Implementing Access Control
In the real world, authorization is dictated by policy. When it comes to using resources, reading documents, or accessing rooms, different people have different access rights. The implementation of this policy can be locked safes or badge-access rooms. In the Windows 2000 environment, authorization is also based on policy. Different people or groups of people have different access rights. Policy here is implemented through access control. Quite simply, access control determines which users can access which resources. Resources in Windows 2000 are
- Files and folders, which can be accessed through Windows Explorer
- Shared volumes, folders, and files, which are allowed permissions on both NTFS and FAT file systems
- Active Directory objects, which are managed with the Active Directory Users and Computers snap-in
- Registry keys, which are managed with the Registry Editor
- Services, which are managed with the Security Configuration Tool Set
- Printers, which are configured through Settings on the Start menu
Each resource has a security descriptor associated with it that defines the object's owner, the object's access permissions, and the object's auditing information. Auditing of the object is discussed in the section "Auditing," later in this chapter.
For Active Directory objects, administrative responsibility can be delegated to group administrators. Delegating allows object permissions to be managed in one organizational unit of the domain, without requiring multiple administrators for the entire domain. For more information, see the section "Delegating Object Control" in Chapter 10.
Establishing Ownership
The owner of an object controls who can access the object by setting object permissions. By default, the object's owner is its creator. Typically, administrators create most network objects and are responsible for setting the object permissions.
One of the standard permissions associated with all objects is the Take Ownership permission. By granting this permission, the owner allows a user (or member of a group) to assume ownership of the object. Taking ownership can be done through the tool that manages the specific type of object. For example, printers are managed through the interface found under Settings on the Start menu. The Security tab on the Properties window for the printer shows the groups and users for which permissions are set. Clicking the Advanced button opens the Access Control Settings dialog box. With the correct permissions, ownership can be modified on the Owner tab. Administrators can assume control of any object under their administrative jurisdiction, regardless of the setting of the Take Ownership permission for the object.
Assigning Permissions
Object permissions are broken down into specific actions that can be performed on that particular object. For registry keys, this includes the ability to create subkeys and set values. For Active Directory objects, permissions include the ability to create and delete children.
Permissions are set for the specific users or groups who perform actions on a particular object. For a given folder, one group may be granted permissions to create and delete files within that folder. Another group may be allowed only to list the folder's contents. Figure 18-9 shows printer permissions granted to Everyone.
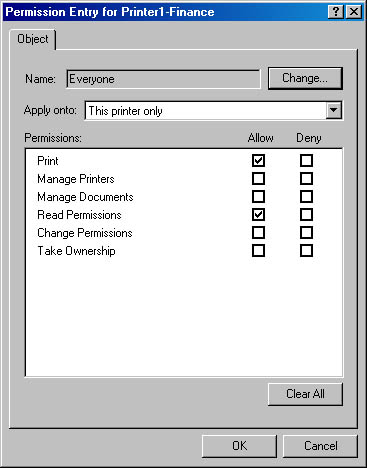
Figure 18-9. Printer permissions for the group Everyone.
To display permissions for a user or group, choose an entry in the Access Control Settings dialog box, and click the View/Edit button. The owner of the object, or a user or group granted Change Permissions permission, can use this dialog box to modify permissions for the user or group. To add a user or group to the access control list (Figure 18-10), click the Add button and select the user or group to add. Remember to set the appropriate permissions.

TIP
The burden of administering a domain of user rights and permissions can be eased by following a few guidelines. First, delegate administration to local authorities whenever closer management of users and services makes sense. Second, assign permissions on a group basis, rather than on a user basis. Third, set permissions at common node points in Active Directory and let them propagate down the tree to lower nodes.
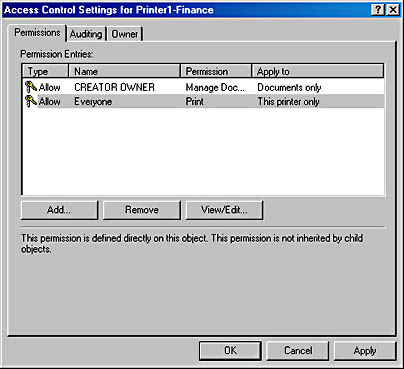
Figure 18-10. The Access Control Settings dialog box.
EAN: 2147483647
Pages: 366