in the topology table and the neighbor table because the updates are connection-oriented and the acknowledgments from the neighbors must be received within a set timeframe. Router A, having added the network to its topology table, adds the network to its routing table. The network will be marked as passive because it is operational. Router A's work is done. Router D's work has just begun. Acting at the distribution layer, Router D is the router that connects Routers A, B, and C to the rest of the building. Its neighbors are routers on each floor and the routers in the other buildings . -
On hearing the update from Router A, Router D updates the sequence number in the neighbor table and adds the network to the topology table. It calculates the FD and the successor to place in the routing table. It is then in a position to send an update to all of its neighbors, except for Routers A, B, and C. It is obeying the split horizon rule here. Routers B and C are updated in the same manner and at the same time as Router D. The next section describes the process for removing a router or path from the topology table. Removing a Path or Router from the Topology Table The process of removing a path or router from the topology table is far more complex and gets to the crux of EIGRP. The following process uses Figure 13-3 and focuses on Router D: -
If a network connected to Router A is disconnected, Router A updates its topology and routing table and sends an update to its neighbors. -
When Router D receives the update, it updates the neighbor table and the topology table. -
As a router, D is programmed to find an alternative route to the remote network. It examines the topology table for alternatives. Because there is only one path to the remote network, no alternatives are found. -
The router then sends out a query to its neighbors requesting that they look in their tables for paths to the remote network. The route is marked active in the topology table at this time. -
The query is tracked, and when all the replies are in, the neighbor and topology tables are updated. -
DUAL, which starts to compute as soon as a network change is registered, runs to determine the best path, which is placed in the routing table. -
Because no alternative route is available, the neighbors reply to the query stating that they have no path. -
Before they respond, they query their own neighbors; in this way, the search for an alternative path extends or diffuses throughout the organization. -
When no router can supply a path to the network, all the routers remove the network from their routing and topology tables. The next section describes when a neighbor does have an alternative route. Finding an Alternative Path to a Remote Network When the path to a network is lost, EIGRP goes to a lot of trouble to find an alternative path. This process is one of the major benefits of EIGRP. The method that EIGRP uses to find alternative paths is very reliable and very fast. Figure 13-4 illustrates the steps in this section. In the figure, the routers that are participating in the selection process are circled. Figure 13-4. Campus Topology Map Showing Alternative Path Selection 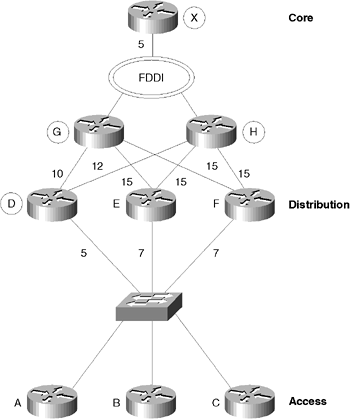 NOTE The metric shown in Figure 13-4 has been simplified for the purposes of this example.
The following list describes the process after Router G goes offline: -
Router D marks the routes that were reached by sending the traffic to Router G. -
Router D looks in the topology table, which has every network and path of the network, to determine whether there is an alternative route. It is looking for an FS. -
An FS is determined by a clearly defined equation. The topology table has an AD and an FD listed for every route or successor. This comprises the metric by which the route was selected. -
Router D adds the alternative route to Router X via Router H, found in the topology table, without moving into active mode because the AD is still less than the original FD. The AD is 5; the original FD was 15. It needs to send updates to its neighbors because the distance has changed. -
If the router did not have an FS, it would have placed the route into an active state while it actively queried other routers for an alternative path. -
After interrogating the topology table, if a feasible route is found, the neighbor replies with the alternative path. This alternative path is then added to the topology table. -
Next, in the last steps of DUAL, the routing table is updated. -
The network is placed back into a passive state as the router returns to the normal forwarding and maintenance of EIGRP tables until the next change in the network. -
If a neighbor that has been queried has no alternative path or FS, it places the network into active mode and queries its neighbors. -
If no answer is heard, the messages are propagated until they hit a network or autonomous system boundary. When the router sends a query packet, it is recorded in the topology table. This is to ensure a timely reply. If the router does not hear a reply, the neighbor is removed from the neighbor table; all the networks held in the topology table for that neighbor are seen as suspect, and the networks are queried. Occasionally, because of slow links and burdened routers in a large network, problems can occur. In particular, a router might not receive a reply from all the queries that it sent out. This leads to the route being declared SIA; the neighbor that failed to reply is removed from the neighbor table, and DUAL assumes a reply was received, giving an infinite metric. NOTE SIA can take minutes to resolve. First, it is important to discover if neighbors are consistently failing to answer the query and why. This failure is due to a resource problem either on the router or on the link to the router. It is always better to redesign the network. Summarization and distribution (route filters) both reduce the scope of the query range. This subject is well documented in the Cisco White Paper "EIGRPEnhanced Interior Gateway Routing Protocol" available at the Cisco Web site, Cisco.com.
Creating the Routing Table The routing table is built from the topology table after DUAL has been run. The topology table is the foundation of EIGRP: This is where all the routes are stored, even after DUAL has been run. It is in the routing table that the best paths are stored and accessed by the routing process. Once the tables have been built, the router can make routing decisions. EIGRP Metrics The metrics used in EIGRP are very similar to those of IGRP. The main difference is that the result of the calculation is held in a 32-bit field. This means that the decision can be much finer or more detailed. The DUAL algorithm uses this metric to select the best path or paths to a destination. The computation is performed on paths held in the topology table to identify the best path to place into the routing table. Up to six paths can be held for one destination, and there can be three different types of paths. These three path types are described in Table 13-3. Table 13-3. EIGRP Routing Types | Route Type | Description | | Internal | Internal paths to the autonomous system | | Summary | Internal paths that have been summarized | | External | External paths to the autonomous system that have been redistributed into this EIGRP autonomous system | The metric is the same composite metric used by IGRP, with the default calculated from bandwidth and delay. Although it is possible to change the metric, this must be done only with great care and consideration to the network design. Any changes made must be effected on every router in the EIGRP autonomous system. The equation for the default metric used is this: metric = [(10000000 smallest bandwidth kbps) + sum of delays] * 256 Table 13-4 explains the metric values. Table 13-4. EIGRP Metric Values | Metric Symbol | Metric Value | Description | | K1 | Bandwidth | Selects the smallest bandwidth media between the source and destination hosts . The equation used is [10000000 bandwidth kbps] * 256. | | K2 | Loading | Based on the statistics held at the outgoing interface and recorded in bits per second. | | K3 | Delay | The delay calculated on the outgoing interface. The value used is the cumulative total of the delay on all the interfaces between the hosts. The delay is measured in units of 10 ms to 168 seconds. A delay of all 1s in the 32-bit field means the network is unreachable. | | K4 | Reliability | Based on the statistics held on the outgoing interface gained from keepalives and exponentially averaged over five minutes. | | K5 | MTU | The smallest MTU found on an interface along the route. This value is included although it has not been used as part of the metric calculation. | The default for the K constants are K1 = 1, K2 = 0, K3 = 1, K4 = 0, K5 = 0 If K5 = 0, the composite metric is calculated using the following formula: metric = [K1 * bandwidth(K2 * bandwidth)(256-load) + K3 * delay] If K5 is not 0, the added formula is used: metric = metric * [K5(reliability + K4)] Given the overall understanding of how EIGRP works, the next section considers the topology table and its components, which will help explain the details of EIGRP operation. The Topology Table and the DUAL Finite-State Machine DUAL is responsible for maintenance of the topology table and the creation of the routing table. The topology table records the metric as received from the advertising router, or the next hop. It then adds the cost of getting to that neighbor, the one that is advertising the route. The cost to the destination network from the advertising router, plus the cost to that router, equals the metric to the destination network from the router. The metric or cost from the neighbor advertising the route is known as the advertised distance ( AD ) . The metric or cost from the router that is determining the metric or the local router is referred to as the feasible distance ( FD ) . If the AD is less than the FD, the next-hop router is downstream and there is no loop. Put simply: The downstream neighbor or next hop must be closer to the destination. This is fundamental to EIGRP. Figures 13-4 and 13-5, shown earlier in this chapter, illustrate these distances. Note that the metric shown in these figures has been simplified for the purposes of this example. Figure 13-5. The Use of Feasible and Advertised DistancePassive Mode 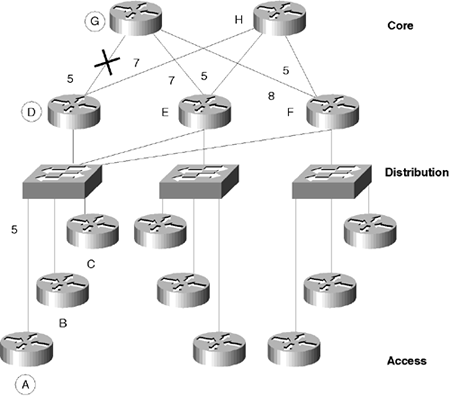 Updating the Routing Table in Passive Mode with DUAL DUAL determines whether there is an acceptable route in the topology table to replace the current path in the routing table. In EIGRP terms, this is replacing a successor in the routing table with a feasible successor from the topology table. Use the network in Figure 13-5 as an example. The following list explains the figure with the metrics and actions that EIGRP takes in determining the path: -
The FD from Router A to Router G is 10 (A to D to G). -
The AD from Router A to Router G is 5 (advertised from Neighbor D). -
Because 10 > 5, then FD > AD. This means that the FD is a feasible condition (FC), allowing it to become an FS. If you follow the diagram, it is very straightforward and less algebraic. -
If the link between Router D and Router G were down, Router A would look in its topology table. -
The alternative routes through Router A to D to H to E to G have an AD of 19 (7 + 5 + 7). -
Because 19 is greater than the original FD of 10, it does not qualify as an FS. -
The path through Router D to H to F to G has an AD of 20 and cannot be an FS. -
The path through Router A to E to G has an AD of 7, however, which is less than the original 10. Therefore, this is an FS and can be replaced as a route without Router A changing from passive to active mode. -
The original topology table would show that the primary route (successor) is Router D, while the backup route (FS) is Router E. After the link between D and G dies, the routing table would be updated from the topology table while the route remains passive. The following section illustrates what happens when the topology table is interrogated and no feasible route is found. Updating the Routing Table in Active Mode with DUAL When no alternative route is found in the routing table, the following actions are taken (using the network in Figure 13-6 as an example). The following list describes the figure and explains the actions taken on the information provided: -
The topology table of Router A has a path (successor) of A to D to G to X. -
The FD is 20, and the AD from Router D is 15. -
When Router D dies, Router A must find an alternative path to X. -
Neighbors B, C, E, and F have ADs of 27, 27, 20, and 21, respectively. -
Because all the neighbors have an AD that is the same or greater than the successor FD, none of these are acceptable as FSs. -
Router A must go into active mode and send queries to the neighbors. -
Both Routers E and F reply with an FS because both have an AD from Router G of 5. Remember the equation FD > AD; the Routers E and F have an FD of 21, and 21 > 5. -
Because the FD is acceptable, the topology and routing tables will be updated, DUAL will be calculated, and the network will be returned to passive mode. -
From this information received from Routers E and F, the router selects the path through E as the best route because it has the lower cost. -
The result is placed in the routing table as the valid neighboring router. EIGRP refers to this neighboring router as a successor . -
Router F will be stored as an FS in the topology table. Figure 13-6. The Use of Feasible and Advertised DistanceActive Mode 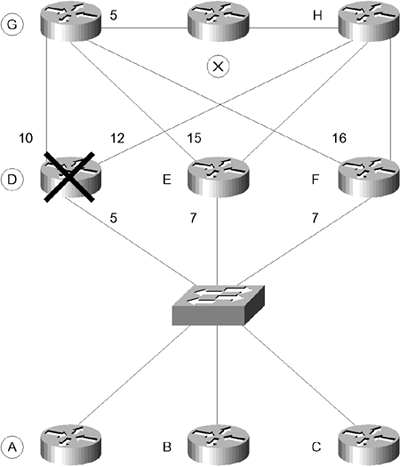 NOTE Figure 13-6 is simplified to explain the concepts. In reality, the split horizon rule dictates that Routers B and C would not readvertise routes it learned through an interface out of that same interface. Because all routes to X are learned through one interface, no routes to X would be readvertised out of this interface.
The details on how EIGRP computes successors are complex, but the concept is simple, as described in the next section. Choosing a Successor To determine whether a path to a remote network is feasible, EIGRP considers the feasible condition (FC) of the route. Essentially, each router holds a routing table that is a list of the available networks and the best or most efficient path to each of them. The term used to describe this is the feasible distance of the successor , otherwise known as the metric for the route. The router also holds the routing table of its neighbors, referred to as the AD. If the AD is within scope, this route may be identified as an alternative route, or an FS. A neighbor can become an FS for a route only if its AD is less than the FD. This is DUAL's fundamental key to remaining loop-free; if a route contains a loop, the AD will be greater than the FD and therefore will fail the FC. By holding the routing tables of the neighbors, the amount of network overhead and computation is reduced. When a path to a remote network is lost, the router might be capable of finding an alternative route with minimal fuss, computation, or network traffic. This gives the much-advertised benefit of very fast convergence. As you can see in the explanation for finding an FS in the previous section, "Updating the Routing Table in Active Mode with DUAL," queries can be sent throughout the organization's network. This is the design key to ensuring that EIGRP scales. EIGRP Network Design EIGRP is designed to work in very large networks. However, EIGRP, as with OSPF, is design-sensitive. Scaling a networkor, in other words, improving its capability to grow in size and complexityis a major concern in today's organizations. New demands are constantly driving the networks to use applications that require more bandwidth and other resources from the network. For example, simply consider the need for every desktop and every user to be able to attach to centralized resources as well as to the Internet. The factors that can affect the scaling of EIGRP are as follows : -
The amount of information sent between neighbors -
The number of routers that are sent updates -
How far away the routers are that have to send updates -
The number of alternative paths to remote networks Poorly scaled EIGRP networks can result in the following: Some of these symptoms are caused by other factors, such as poor design, with resources overwhelmed by the tasks assigned. Often, many of these symptoms are characterized by a route being flagged as SIA, as the router waits for a reply from a neighbor across a network that cannot handle the demands made upon it. Careful design and placement of network devices can remedy many of the problems seen in a network. Solutions to EIGRP Scaling Issues The design of the network is very important to the ability to scale any network. The following solutions revolve around a carefully thought-out network: -
Allocation of addresses should be contiguous to allow summarization. -
A hierarchical tiered network design should be used to allow summarization. -
Sufficient network resources (both hardware and software) on network devices. -
Sufficient bandwidth should be used on WAN links. -
Appropriate EIGRP configuration should be used on WAN links. By default, EIGRP only uses 50 percent of the bandwidth of the link for its traffic. This default may be tuned manually. -
Filters should be used. -
Network monitoring should be used. EIGRP Design Issues The major concern in scaling an organizational network is controlling the network overhead that is sent over slow WAN links in particular. The less information about the network, its services, and networks that needs to be sent, the greater the capacity available for the data between clients and servers. Although sending less routing information relieves the network, it gives the routers less information with which to make decisions. Every designer of routing protocols and every network administrator must deal continually with this trade-off. As seen with summarization, static and default routes can lead to poor routing decisions and loss of connectivity. EIGRP automatically summarizes at the autonomous system boundary and at the classful network boundary. To configure manual configuration, it is first necessary to disable automatic summarization. Summarization is configured at the interface level. This obviously requires careful consideration of the network design in reference to the flow of data and the network topology. Although still a distance vector protocol and proprietary, EIGRP addresses many of the problems related to scaling the network. Remember that queries must be limited to ensure that EIGRP can properly scale. If queries are allowed to traverse the entire organization, the problems and symptoms described will ravage your network. Many believe that dividing the organization's network into different EIGRP autonomous systems is a good way of limiting the query range. This is true, because EIGRP does not share updates with another autonomous systems. However, many organizations that created autonomous systems to replicate OSPF areas naturally redistribute between them so that the entire organization can share routing information. At this point, the query is propagated into the new autonomous system, and the problem continues. Summarization is the best way to limit the query range of EIGRP networks. If a subnet is hidden by summarization, the query will stop at the first router that has no knowledge of it. Certain topologies, although valid in most instances, pose problems for the EIGRP network. This is true in particular for the hub-and-spoke design often seen implemented between remote sites and regional offices. The popular dual- homed configuration, although providing redundancy, also allows the potential for routers to reflect queries back to one another. Summarization and filters make this network design work well while also allowing queries to be managed effectively. |