Share Permissions vs. NTFS Permissions
|
| < Day Day Up > |
|
Share permissions determine the maximum access over the network. NTFS permissions can be more restrictive but can’t expand beyond the limits established by the share permissions. Share permissions have no effect on a user who logs on locally or to a terminal server user of the computer. Share permissions are the only restrictions available for shares on a FAT volume.
On NTFS volumes (required for Windows Small Business Server), folders have the same share permissions as those on a FAT volume, but another type of permissions—greatly superior to share permissions—is available beyond that. NTFS permissions use access control lists (ACLs) to limit access to resources, and can be assigned only to resources on an NTFS volume. NTFS permissions can be assigned to both files and folders and apply over the network and locally.
Microsoft Windows Server 2003 (and therefore Windows Small Business Server) uses the default share permission of Everyone = Read. (Microsoft Windows 2000 and Windows NT uses a default share permission of Everyone = Full Control.) You can change the share permission to Everyone = Full Control or Domain Users = Full Control (for more security) and use NTFS permissions for more granular control.
Whatever your choice, avoid configuring both share permissions and NTFS permissions because the result can be unpredictable and hard to troubleshoot.
| Caution | If shared permissions are configured for a folder, and NTFS permissions are configured for the folder and its contents, the most restrictive permissions apply. An exception is when an individual user is granted share permission and the user is also part of a group with a different permission. In this case, the user’s effective permissions are the combination of the user and group permissions. Consider a user who has only Read access through a share permission but also belongs to a group with Full Control share permission. In this case, the user has Full Control. |
How Permissions Work
If you take no action at all, the files and folders inside a shared folder have the same permissions as the share. Permissions for both directories and files can be assigned to the following:
-
Groups and individual users on this domain
-
Global groups, universal groups, and individual users from domains that this domain trusts
-
Special identities such as Everyone and Authenticated Users
The important rules for permissions can be summarized as follows:
-
By default, a folder inherits permissions from its parent folder. Files inherit their permissions from the folder in which they reside.
-
Users can access a folder or file only when they are granted permission to do so or they belong to a group that has been granted permission.
-
Permissions are cumulative, but the Deny permission trumps all others. For example, if the Sales group has Read access to a folder and the Finance group has Modify permission for the same folder, and Wally is a member of both groups, Wally has the higher level of permission, which is Modify. However, if the Sales group permission is changed to explicitly Deny, Wally is unable to use the folder, despite his membership—and ostensibly higher level of access—in the Finance group.
-
The user who creates a file or folder owns the object and can set permissions to control access.
-
An administrator can take ownership of any file or folder.
-
Members of the Administrators, Backup Operators, and Server Operators built-in security groups can take ownership and reassign ownership.
Working with NTFS File and Folder Permissions
Windows Small Business Server has a set of standard NTFS permissions that are combinations of specific kinds of access. The individual permissions are Full Control, Modify, Read & Execute, List Folder Contents, Read, and Write. Each of these permissions consists of a group of special permissions. Table 10-2 shows what special permissions are included with each standard permission.
| Special Permission | Full Control | Modify | Read & Execute | List Folder Contents | Read | Write |
|---|---|---|---|---|---|---|
| Traverse Folder/Execute File | Yes | Yes | Yes | Yes | No | No |
| List Folder/Read Data | Yes | Yes | Yes | Yes | Yes | No |
| Read Attributes | Yes | Yes | Yes | Yes | Yes | No |
| Read Extended Attributes | Yes | Yes | Yes | Yes | Yes | No |
| Create Files/Write Data | Yes | Yes | No | No | No | Yes |
| Create Folders/Append Data | Yes | Yes | No | No | No | Yes |
| Write Attributes | Yes | Yes | No | No | No | Yes |
| Write Extended Attributes | Yes | Yes | No | No | No | Yes |
| Delete Subfolders and Files | Yes | No | No | No | No | No |
| Delete | Yes | Yes | No | No | No | No |
| Read Permissions | Yes | Yes | Yes | Yes | Yes | Yes |
| Change Permissions | Yes | No | No | No | No | No |
| Take Ownership | Yes | No | No | No | No | No |
File permissions include Full Control, Modify, Read & Execute, Read, and Write. As with folders, each of these permissions controls a group of special permissions. Table 10-3 shows the special permissions associated with each standard permission.
| Special Permission | Full Control | Modify | Read & Execute | Read | Write |
|---|---|---|---|---|---|
| Traverse Folder/Execute File | Yes | Yes | Yes | No | No |
| List Folder/Read Data | Yes | Yes | Yes | Yes | No |
| Read Attributes | Yes | Yes | Yes | Yes | No |
| Read Extended Attributes | Yes | Yes | Yes | Yes | No |
| Create Files/Write Data | Yes | Yes | No | No | Yes |
| Create Folders/Append Data | Yes | Yes | No | No | Yes |
| Write Attributes | Yes | Yes | No | No | Yes |
| Write Extended Attributes | Yes | Yes | No | No | Yes |
| Delete Subfolders and Files | Yes | No | No | No | No |
| Delete | Yes | Yes | No | No | No |
| Read Permissions | Yes | Yes | Yes | Yes | Yes |
| Change Permissions | Yes | No | No | No | No |
| Take Ownership | Yes | No | No | No | No |
| Caution | Any user or group assigned Full Control on a folder can delete files and subfolders no matter what the permissions are on the individual files or subfolders. |
Considering Inheritance
Just to complicate matters a bit more, there are two types of permissions: explicit and inherited. Explicit permissions are the ones you set on folders you create. Inherited permissions are those that flow from a parent object to a child object. By default, when you create a subfolder, it inherits the permissions of the parent folder.
If you don’t want the child objects to inherit the permissions of the parent, you can block inheritance at the parent level or at the child level. Where you block inheritance is important. Block at the parent level and no subfolders inherit permissions. Block selectively at the child level and some folders inherit permissions but others do not.
To block a file or folder from inheriting permissions, right-click the folder, select Properties, and then click the Security tab. Click Advanced and clear the check box for Allow Inheritable Permissions From The Parent To Propagate To This Object And All Child Objects.
| Caution | An additional check box is shown on the Advanced Security Settings page. It’s Replace Permission Entries On All Child Objects With Entries Shown Here That Apply To Child Objects. If you select this option, subfolders and files have their permissions reset to those they inherit from a parent object. Once you select this item and click Apply or OK, you can’t go back and undo it. |
When the check boxes for permissions appear shaded, it means the permissions are inherited from a parent object. When the check boxes are shaded and have a check mark (Figure 10-7), some permissions are inherited and others have been added. There are three ways to change this situation:
-
Clear the check box for Allow Inheritable Permissions From the Parent To Propagate To This Object And All Child Objects. When the check box is cleared, you can make changes to the permissions or change the users or groups in the list.
-
Change the permissions of the parent folder.
-
Select the opposite permission—Allow or Deny—to override the inherited permission.
If neither Allow nor Deny is selected, the users or groups might have acquired the permission through a group membership. Otherwise, failure to explicitly configure Allow effectively denies the permission.
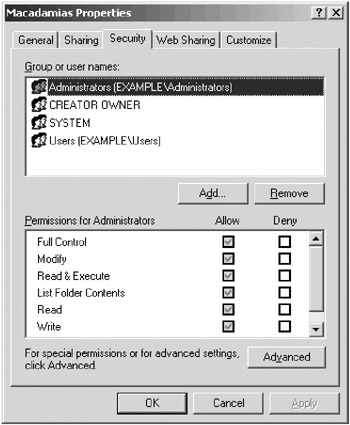
Figure 10-7: A folder with inherited and noninherited permissions.
Configuring NTFS Folder Permissions
Before sharing a folder on an NTFS volume, set all the permissions on the folder. When you set folder permissions, you’re also setting permissions on all the files and subfolders in the folder. To assign permissions to a folder, right-click the folder in Windows Explorer, choose Properties from the shortcut menu, and then click the Security tab.
-
To remove an individual or group from the list, select the name and click Remove.
-
To add to the list of those with permissions, click Add. This opens the Select Users, Computers, Or Groups dialog box. Or click Advanced to perform a more sophisticated search, as shown in Figure 10-8. Click OK when you’re finished.
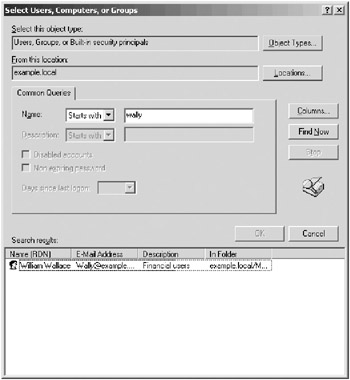
Figure 10-8: Selecting users and groups.
Assigning NTFS Permissions to Files
Permissions for individual files are assigned in the same way as folders. There are, however, some special considerations:
-
Remember to grant permissions to groups, rather than to individuals.
-
Create universal groups and assign file permissions to them rather than assign permissions directly to local groups.
| Caution | Groups or users who have Full Control for a folder can delete files and subfolders, no matter what protective permissions are assigned to the files and folders. |
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 224