Workgroup Security Files
The effectiveness of the Access workgroup ( user -level) security hinges on the security of the workgroup file itself. As I explained in Chapter 8, workgroup security is relatively strong if the developer can ensure that the workgroup file is not released to the users. Unfortunately, the fundamental strategy behind the workgroup security system is that users and developers all share the same workgroup file. This noble strategy has lived on in many books, the Internet, and Access help files for most of the last decade . Unfortunately, in the last few years , that strategy has been compromised because a number of organizations have truly cracked the structure of the workgroup file. To understand this issue, let me first explain the basic structure of the workgroup file.
What is a Workgroup File?
A workgroup file is an encrypted Access database (see the preceding section) that contains a table of user accounts, passwords, and groups (called MSysAccounts) and a table of which users belong to which group (called MSysGroups). Both the users and groups will have a unique special identifier (SID) that is created from a workgroup identifier and a personal identifier (PID) that you enter at the time that you create the user account. To see the user accounts and groups tables for a developer workgroup file (discussed in Chapter 8), have a look a Figure 9-4. Here you will see that the information is stored in a simple design that has the SID and passwords encrypted. In this database, the Developer account belongs to both the Admins and the Users groups, whereas the Admin account only belongs to the Users group . To understand this data structure further, bear in mind that groups are stored in the MSysAccounts table and that the SIDs are the common data key between that table and the MSysGroups table.
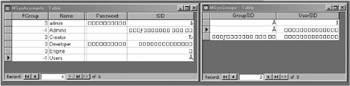
Figure 9-4: The Accounts and Groups tables from a workgroup file.
The Cracks in the Workgroup File
It really doesn't take a lot of guessing to realize that if the Access workgroup file uses a weak encryption algorithm, someone will one day work out how to extract the passwords from the file. To test this theory, I made a simple search on the Internet and discovered a number of software programs that claim to be able to read workgroup files and database passwords (discussed later in the chapter). Having tried a number of these products, I can tell you that they can read work-group files and retrieve the passwords for all the user accounts in a few seconds. Figure 9-5 shows the output from one of these programs.

Figure 9-5: A password recovery program, which retrieves complex workgroup passwords instantly.
So in summary, the workgroup file is small, a weak algorithm protects it, and even a novice hacker can open the file as a database and view enough of the contents to verify the supposed contents of the file.
So What do We do About Workgroup Security Flaws?
The best solution would be if Microsoft were to support a highly secure workgroup file. Unfortunately, Access 2003 is now on the streets , and there is no sign of any improvements to workgroup files. Therefore, we need an alternative strategy, and it will come from one or more of the following techniques:
-
Never release the workgroup files with the developer details to your users (Chapter 8).
-
Do your best to conceal the location of the workgroup files from your users.
-
Use the operating system to secure the folders and workgroup files from unwanted users.
Otherwise, you can just share the workgroup files between administrators and different levels of users and hope that they don't go looking for a password retrieval program to extract the passwords. If this option is going to be your strategy, make sure that you first enforce passwords for all accounts and second that the passwords are at least eight characters long, because the password retrieval programs provide the first few characters of the user account in the trial version. These unlicensed programs will always identify an account with no password, which is a pity because having no password is a useful time saver.
EAN: 2147483647
Pages: 176