Protocol Drivers
| < Day Day Up > |
| Networking API drivers must take API requests and translate them into low-level network protocol requests for transmission across the network. The API drivers rely on transport protocol drivers in kernel mode to do the actual translation. Separating APIs from underlying protocols gives the networking architecture the flexibility of letting each API use a number of different protocols. The protocol drivers that Windows includes are TCP/IP, TCP/IP with IP version 6 (IPv6), NWLink, and the AppleTalk protocol. Here's a brief description of each protocol:
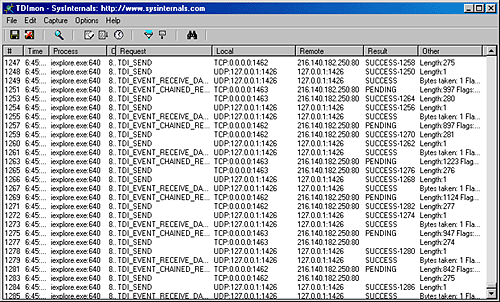
TDI transports in Windows generally implement all the protocols associated with their primary protocol. For example, the IPv4 TCP/IP driver (\Windows\System32\Drivers\Tcpip.sys) implements TCP, UDP, IP, ARP, ICMP, and IGMP. A TDI transport generally creates device objects that represent particular protocols so that clients can obtain a file object representing a protocol and issue network I/O to the protocol by using IRPs. The TCP/IP driver creates several device objects that represent various TDI-client accessible protocols: \Device\Tcp, \Device\Udp, \Device\Ip, and on Windows XP and Windows Server 2003, \Device\Rawip and \Device\Ipmulticast.
So that networking API drivers don't need to employ various interfaces for each transport protocol they might want to use, Microsoft established the Transport Driver Interface (TDI) standard. As mentioned earlier in this chapter, a TDI interface is essentially a convention for the way network requests format into IRPs and for the way network addresses and communications are allocated. Transport protocols that adhere to the TDI standard export the TDI interface to their clients, which include networking API drivers such as AFD and the redirector. A transport protocol implemented as a Windows device driver is known as a TDI transport. Because TDI transports are device drivers, they format requests they receive from clients as IRPs. Support functions in the \Windows\System32\Drivers\Tdi.sys library, along with definitions developers include in their drivers, make up the TDI interface. The TDI programming model is very similar to that of Winsock. A TDI client executes the following steps to establish a connection with a remote server:
TDI also supports connectionless communications for connectionless protocols such as UDP. In addition, TDI provides a means whereby a TDI client can register event callbacks (that is, functions that are directly invoked) with TDI transports. When it receives data from across the network, a TDI transport can invoke a registered client receive callback, for example. This event-based callback feature of TDI allows the TDI transport to notify its clients of network events, and clients that rely on event callbacks don't need to preallocate resources such as buffers when receiving network data because they can view the contents of the buffers supplied by a TDI protocol driver.
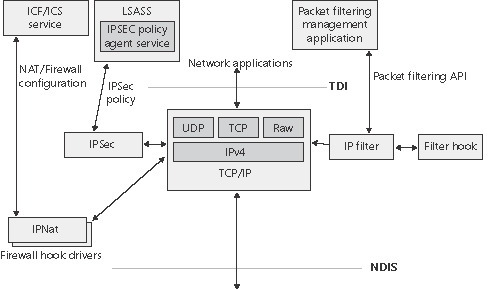
TCP/IP ExtensionsOther Windows networking services extend basic networking features of the TCP/IP protocol driver by relying on add-on drivers that integrate with the TCP/IP protocol driver using private interfaces. These include network address translation (NAT), IP filtering, IP hooking, and Internet Protocol security (IPSec). Figure 13-17 shows how these extensions interface with the TCP/IP driver. Figure 13-17. TCP/IP extension architecture
Network Address TranslationNetwork address translation (NAT) is a routing service that allows multiple private IP addresses to map to a single public IP address. Without NAT, each computer of a LAN must be assigned a public IP address to communicate across the Internet. NAT allows one computer of the LAN to be assigned an IP address and the other computers to use private IP address and be connected to the Internet through that computer. NAT translates between private IP addresses and the public IP address as necessary, routing packets between LAN computers and the Internet. NAT components on Windows consist of a NAT device driver, \Windows\System32\Drivers\ Ipnat.sys, that interfaces with the TCP/IP stack as well as editors that can perform additional packet processing beyond address and port translation. NAT can be installed as a routing protocol component with the Routing And Remote Access MMC snap-in or by configuring Internet Connection Sharing (ICS) using the Network Connections folder (although NAT is much more configurable when installed using the Routing And Remote Access MMC snap-in). IP FilteringWindows 2000, Windows XP, and Windows Server 2003 all include a very basic IP filtering capability where a user can choose to allow only certain ports or IP protocols. While this capability can serve to protect a computer from unauthorized network accesses, its drawback is that it is static and does not automatically create new filters for traffic initiated by applications running on the computer. Windows XP introduces a personal firewall capability called Internet Connection Firewall (ICF) that goes beyond the basic filtering just described. ICF implements a stateful firewall, which is one that keeps track of traffic flow so that it distinguishes between TCP/IP traffic that originates on the local LAN and unsolicited traffic that originates on the Internet. When ICF is enabled on an interface, by default all unsolicited incoming traffic received by the computer is discarded. A user or application can define exceptions so that services running on the computer, such as file and printer sharing or a Web site, can be accessed from other computers. The ICF/ICS service, which executes in a Svchost process, passes exception rules defined in the ICF user interface to the IPNat driver. In kernel mode, ICF is implemented in the same driver, \Windows\System32\Drivers\Ipnat.Sys, that implements Network Address Translation. The NAT driver registers with the TCP/IP driver as a firewall hook driver. The TCP/IP driver executes the callback functions of each registered firewall hook as it processes both inbound and outbound IP packets. A callback function can provide NAT functionality by modifying source and destination addresses in a packet, or as a firewall by returning a status code to TCP/IP that requests that TCP/IP drop the packet and cease processing for it. Although Ipnat implements ICF using the TCP/IP firewall hook interface, Microsoft recommends that third parties implement packet filtering as an NDIS Intermediate Driver (described later in this chapter). IP Filter and Filter HookWindows XP and Windows Server 2003 include a user-mode packet filtering API and an IP filter driver, \Windows\System32\Drivers\Ipfltrdrv.sys, that together allow applications to manage packet flow into and out of a system. The IP filter driver also allows at most one driver to register as a filter hook driver. In a manner similar to the way it interacts with firewall hook drivers, TCP/IP executes a function that the IP filter driver specifies, which allows the IP filter to drop or modify packets. The IP filter in turn invokes a callback specified by the filter hook driver, propagating modifications or a request to drop the packet to the TCP/IP driver. The filter hook functionality provided by the system allows third-parties to add translation, firewall, logging, or other functionality to the system. Internet Protocol SecurityInternet Protocol security (IPSec), which is integrated with the Windows TCP/IP stack, helps protect unicast IP data against attacks such as eavesdropping, sniffer attacks, data modification, IP address spoofing, and man-in-the-middle attacks. You can use IPSec to provide defense-in-depth against network-based attacks from untrusted computers, attacks which can result in the denial-of-service of applications, services, or the network; data corruption, data theft, user-credential theft; and the administrative control over servers, other computers, and the network. IPSec helps defend against network-based attacks through cryptography-based security services, security protocols, and dynamic key management. IPSec provides the following properties for unicast IP packets sent between trusted hosts:
You can use IPSec to help defend against network-based attacks by configuring host-based IPSec packet filtering and enforcing trusted communications. When you use IPSec for host-based IPSec packet filtering, IPSec can permit or block specific types of unicast IP traffic based on source and destination address combinations and specific protocols and specific ports. Because IPSec is integrated at the IP layer (layer 3) of the TCP/IP stack and it is applied to all applications, you do not need to configure separate security for each application that uses TCP/IP. In an Active Directory environment, Group Policy can be used to configure domains, sites, and organizational units (OUs), and IPSec policies can then be assigned as required to Group Policy Objects (GPOs). Alternatively, you can configure and assign local IPSec policies. Active Directory-based IPSec policies are stored in Active Directory, and a copy of the current policy is maintained in a cache in the local Registry. Local IPSec policies are stored in the local system registry. To establish trusted communications, IPSec uses mutual authentication, and it supports the following authentication methods: Kerberos version 5, a computer X.509 version 3 public key certificate, or a preshared key. The Windows implementation of IPSec is based on IPSec Requests for Comments (RFCs). The Windows IPSec architecture includes the IPSec Policy Agent, the Internet Key Exchange (IKE) protocol, and an IPSec driver:
You can use the IP Security Policy Management snap-in that is available in MMC to create and manage IPSec policy. This snap-in can be used to create, modify, and store local IPSec policies or Active Directory based IPSec policies, and to modify IPSec policy on remote computers. In Windows XP and Windows Server 2003, after IPSec-secured communication is established, you can monitor IPSec information for local computers and for remote computers by using the IP Security Monitor snap-in that is available in MMC. |
| < Day Day Up > |
EAN: 2147483647
Pages: 158