Modifying ISA
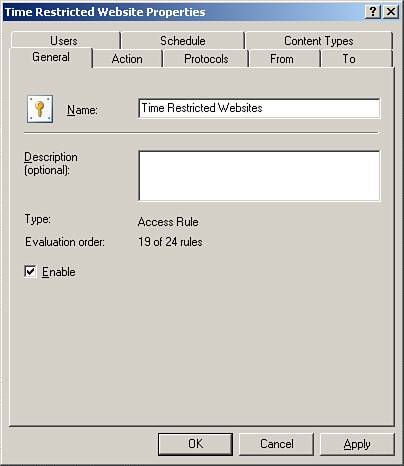
| ISA comes preconfigured with all the necessary settings to operate a generic installation of SBS 2003. However, because many businesses don't fit exactly into the generic model, modifying ISA's configuration is necessary. Understanding Application and Web FiltersIt is not an understatement to say that application filters are the real strength of ISA. Back in the day, router/firewall administrators were accused of not caring about anything above layer 3 in the OSI model, where packets are routed. Application filters allow ISA to inspect packets at layer 7 where the data resides. Being able to inspect the contents is a huge advantage giving ISA the capability to prevent a wide range of attacks by filtering out contents that don't adhere to standards. Most attacks count on the fact that firewalls in place today aren't intelligent. All they know is open or closed. ISA on the other hand checks the packet to see whether it matches the expected configuration and also whether this type of data is allowed on your network at all. To see the application filters, expand Configuration and then click on Add-ins. There are no configuration options in the filters themselves except to enable or disable them. By default all the filters are enabled except the H.323 and the SMTP filters (see Figure 24.7). The configuration of each of these filters actually comes in the specific rule definition as is described later in this chapter in the section "Allowing FTP Upload and Download to External Servers." Figure 24.7. ISA application filters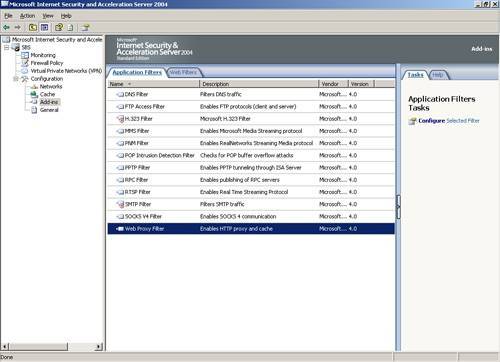 Web filters are similar to application filters in that they are simply enabled or disabled in this section. Web and application filters allow advanced security configurations of the features that they control and both application and web filters can be extended by third-party developers. Anatomy of a Firewall PolicyThe Firewall Policy in ISA 2004 Server is made up of both System Policies and user-specified policies called Firewall Policy Rules. There are about an equal number of each in the default configuration. Both types of policies are required for ISA to work for SBS and are created for you when you run the Connect to the Internet Wizard. System Policies can be changed only through the System Policy editor, whereas Firewall Policy Rules can be edited directly. During day-to-day administration, you will most often deal with Firewall Policy Rules and not the System Policy. Firewall Policy Rules are made up of several components: access rules, protocol definitions, user set, schedule, domain name set, URL sets, and content filters. (see Figure 24.8) You can pick and choose which of these components are needed for your new rule. The best way to learn how to create a new policy is to look at the existing policies. To facilitate this, ISA 2004 has a new feature that allows you to copy a rule. To copy a rule, right-click on the rule that you want to copy and select Copy, then right-click and select Paste to paste the copied rule into the Firewall Policy. The copied rule is called Rule Name (1), where Rule Name is the name of the original rule. Rename the copy and then begin your configuration changes. This feature can be a real time-saver. Figure 24.8. There are many options for refining a Firewall Policy Rule. Each tab contains options for fine tuning. If you have created rules in ISA 2000, you'll notice that you can now define each component as you configure the rule instead of configuring each item individually and then creating the rule last. This feature is also a great timesaver.
Components of a Firewall Policy RuleUnderstanding firewall policy isn't rocket science. At first it appears intimidating because there are so many options. In reality, the options allow the administrator an unprecedented amount of flexibility and control. A brief description of each component follows.
|
EAN: 2147483647
Pages: 253