Using OUs to Delegate Administration
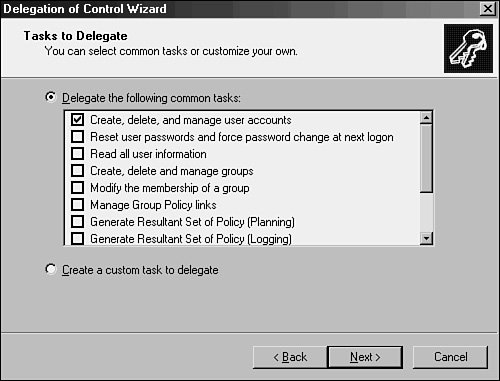
| As previously mentioned, one of the most important reasons for creating an OU structure in Active Directory is for the purpose of delegating administration to a separate administrator or administrative group. Whereas in NT 4.0 separate domains were necessary for this type of functionality, Active Directory allows for this level of administrative granularity in a single domain. This concept is further illustrated in this section. Essentially, the role of the NT resource domain has been replaced by the concept of the organizational unit. A group of users can be easily granted specific levels of administrative access to a subset of users. For example, a remote IT group can be granted standard user creation/deletion/password-change privileges to its own OU. The process of delegating this type of access is quite simple and involves the following steps:
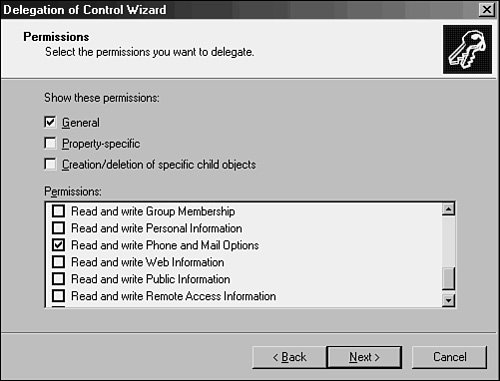
In fact, the Delegation of Control Wizard allows for an extremely specific degree of administrative granularity. If desired, an administrator can delegate a group of users to be able to modify only phone numbers or similar functionality for users in a specific OU. Custom tasks can be created and enabled on OUs to accomplish this and many other administrative tasks. For the most part, a very large percentage of all the types of administration that could possibly be required for delegation can work in this way. To use the phone administration example, follow these steps to set up custom delegation:
The possible variations are enormous, but the concept is sound. Active Directory's capability to delegate administrative functionality to this degree of granularity is one of the major advantages inherent in Windows Server 2003. |
EAN: 2147483647
Pages: 499