Planning the Network
| After you have the licensing counts established, you can focus on the network implementation. This aspect of the installation covers a number of networking issues, from connecting to the Internet to internal IP address schemes to internal and external domain names. Each piece of this puzzle has a significant impact on the way the server will be set up, and because some networking changes are difficult to impossible to change down the line, it's best to spend some quality time in this area to make sure that you can get it right the first time. Connection to the InternetMany small businesses these days have some form of high-speed connection to the Internet, whether by DSL, cable modem, or one of many types of dedicated connections. With the lower-cost solutions, it is common for the ISP to require some form of authentication (PPPoE, for example) when connecting to its network. Others may tie your network connection to a specific MAC address from a network card. Some may require no authentication at all for basic network access. No matter what the ISP requires for connecting to its network, a growing number of small business consultants strongly recommend placing some type of router/firewall device between the ISP's connection and the rest of the network. In some cases, this is required by the ISP, but the practice is becoming a best practice for small businesses because it adds a layer of protection from the Internet in addition to the protection provided by both editions of SBS 2003. One NIC or TwoFor many experts in the SBS field, this is not really an option. The SBS community strongly recommends the use of two network cards in every SBS serverone to connect to the Internet, one to connect to the internal network. As shown in Figure 3.1, the external NIC in the server is attached to the ISP's network through a DSL or cable modem or some sort of router. The other NIC connects to a hub or switch internally, which then connects to the other workstations and printers on the internal network. Figure 3.1. Network diagram featuring a dual-NIC SBS configuration with the SBS server between the Internet connection and the internal workstations.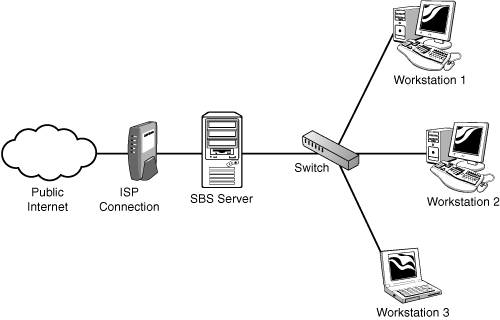 Why is this a good idea? There are many reasons, but the main one is that this layout physically separates the organization's computers from the Internet. Like adding a router/firewall between your company's network and the Internet, putting the SBS server between the router and your internal network adds another layer of protection from the Internet for your client computers. The built-in firewall included with SBS 2003 Standard Edition does a fine job of helping block malignant traffic from getting into your network. For even more robust protection, as well as limiting or tracking external network traffic from the client workstations, server administrators can install ISA 2000 (ISA 2004 with SP1) from the Premium Installation, which all but requires two network cards in the server. Are there downsides to the dual-NIC arrangement? Yes there are, but they are relatively few and relatively insignificant. The first response that many people have to this suggestion is that it represents a single point of failure. True, it does, but then so does your ISP. The other related concern is that in a dual-NIC setup, when the SBS server goes down, no one can get out to the Internet. In a correctly configured SBS setup, which will be detailed later, even if the server is configured with only a single network card, users will have difficulty getting out to the Internet. The reality is, though, that if the SBS server is built correctly and maintained properly, the chances of it going offline for any length of time are minimal. One problem that can arise in a dual-NIC configuration is the use of a network-aware device behind the SBS server that may not be compatible with ISA. Some devices, such as network-aware cameras or voice over IP (VoIP) phone systems, require direct access to the network without a proxy. In those cases, SBS could be configured with a single NIC and connect to a switch along with the remainder of the workstations and network-aware devices, as shown in Figure 3.2. Alternatively, the network-aware device could be attached directly to the router/firewall along with the external NIC of the SBS server, and the remainder of the workstations would be attached to a switch that connects to the internal NIC of the server, as shown in Figure 3.3. Figure 3.2. Network diagram featuring a single-NIC configuration where the server and all workstations connect to a switch, which is behind a hardware firewall.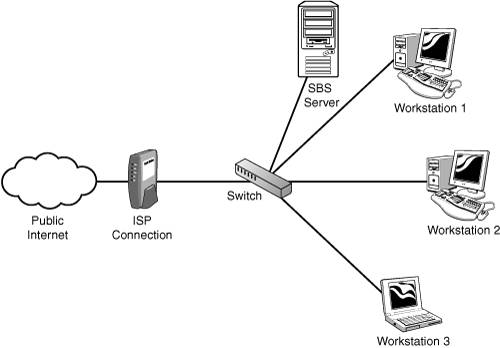 Figure 3.3. Network diagram featuring a dual-NIC configuration with a network-aware device behind the hardware firewall but in front of the SBS server.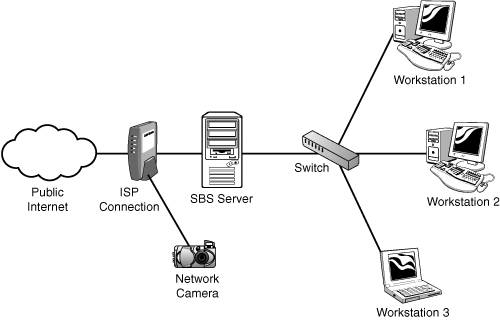 Although it is possible to configure more than two NICs in an SBS server, this is not recommended. The network configuration wizards in SBS 2003 assume that there will be one or two NICs and will not function as expected if there are more than two present and active in the server. Why would more than two network cards be needed in a server? One reason would be for connecting multiple physical network segments or more than one logical network. Although SBS could be configured to act as a network router in this configuration, would the benefits gained by doing so outweigh the costs of losing the ability to use the SBS wizards to configure the network? If this type of configuration was necessary, the use of a dedicated network router should be considered instead. Another reason people give for wanting to add more than two network cards in an SBS server is to improve network performance for transactions to and from the server. The thought is that by adding an additional NIC on the internal network, the server doubles its network bandwidth on that network. Simply adding another NIC on the same physical network will not achieve this. Certain network cards can be configured in a teaming NIC setup, where both NICs act as a single network interface as far as the server OS is concerned. In a small business network environment, chances are that a single network card on the internal network is going to be more than able to handle the network traffic on the internal subnet. If network bandwidth at the server is a bottleneck, upgrading all the devices on the network to a higher-bandwidth interface (such as moving from 100MB to Gigabit) will actually have more impact on network performance than adding another NIC on the internal network.
IP Address RangesWhen using SBS in the preferred dual-NIC configuration, the server needs to have two separate IP address ranges, one for each network card. Selecting the appropriate address ranges to use is important because a misconfigured network can cause many performance and connectivity issues. By default, SBS 2003 designates an IP address of 192.168.16.2 for its internal NIC with a subnet mask of 255.255.255.0. This gives the internal network an address range of 192.168.16.1-192.168.16.255. In a single-site small business installation, this address range should more than cover the number of devices connected to the server. During installation, this address range can be modified, but the IP address of the internal NIC must be a static address.
Note Why 192.168.16.x? Because many consumer-grade firewalls use 192.168.1.x for their internal address range. The 192.168.16.x range was selected so it would not conflict with these devices for an out-of-the-box configuration. The IP address assigned to the external NIC varies depending on a number of factors. In cases where an ISP provides a router to connect to its network, the ISP may configure the router so that it provides a DHCP address to devices that connect to it. The external NIC can be configured to get a DHCP address from the Internet router in this case, or it could be configured with a static IP address within the range of addresses allowed by the ISP router. When possible, the external NIC of the server should be given a static IP address. This is not required, however, unlike the address assigned to the internal NIC. The most important factor in specifying the IP address ranges for the external and internal networks is making sure that the two network cards do not have addresses in the same IP range. If the internal NIC uses the default 192.168.16.2 address, the external NIC cannot have an address on the 192.168.16.x range. An address in any 192.168.x.x address space other than 192.168.16.x is fine. Some administrators use a 10.x.x.x or 172.16.x.x address range to help avoid confusion as to which network is which when troubleshooting down the line. The reason for having the internal and external NICs on different IP subnets has to do with IP routing. Suppose that you have a server with two NICs, both on the 192.168.1.x subnet. The external NIC has an address of 192.168.1.2, and the internal NIC has an address of 192.168.1.3. Workstations connected to the internal network have IP addresses starting with 192.168.1.10 and higher. The external NIC connects to a firewall/router with an IP address of 192.168.1.1. The internal NIC is set as the primary network card. If an internal workstation needs to connect to the firewall/router to configure it, the workstation will send a request to 192.168.1.1. That request will be heard by the internal NIC of the SBS server, but the server will ignore it, because the request is for an address on the internal network. The workstation will never be able to make a connection to the device at 192.168.1.1. In the same way, if a user on the server attempts to open a connection to 192.168.1.1, the request will be broadcast on the internal NIC, because that is the primary network interface, and it is on the same subnet. That request will also never get routed to the external NIC, even though 192.168.1.1 would be assigned as the default gateway on the external NIC. DHCP ConfigurationBy default, the SBS installation attempts to install DHCP (Dynamic Host Configuration Protocol) services on the SBS server. This allows the SBS server to provide IP configuration information to workstations on the internal network that do not have static IP addresses. In most SBS installations, this is the recommended configuration.
Public and Private Domain NamesSelecting an appropriate internal domain name is just as important as selecting the correct IP address range during setup. Active Directory depends on the domain name used during setup, and Microsoft has long recommended against the use of publicly routable domain names for the Active Directory name space. In other words, if your company uses the public domain name smallbizco.net, you would not want to use smallbizco.net as your internal domain name. Instead, Microsoft would recommend that you use smallbizco.local as your internal domain name. Why not use smallbizco.net for the internal domain name? In Active Directory, the internal DNS server acts as the authoritative server for the internal domain, so the SBS DNS server would be the only place internal machines would look for any DNS request on the smallbizco.net domain. If the public website www.smallbizco.net is hosted with an external web service provider, its DNS record will be managed on public DNS servers, not on the SBS DNS server. If an internal workstation attempted to browse to www.smallbizco.net, it would ask the SBS DNS server to look up the address. The SBS DNS server, seeing that the hostname lies within the internal domain namespace, would look at its internal tables for an A record for www. If no record is found, it tells the requesting workstation that no record exists, even though the record actually does exist on the public Internet. The system administrator could add an A record for the www site and give it the public IP address, but then it becomes the system administrator's job to monitor the external web provider for changes to the IP address used to host www.smallbizco.net and make changes to the internal DNS whenever the public IP address changes. So the recommendation is to use a separate domain name scheme for internal domain records. Despite Microsoft recommendations, a growing number of SBS experts recommend the use of a name other than .local for the internal domain name. The primary reason for this is the growing number of Macintosh computers in the small business space. With the release of Mac OS X 10.2, Apple introduced a peer-to-peer network discovery technology called Rendezvous, which uses the .local namespace for name resolution. This implementation prevents Macintosh workstations from performing proper name resolution in the local network if the Active Directory namespace ends with .local. Although there is a way to reconfigure the Macintosh to be able to correctly resolve network names in the .local namespace, covered in Chapter 17, "Integrating the Macintosh into a Small Business Server 2003 Environment," if you are installing SBS into a new network and you know there will be Macintosh workstations in the network at installation or in the near future, give your internal namespace an extension other than .local, such as .lan or .office or something similar. Do not use a .mac extension as that could cause conflicts with future Apple network services. Note The .local and .lan top-level domains (TLDs) are not reserved domains. That means those domains could be put into service at some point in the future and become routable domains. Four reserved domains are identified in RFC 2606 (http://www.ietf.org/rfc/rfc2606.txt) for testing: .test, .example, .invalid, and .localhost. Although it's unlikely that the domains .local and .lan would be used as live top-level domains in the near future, a systems administrator who wanted to be absolutely certain that his internal domain would never be publicly routed could use one of the four reserved domains. Doing so would present a special set of challenges, because the .localhost name has special functions for referring back to the local machine, and the other names do not imply permanence. Wireless Network AccessOne of the biggest challenges facing the small business consultant today is the increasing use of wireless devices on the network. Many SOHO router/firewall devices now include a wireless interface so that laptops and other devices with wireless network interfaces can connect to the local network. Connecting wireless devices to the SBS server presents two issuessecuring the wireless connection and configuring access to server services. The basic rule of thumb for the placement of the wireless access point is this: If the client that is connecting to the wireless access point needs to access the resources on the SBS server, the access point should be located on the internal network. If the wireless client only needs "guest" access for the purpose of getting to the Internet but not to resources on the server, the access point should be located on the external network. Figure 3.4 shows the two locations for wireless access points in the network. Figure 3.4. Network diagram featuring two possible locations for a wireless access point on the network.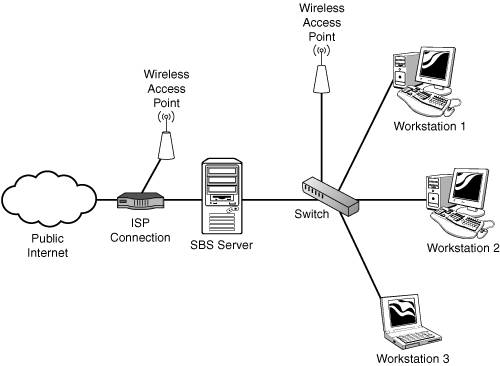 Connecting a wireless client to an access point on the internal network gives that client an internal IP address and allows the client to interact with the rest of the internal network just as if it were connected to the wired internal network. Connecting to an access point on the external network is similar to connecting the workstation on the public Internet. In a properly configured dual-NIC SBS installation, this workstation will be unable to access file and print services on the server. The client could set up a VPN connection to the server to access as though the workstation were on the internal network, or the client could connect through Remote Web Workplace to a workstation on the internal network. In either case, if a workstation needs full access to the server, it just makes more sense to connect the workstation to an access point on the internal network. |
EAN: 2147483647
Pages: 253