Scenario 3: PPPoE SoftwareHardware Problems
Scenario 3: PPPoE Software/Hardware ProblemsPPPoE was covered in great detail in Chapter 21. In this case, the types of problems you might encounter with PPPoE are identified. As you might know, the use of PPPoE software continues to increase, especially in the DSL industry. PPPoE can be used with cable, but it is rarely used by cable ISPs. Companies such as AT&T @Home currently use a static computer name to authenticate their users. Numerous PPPoE clients are in use today, but only three comprise 90 percent of the market. These three main PPPoE clients are NTS Enternet 300 (SBC), WinPoet (Verizon, Earthlink), and RASPPPoE (Freeware). The subsequent sections cover each client (after first presenting an overview of PPPoE and the MTU issue). This section demonstrates to you how to configure and troubleshoot the following two topics:
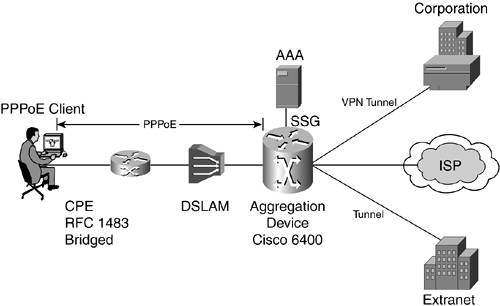
PPPoE is similar to a dialup connection: you bring up a dialer on your PC, type a username and password, and hit connect. Your user information is then passed to an authentication server through the access concentrator, and if you are successfully authenticated, you get connected. All PPPoE negotiations are done on the ISP side, so after you get connected, you can connect with your VPN client (see Figure 22-8). Figure 22-8. The Basic PPPoE Infrastructure; All the PPPoE Negotiations Are Done on the ISP Side
Case 1: PPPoE Software IssuesBased on previous discussions, the MTU issue is one of the greatest problems faced by VPN users, and unfortunately, it also carries over to PPPoE. The MTU settings when using the PPPoE protocol are the main contributor to most of the problems. NOTE The Set MTU application in the VPN client does not have the capability to adjust the MTU on a PPPoE virtual adapter. As of October 2002, there are no plans to add PPPoE adjustment capabilities to the VPN 3000 Client Set MTU application. If you try to connect without lowering the MTU on your PPPoE adapter, you might experience severe problems such as failure to download e-mail, failure to browse the intranet, and failure to browse the internal domain. In the following three sections, you learn about the steps required to lower the MTU on all three of the major PPPoE clients. MTU Settings in NTS Enternet 300NTS Enternet 300 has proven to be one of the dominant PPPoE clients in the market, particularly on the West coast. It is a solid client, easy to configure, and it works well with Cisco's VPN client. This section focuses on configuring NTS Enternet 300 on multiple Windows operating systems. For Windows 95/98,
For Windows NT/2000,
MTU Settings in WinPoetWinpoet is another widely used PPPoE client. Although it is widely used it is not considered by most to be a great PPPoE client. It is difficult to modify MTU settings for it to work with the Cisco VPN client. Essentially, the Cisco VPN client and WinPoet do not work well together. Fortunately for the PPPoE users, they can use any PPPoE client. So there are no limitations prohibiting a user from switching PPPoE clients. We have formulated a method to adjust the MTU using WinPoet, which follows; however, Cisco recommends switching to another PPPoE client such as NTS Enternet or RASPPPoE. WinPoet does not provide user control over the PPPoE MTU under Windows 95/98. But for Windows NT/2000, you can control it by explicitly setting the following registry key:
The <guid> and <adapternumber> can vary on different systems. Browse through the registry, looking for the MaxFrameSize value. WARNING Edit the registry only if you are comfortable doing so. Incorrect registry entries can make your PC unstable or unusable. If you are not familiar with editing the registry, contact desktop support for assistance. MTU Settings in RASPPPoERASPPPoE is another good PPPoE client, and it is freeware. It gives users the ability to adjust the MTU without having to touch the registry and has been successfully tested with Cisco's VPN client. If you are interested in downloading or for more information on configuring RASPPPoE, visit http://user.cs.tu-berlin.de/~normanb/. For Windows 95/98,
For Windows NT/2000,
Additional information about this topic can be found at http://user.cs.tu-berlin.de/~normanb/README2K.HTM. Case 2: IOS-Based PPPoE IssuesIn today's environment, more and more devices support PPPoE. It is no longer just software and routers that can support PPPoE; devices such as the PIX 501 and 506, and the VPN 3002 hardware client also support PPPoE. There is a long list of Cisco routers that support PPPoE, including the 806, 826, 827, 827-4V, 828, SOHO 77, and SOHO 78. Although each one supports PPPoE, each one meets different needs. For more information on these product specifications, see www.cisco.com/univercd/cc/td/doc/product/access/acs_fix/827/827rlnts/820feat.htm. Hundreds of routers on the market support PPPoE. Although some were built to work with both PPPoE and VPN, others were built to meet the need for only one of the two. The following information provides output from a series of debug commands, which is not possible from a majority of routers on the market. Cisco 800 Series PPPoE Connection ProblemThis case demonstrates how a Cisco 806 router connects to an ISP using PPPoE. The 806 router connects to a generic ADSL modem and there is no other equipment besides the PC. In Example 22-6, the output shows the router trying to complete the PPPoE negotiation, but the Ethernet1 (WAN) interface is bouncing. You can also see what the log viewer displays with all filters set to high. The PPPoE's link control protocol (LCP) sends keepalives to the core. See the shaded comments in Example 22-6. Example 22-6. PPPoE Router Trying to Connect While the WAN Link Bounces[View full width] 806-ADSL#debug vpdn pppoe events and 806-ADSL#debug ppp negotiation THE LOG VIEWER IS OPEN 04:42:15: Vi1 LCP: echo_cnt 2, sent id 34, line up 04:42:25: Vi1 LCP: echo_cnt 3, id 35, line up 04:42:35: Vi1 LCP: echo_cnt 4, sent id 36, line up 04:42:45: Vi1 LCP: echo_cnt 5, sent id 37, line up 04:42:56: Vi1 PPP: Missed 5 keepalives, taking LCP down ! LCP misses 5 keepalive responses and then takes the line down. ! The keepalives act as integrity packets. 04:42:56: Vi1 IPCP: Remove link info for cef entry 165.1.1.1 04:42:56: Vi1 IPCP: State is Closed 04:42:56: Vi1 PPP: Phase is DOWN 04:42:56: PPPoE 12997: Shutting down 04:42:56: PPPoE : Shutting down client session 04:42:56: PPPoE 12997: O PADT L:0002.1762.ad36 R:0002.3b00.9d43 Et1 04:42:56: %DIALER-6-UNBIND: Interface Vi1 unbound from profile Di1 04:42:56: Vi1 PPP: Phase is ESTABLISHING, Passive Open 04:42:56: Vi1 PPP: No remote authentication for call-out 04:42:56: Vi1 LCP: State is Listen 04:42:56: %LINK-3-UPDOWN: Interface Virtual-Access1, changed state to down 04:42:56: Vi1 LCP: State is Closed 04:42:56: Vi1 PPP: Phase is DOWN 04:42:56: Di1 IPCP: Remove route to 165.1.1.1 04:42:57: %LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access1, changed state See Chapter 21 for a detailed explanation of PPPoE. Upgrading the Router's FirmwareBecause PPPoE is a relatively new technology, it is still going through growing pains, especially with VPN. Many companies, other than Cisco, who manufacture SOHO routers, are frantically trying to develop products that meet the PPPoE/VPN needs of the consumer. Some of these routers might not function as expected and they might not work with the Cisco VPN client right out of the box. The best approach when you have problems connecting to a VPN concentrator through a new router is to upgrade the firmware. Almost all companies post a copy of their latest firmware release on their web sites, along with instructions on how to implement it. Immediately upgrade the router's firmware to eliminate this possible cause. If you use a router with firewall capabilities and the firmware upgrade does not solve the problem, try to open up the firewall completely. If it works, you know you have to work on getting the correct ports open. See Scenario 5, Case 1 for more information on what ports and protocols must be allowed on a firewall. |
EAN: 2147483647
Pages: 235