Using the .NET Framework Configuration Tool
|
The .NET Framework Configuration Tool has a lot to offer the developer. It’s a tool that you should spend time learning, even if you aren’t using it for security needs. For example, this tool lets you view registered assemblies and add new ones using a graphical interface, as shown in Figure 4.5. Using this tool is easier than using utilities such as GACUtil (Global Assembly Cache Utility), which you use to register assemblies with strong names for global use.
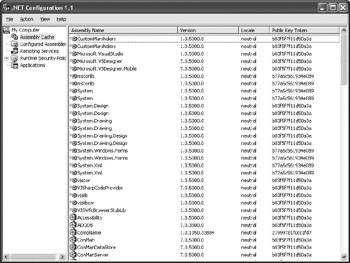
Figure 4.5: Add the .NET Framework Configuration Tool to your list of security aids.
| Note | This chapter assumes that you’re using the .NET Framework version 1.1 and associated .NET Framework Configuration Tool. The older 1.0 version is very similar, but you may see a few differences in screenshots, wording, and changes in some options or features. Even if you own the older version, you’ll find this discussion helpful. |
The following sections describe the security uses of the .NET Framework Configuration Tool. I’ll also include some usage notes as the book progresses and show how the tool affects the output of programs. For now, however, concentrate on how you can use the tool to reduce your workload.
Working with Code Groups
The “Defining Membership and Evidence” section discussed the idea of code groups and I demonstrated how you could determine code membership characteristics. The .NET Framework only comes with one code group by default, the All_Code group. The Enterprise, Machine, and User policies all support this code group and you’ll generally use it for all local programs. However, you can modify how the code groups work and even add new code groups as the need arises. Any new code group you add will appear below the All_Code group in the hierarchy.
When you first select the Runtime Security Policy\<Level>\Code Groups\All_Code entry in the left pane of the .NET Framework Configuration Tool, you’ll see a help screen.
This screen contains options for adding new code groups or configuring the existing code group, as shown in Figure 4.6. (This figure also shows the location of the All_Code entry in the hierarchy.)
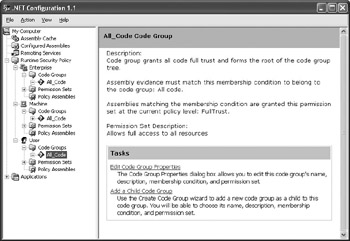
Figure 4.6: Add or edit code groups using this help screen.
You can use one of three ways to create a new code group. Click the Add a Child Code Group link and you’ll see a Create Code Group dialog box. This dialog box contains an option to create the code group manually (the first method), or you can import an XML file that contains the code you want to use (the second method). The third method is to right-click an existing code group and choose the Duplicate entry from the context menu. This technique creates a code group with the same characteristics as the parent.
| Tip | You don’t have to use the .NET Framework Configuration Tool to edit policies for a system. The configuration files are actually XML based, so you can edit them with any good XML editor. In fact, the Visual Studio .NET IDE reads these files without any problem. If you prefer a command line approach, you can use the CASPol utility to make any required changes. The enterprise, application domain, and machine level configuration files appear in the \WINDOWS\Microsoft.NET\Framework\<Version Number>\CONFIG folder, while the user information appears in the \Documents and Settings\<User Name>\Application Data\Microsoft\CLR Security Config\<Version Number> folder. The example in the “SecurityManager Class Example” section of Chapter 2 shows how to obtain the precise locations of these files using the SecurityManager.PolicyHierarchy() method. The PolicyLevel.StoreLocation property contains the directory information. |
When you choose to create a code group manually, you pass through several dialog boxes. Each dialog box asks a question about the new code group including the condition type (such as ApplicationDirectory, Zone, or Hash) and the permission set (such as Full Trust, Execution, or Internet).
Editing a code group means changing features such as the condition type and the permission set. When you click Edit Code Group Properties on the help screen, you see a Properties dialog box similar to the one shown in Figure 4.7.
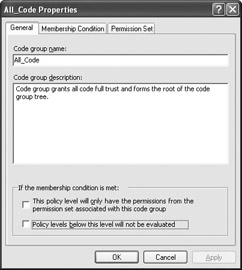
Figure 4.7: Use this dialog box to change the characteristics of a code group.
Notice that you can use this dialog box to determine how the code group will work with the policy levels. The first check box lets you set the code group to use permissions associated with the permission set for the code group exclusively. The second tells CLR not to evaluate policy levels below the existing policy level. In other words, this check box creates an exclusive code group.
Creating and Defining Permission Sets
The .NET Framework comes with a standard set of permissions. You can create additional permission sets as required to meet specific programming needs. In addition, you can modify the definitions for existing permissions. However, modifying a current permission isn’t a good idea because that action will change the default meaning of the permission and could cause applications written by other developers to fail. (CLR prevents you from changing .NET Framework specific permission sets.)
You have the same options for creating a new permission set as described in the “Working with Code Groups” section. When you create a new permission manually, you’ll see the Create Permission Set dialog box. The first screen asks for a name and description for the permission set. The second screen asks you to define the permission for the permission set, as shown in Figure 4.8.
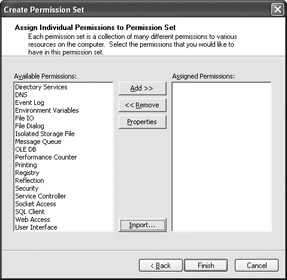
Figure 4.8: Define the permissions for your new permission set carefully to avoid security breaches.
Whenever you add a new permission, the .NET Framework Configuration Tool displays a Permission Settings dialog box that helps you configure that particular permission. The dialog boxes vary by permission. For example, the File IO permission includes a setting that lets you define individual permissions for each drive you want the permission set to access, or you can grant unlimited drive access. You can click Import to import an XML file containing the permissions you want to use. Custom permission sets include a help screen that lets you view, change, and rename the permission set.
Defining Policy Assemblies
Policy assemblies contain the code used by CLR to evaluate the evidence presented by an object to obtain a permission. The default .NET Framework configuration is all you need unless you design a special policy that requires additional code. If you decide to create a unique policy, then you must add the assembly to the appropriate list or the evaluation will always fail. Unfortunately, you may find that .NET is less than helpful in telling you about the problem. It always appears as a security error.
Adding Configured Applications
The Applications folder isn’t strictly a security setting, but entries in this folder can affect individual applications. When you look at the help screen for the Applications folder, you see two entries. The first helps you add a new configured application to the list. The second helps you fix the configuration of an application. For example, the developer of an application may design it to use an assembly that isn’t available or is outdated.
You need to consider two configured application features. First, this utility lets you change the code bases for the application. Several of the applications in this chapter rely on the code base provided by the application, so it’s easy to see how changing the code base could affect the security of the application as well.
The second feature appears on the Properties dialog box for the application. To display this dialog box, right-click the application entry and select Properties from the context menu. The .NET Framework Configuration Tool normally checks the Enable Publisher Policy check box by default. However, it’s possible that someone could clear this check box, which will affect the security of the application. You could find that the application fails because someone has turned the publisher policies off.
|
EAN: 2147483647
Pages: 168