3.3 Servers and Hosts
|
3.3 Servers and Hosts
This section concentrates on some of the issues relating to server and hosts on the network. To say that servers and hosts are vulnerable to lapses in organizational security is an understatement. Even the most technologically green computer user, when faced with questions regarding the importance of system security, will reply with something along the lines of, "Well, it's important because someone can get into our computer and do stuff."
To prevent this, we typically will employ network security services. This means that we employ a firewall at the perimeter of our network and perhaps a VPN access point for remote users. Anti-virus software is used to prevent infections from damaging computer code and servers may be kept separate from the rest of the organization. With these steps in place, many network administrators feel that their servers and hosts — and therefore their network — are now secure.
This is commonly the approach taken when a company lacks a coherent security policy. It is lacking in several respects. In a thorough risk analysis, security experts and management will see that user resources are at risk from a number of threats and vulnerabilities. Hosts are vulnerable to threats from the network — and a fairly robust defense plan will reduce the severity of the majority of these attacks. Hosts are also vulnerable to threats that sit at the keyboard. Network security is not much help against these.
Yes, I am implying that an important threat to consider when doing a risk analysis is the user of the network. I commonly bring this up in consulting meetings, only to be met with stares of shock and disbelief. "That may be true elsewhere, but our users would never do anything like that!" is the common reply.
I agree that most users do not "attack" the network out of malicious intent — although research consistently shows that the majority of network security incidents occur from the inside. Most internal threats are well-intentioned users who either make a mistake in the course of their daily business activities or are circumventing secure computing practices to make their jobs easier and more productive. Expensive applications that protect your network against packet-based attacks will do nothing to protect the most likely source of security incidents in your company. Subsequent chapters discuss what can be done to protect hosts against this type of intentional or accidental misuse; but for now, the major point is that the most expensive firewall in the world is not going to help your network when someone sits down at a computer and is able to circumvent its local security safeguards.
Servers are a special point of concern for most organizations. After all, this is where the most expensive data is stored. Many of the same considerations that apply to hosts also apply to servers. Due to their sensitive nature, physical access must always be denied to unauthorized users. Access to the servers themselves from other network administrators must also be closely monitored. What can a company do to protect a server against the intentional or accidental misconfiguration by a network administrator? This is simply another example, that no matter how much we discuss technical controls in this text, it is really a variety of controls applied in depth that provide the best reduction of risk for all systems.
When discussing network hosts and servers, there are a couple of common terms that must also be defined when discussing network security vocabulary. As the lingua franca of networking, these terms will allow you to clearly discuss with vendors and security professionals your specific needs and solutions.
3.3.1 Bastion Hosts
The term "bastion host" is used to describe a host operating system that has had all unnecessary programs and kernel components removed. It is commonly said that a bastion host has been hardened, that it is has been specially configured with security as the primary focus. Bastion hosts often serve as the base operating system for firewalls, VPNs, or IDS devices.
The theory behind a bastion host is that any program, application, or process can contain vulnerabilities that can be potentially exploited by a knowledgeable threat — a theory that has until now seen little reason to be disputed. By removing every element of the operating system not used in actual application of the host computer, the risk is reduced accordingly.
I have heard various arguments as to where the bastion host concept should be applied. Commonly, bastion hosts are specifically configured on systems that will almost certainly face threats — firewalls, DMZ hosts, VPN servers, etc. Some network administrators who apply the bastion host concept to all hosts in the organization use that same argument. If there is no need for the users of host system to use a media player, then the media player applications are removed. Ultimately, where to apply bastion hosts is going to be a function of your final security policy.
3.3.2 The Network Demilitarized Zone (DMZ)
Various sources use different definitions for the DMZ. The strictest definition is the same applied to the border between North and South Korea; a "no man's land" where the land is a buffer and not clearly under the control of either party. A network DMZ is a section of network that acts as a buffer between the external Internet and the internal trusted network (see Exhibit 16). Other definitions of the DMZ include a separate network that contains company Internet servers such as Web servers, external DNS servers, file servers, mail relay, etc. In this case, the network clearly is part of the parent company and under its control but the terminology of the DMZ is often applied in this instance as well.
Exhibit 16: The Demilitarized Zone
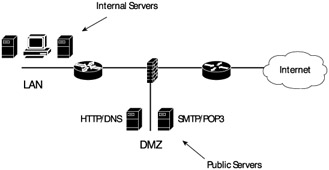
It would also not be uncommon for a company to have a number of DMZ zones that employ both of the above definitions.
Regardless of its application, the DMZ term has evolved into a term that means a section of the network that has access restrictions that are different from the company internal network.
|
EAN: 2147483647
Pages: 119