Using the GPMC in Active Directory
| | ||
| | ||
| | ||
| Note | For the examples in this book, I'll refer to our sample Domain Controller, WINDC01, which is part of my example Corp.com domain. For these examples, you can choose to rename the Default-First-Site- Name site or notyour choice. |
Since many of us are still warming up to Group Policy, and even more people are warming up to the GPMC, I'll start with some basics to ensure that things are running smoothly. For most of the examples in this book, you'll be able to get with just the one Domain Controller and one or two workstations that participate in the domain, for verifying that your changes took place.
Again, I encourage you to not try these examples on your production network, in order to avoid a CLM ( Career-Limiting Move ).
Active Directory Users and Computers versus GPMC
The main job of Active Directory Users And Computers is to give you an "Active Directory object centric" view. Active Directory Users And Computers lets you deal with users, computers, groups, contacts, the operations masters (FSMOs), and delegation of control over user accounts as well as change the domain mode and define advanced security and auditing inside Active Directory. When you drill down inside Active Directory Users And Computers into an OU, you see the computers, groups, contacts, and so on contained within the OU.
But the GPMC has one main job: to provide you with a "Group Policy centric" view of all you control. All the OUs that you see in Active Directory Users And Computers are visible in the GPMC; however, the GPMC does not show you users, computers, contacts, and such. When you drill down into an OU inside the GPMC, you see but one thingthe GPOs that affect the objects inside the OU.
In Figure 1.6, you can see the Active Directory Users And Computers view as well as the GPMC view rolled up into one MMC that we created earlier. The Active Directory Users And Computers view of Temporary Office Help and the GPMC view of the same OU is radically different.
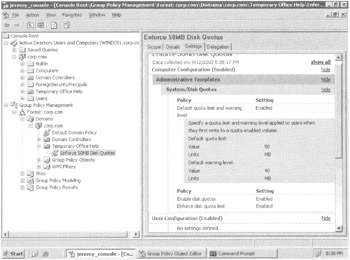
Figure 1.6: GPMC shows the same OUs as Active Directory Users and Computers. However, the GPMC shows GPO relationships, not users, computers, or other objects.
When focused at a site, a domain, or an OU within the GPMC, you see only the GPOs that affect that level in Active Directory. You don't see the same "stuff" that Active Directory Users And Computers sees, such as users, computers, groups, or contacts.
The basic overlap in the two tools is the ability to create and delete OUs. If you add or Deleteelete an OU in either tool, you need to refresh the other tool by pressing F5 to see the update. For instance, in Figure 1.6, you can see that my Active Directory has several OUs, including one named Temporary Office Help .
| Warning | Deleting an OU from inside the GPMC is generally a bad idea. Because you cannot see the Active Directory objects inside the OU (such as users and computers), you don't really know how many objects you're about to delete. So be careful! |
If I delete the Temporary Office Help OU in Active Directory Users And Computers, the change is not reflected in the GPMC window until it's refreshed. And vice versa.
Adjusting the View within the GPMC
The GPMC lets you view as much or as little of your Active Directory as you like. By default, you view only your own forest and domain. You can optionally add in the ability to see the sites in your forest, as well as the ability to see other domains in your forest or domains in other forests, although these views might not be the best for seeing what you have control over.
Viewing Sites in the GPMC When you create GPOs, you won't often create GPOs that affect sites. The designers of the GPMC seem to agree; it's a bit of a chore to apply GPOs to sites. To do so, you need to link an existing GPO to a site. You'll see how to do this a bit later in this chapter.
However, you first need to expose the site objects in Active Directory. To do so, right-click the Sites object in GPMC, choose "Show Sites" from the shortcut menu (see Figure 1.7), and then click the check box next to each site you want to expose.
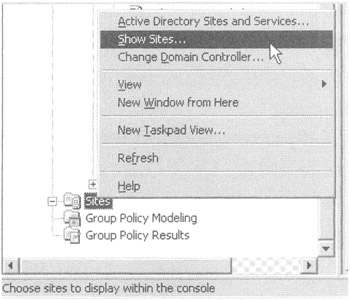
Figure 1.7: You need to expose the Active Directory sites before you can link GPOs to them.
In our first example, we'll use the site level of Active Directory to deploy our first Group Policy Object. At this point, go ahead and enable the Default-First-Site so that you can have it ready for use in our own experiments.
Viewing Other Domains in the GPMC To see other domains in your forest, drill down to the Forest folder in Group Policy Management, right-click Domains, choose Show Domains, and select the other available domains in your forest. Each domain will now appear at the same hierarchical level in the GPMC.
Viewing Other Forests in the GPMC To see other forests, right-click the root (Group Policy Management), and choose "Add Forest" from the shortcut menu. You'll need to type the name of the Windows 2003 forest you want to add. If you want to add or subtract domains within that new forest, follow the instructions in the preceding paragraph.
| Tip | You can add forests with which you do not have a two-way cross-forest trust. However, GPMC defaults will not display these domains as a safety mechanism. To turn off the safety, choose View menu ˜ Options to open the Options dialog box. In the General tab, clear "Enable Trust Detection" and click OK. |
Now that we've adjusted our view to see the domains and forests we want, let's examine how to manipulate our GPOs and GPO links.
The GPMC-Centric View
As we stated earlier, one of the fundamental concepts of Group Policy is that the GPOs themselves live in the "swimming pool" that is the domain. Then, when a level in Active Directory needs to use that GPO, there is simply a link to the GPO.
Figure 1.8 shows what our swimming pool will eventually look like when we're done with the examples in this chapter.
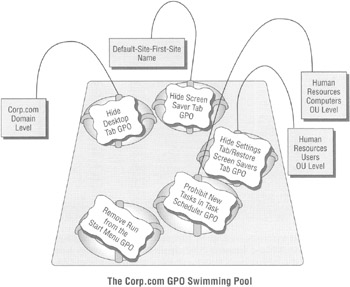
Figure 1.8: Imagine your upcoming GPOs as just hanging out in the swimming pool of the domain.
Our swimming pool will be full of GPOs, with various levels in Active Directory "linked" to those GPOs. To that end, you can drill down, right now, to see the representation of the swimming pool. It's there, waiting for you. Click Group Policy Management ˜ Forest ˜ Domains ˜ corp.com ˜ Group Policy Objects to see all the GPOs that exist in the domain. (See Figure 1.9.)
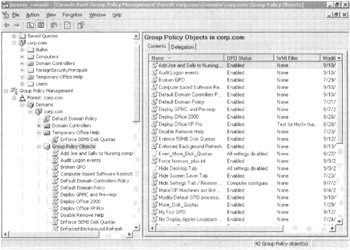
Figure 1.9: The Group Policy Objects folder highlighted here is the representation of the swimming pool of the domain that contains your actual GPOs.
| Note | If you're just getting started, it's not likely you'll have more than the "Default Domain Controllers Policy" GPO and "Default Domain Policy" GPO. That's OK. You'll start getting more GPOs soon enough. Oh, and for now, please don't modify the default GPOs. They're a bit special and are covered in great detail in Chapter 6. |
All GPOs in the domain are represented in the Group Policy Objects folder. As you can see, when the Temporary Office Help OU is shown within the GPMC, a relationship exists between the OU and the "Enforce 50MB Disk Quotas" GPO. That relationship is the tether to the GPO in the swimming poolthe GPO link back to Enforce 50MB Disk Quotas. You can see this linked relationship because the "Enforce 50MB Disk Quotas" icon inside Temporary Office Help has a little arrow icon, signifying the link back to the actual GPO in the domain.
| | ||
| | ||
| | ||
EAN: 2147483647
Pages: 110
- Structures, Processes and Relational Mechanisms for IT Governance
- Linking the IT Balanced Scorecard to the Business Objectives at a Major Canadian Financial Group
- Measuring ROI in E-Commerce Applications: Analysis to Action
- Technical Issues Related to IT Governance Tactics: Product Metrics, Measurements and Process Control
- The Evolution of IT Governance at NB Power