Protecting Data Outside the Company Network
As soon as you distribute your database, you lose some of the important trump cards, such as disguising the location of the database and workgroup files and control over your environment. You also present users with the time and opportunity to try any tricks that they want. To better understand this reality, I have included an email from a person who was interested in protecting a database and my response.
| User Story | It's a typical user predicament. The email said, "I stumbled upon your vb123.com site thanks to a Google search, and I wonder if you could answer this question "I have a back-end/front-end application that I would like to distribute, but I need to protect the back-end data so that it is accessible (readable, maybe modifiable) only via front-end forms, but not extractable. I wondered if this is practical, and, if so, what are your suggestions? Also, have you any thoughts about including an individual encryption algorithm on some of the fields themselves ?" I replied, "Only distribute what you want your users to see and no more. Keeping the full design of the database from the end users is one way of guaranteeing the secrecy of important data. For example, do not distribute the names and addresses of people, or better still, only distribute consolidated information such as total number of people in each suburb. "Securing a database that you want to send to people around the world is probably the hardest thing that you could do. The MDE format will secure the VBA code and do a good job of protecting the reports and forms. The queries and tables can be secured to a reasonable level with user-level security and RWOP queries. There are a number of organizations that can unravel this security, but the catch is that the would-be thief would have to sign a legal document and pay a hefty fee for the job. Thankfully, software cannot currently be purchased or downloaded to do this for you. One thing that you will want to do is keep the developer workgroup file from your users at all costs "To take this a step further, a simple encryption of some key fields like you mentioned would probably suffice. This measure, combined with Access user-level security, would probably make it expensive to decipher, but some companies will do anything for a fee. Access is too popular and has been around too long to be bullet-proof. I would think long and hard about getting too carried away by it all." |
Distributing Your Data in Some Other Form
A good way to make your data safer is to adopt alternative ways of distributing it. In this case, Access provides many distribution alternatives, such as:
-
Send users snapshots or PDF versions of reports.
-
Save your reports to Excel or Word ( *.RTF format) if the output is suitable.
-
Distribute your information through email by using Microsoft Outlook Automation.
-
Create remote systems based on XML data that you export from Access 2002 or later.
-
Create Excel spreadsheets that summarize the information and allow users access to manipulate only the data that is relevant to them. I have been involved in a number of projects in which the end users simply view and manipulate data that is transferred through Excel Automation.
-
Install a third-party reporting system, such as Crystal Reports or SSW Reporter, to provide an alternative way to view the information.
-
Include your database on the Web and use Web-based technologies to secure and interface the data.
Now I will show you how to hide part of your data from your (remote) users.
Read with Owner Permission Queries
One way to restrict what a remote user account sees in an important table would be to use a particular query type called a Read with Owner Permissions (RWOP) query. This type of query allows a user account that has no permissions to view or change data by inheriting the permissions of the owner of the query. For example, if the owner of a table has read design permission and a user account does not, a RWOP query will allow the user to read columns from a table.
When you are protecting data, especially remote data, RWOP queries are very useful because the user will see only some of the fields in a protected table. Another use is to allow the user to see a consolidated view of data ( group by query). To illustrate this view, let's make a query where the anonymous user can see only the total number of orders per region but cannot see the orders table itself.
-
Log on to a copy of the Northwind database by using the Developer account.
-
Remove the read permissions from the ubiquitous Users group for the Orders table.
-
Create a query that returns only the table or query columns or calculated fields that you want the users to see.
-
When you have set up the query, choose View ˜ Query Properties.
-
Select the field Run Permissions from the list and choose Owner's, as shown in Figure 10-35.
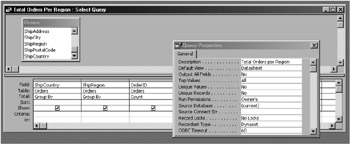
Figure 10-35: The design view of a RWOP query, showing the Run Permissions properties. -
Save the query.
The SQL for the RWOP query will look like the following:
SELECT ShipCountry, ShipRegion, Count(OrderID) AS TotalOrders FROM Orders GROUP BY ShipCountry, ShipRegion WITH OWNERACCESS OPTION;
Though I do see the merits in the occasional RWOP query, I would rather the data weren't distributed at all, because you just cannot be too sure when the information goes off-site. In addition, there is a security issue (that I will be intentionally vague about) with the output from RWOP queries that makes them less than secure when it comes to protecting data. In the next chapter, I will show you how RWOP queries will keep your query designs secret.
Legal Stuff
If your data is valuable , you really should consider making the recipient of the information sign a nondisclosure agreement, which will probably inhibit theft as much as any other security procedure. Of course, if you are distributing the data as a download on the Internet, do not actually expect anyone to read it, even if it is legally binding.
EAN: 2147483647
Pages: 176