Healthcare
|
| < Day Day Up > |
|
The healthcare industry is another vertical undergoing a transformation of its information management processes; the industry is moving to a mobile and wireless environment. In fact, the healthcare industry is perfectly suited to the use of wireless technology. Workers in this industry are very mobile; patient data is needed fast and on demand, and the wires for electrical power, monitor hookups, and other equipment leave little convenient space to plug in additional computer equipment. Is it any wonder that an ever-increasing number of hospitals are integrating wireless access into their network infrastructure?
A WLAN, paired with portable computing devices, allows the average healthcare provider to input, view, and update patient data from anywhere within a medical facility, which, in turn, increases the accuracy and speed of each patient's care.
Reduced errors, increased efficiency, and improved patient satisfaction, as well as a growing shortage in healthcare workers, are driving the healthcare industry's adoption of wireless networking technology. IDC, one of the leading global providers of technology intelligence, estimates the use of handhelds by healthcare workers will grow by nearly 40 percent annually through 2005.
The motivation that is fueling this industry's interest in wireless networking technology includes:
-
FDA rules on medication barcoding.
-
Improved accuracy in all levels of patient treatment.
-
Improved patient care through the ability of caregivers to obtain real-time, point-of-care charts, records, and test results.
-
Reduction in time-consuming and costly paperwork.
-
The ability to track medication, testing, and specimen samples through the chain of care.
-
Ensuring that the right medication, in the right dose, is given to the right person, in the right way, at the right time.
-
Voice-over-Wi-Fi capabilities that enable nurse-call communication with doctors.
-
An impressive ROI-WLANA Magazine found that for a healthcare WLAN to produce a positive ROI takes on average just 11.4 months.
While there are many benefits that can be derived from enabling wireless networking at the point of care, there are also challenges associated with operating RF devices in a medical environment. Proper network design, however, can help mitigate such difficulties.
Address 2.4 GHz Interference
Before installing a wireless networking system in a healthcare environment, several issues must be taken into consideration. For instance, because 802.11b and g systems emit and receive radio frequencies in the 2.4 GHz range, some interference with monitoring and lifesaving devices may occur if the network isn't properly designed. Although most interference is relatively benign, causing no serious effects or producing only low-grade interference such as snow on a monitor, there may be more severe interference, which might cause a medical device to produce erroneous readings, to reset, or to jam its communications.
The first step in preparing for a WLAN deployment should be to determine whether there is any potential interference with medical equipment. Some medical devices are not properly hardened for certain radio frequency levels, including frequencies common to wireless networking. This is particularly true of legacy devices. Check the standards and certification labels on all medical equipment. Then design the WLAN around the associated limitations.
A thorough site survey, along with a non-mission-critical test of all components in the system, will go a long way in minimizing the possibility of harmful radio interference. Ask the biomedical engineering department to participate in the test. This department is responsible for testing devices, and for defining the policies and procedures relating to such devices and their usage. Most biomedical engineering departments have a standard test set that is based on known industry issues and the electromagnetic devices that the health system has already installed. Knowing the location of problematic devices is extremely important, since those devices must be brought under the umbrella of the site survey process.
In a medical environment, where mission-critical decisions are being made all the time, avoiding interference problems is worth the cost of hiring outside professionals, especially for the site survey portion of the WLAN deployment. But also consider hiring a project manager who has extensive expertise in WLAN deployments within the healthcare industry. His or her expertise will prove to be invaluable throughout the deployment process.
Certification and Standards Compliance
Wireless LANs are subject to equipment certification and operating requirements established by regional regulatory bodies. So, as part of the WLAN preparation process, you must check to determine if the WLAN's equipment meets all of the local regulatory requirements. For example, if you read the "compliance" label on a Cisco 1200 Series Wireless LAN access point, you would find that it complies with:
-
Standards: UL 1950; CSA 22.2 No. 950-95; IEC 60950; EN 60950.
-
Radio approvals: FCC Part 15.247; Canada RSS-139-1 & RSS-210; Japan Telec 33B; Europe EN-330.328; FCC Bulletin OET-65C; and Industry RSS-102.
-
EMI and susceptibility: FCC Part 15.107 and 15.109 Class B; ICES-003 Class B (Canada); CISPR 22 Class B AS/NZS 3548 Class B; VCCI Class B; and EN 301.489-1 and -17.
-
Other: IEEE 802.11 and 802.11b Microsoft WHQL.
-
Operates license free under FCC Part 15 and complies as a Class B device.
-
DOC regulations.
-
UL 2043.
-
EMI and susceptibility: FCC Part 15.107 and 15.109 Class B; ICES-003 Class B (Canada); CISPR 22 Class B AS/NZS 3548 Class B; VCCI Class B; and EN 301.489-1 and -17.
Medical Electromagnetic Compatibility Standards
As another part of the WLAN preparation process, you must check to determine if the WLAN's equipment needs to meet the Electromagnetic compatibility (EMC) and safety requirements, which are required of medical devices used to provide direct patient care or peripheral support, e.g. telemetry patient-monitoring services, heart monitors, and defibrillators. Electromagnetic compatibility means that any equipment used in proximity to such devices will not cause harmful interference, but can accept harmful inteference, including that which disrupts service.
In the U.S., the Federal Drug Administration (FDA) is the agency that is charged with regulating EMC requirements for medical devices. In that agency's "Guide To Inspections of Electromagnetic Compatibility Aspects of Medical Device Quality Systems," it is stated:
EMC generally needs to be designed into the product. Therefore, the following questions regarding EMC are included in the Design Control Inspectional Strategy (DCIS), dated March 1997:
820.30(c) Design input
For an electrically powered device, where electromagnetic compatibility (EMC) should have been considered in the design, determine the following:
How has EMC been addressed with regard to the device use environment? For example, the interface with other medical devices or the interference from other consumer products?
If complaint or failure data for similar devices distributed by the manufacturer indicated EMCproblems, did the manufacturer use this information in establishing the design requirements for the new device?
Identify any relevant EMC standard(s) used as a part of the design input process.
That same document further states:
AT THIS TIME FDA DOES NOT REQUIRE CONFORMANCE TO ANY EMC STANDARDS. HOWEVER EMC SHOULD BE ADDRESSED DURING THE DESIGN OF NEW DEVICES OR REDESIGN OF EXISTING DEVICES, ESPECIALLY IF EMC INFORMATION HAS BEEN REQUIRED FOR PREMARKET CLEARANCE.
In the EU countries, medical devices manufactured over the last few years must be designed to meet levels of immunity that are defined either in the specific device's standards or in the general standards for EMC. Any device that meets the standards' requirements bears a "CE-mark." (The CE designation, which is French for "Conformité Européene," indicates that the marked product conforms to the relevant EU directives.) Otherwise, manufacturers should be able to provide data about the maximum field strength in the wireless LAN band for safe operation.
Yet, the Medical EMC issue is muddled. Note this quote from the summary of the Medical Devices Agency publication DB9702 entitled, "Electromagnetic Compatibility of Medical Devices with Mobile Communications":
Results from a large study based on 178 different models of medical device using a wide range of radio handsets are available in MDA Device Bulletin DB9702: 'Electromagnetic Compatibility of Medical Devices with Mobile Communications.'" The publication found that overall, "in 23% of tests, medical devices suffered electromagnetic interference (EMI) from handsets. 43% of these interference incidents would have had a direct impact on patient care, and were rated as serious.
The DB9702 publication, however, did state, "No significant levels of interference were detected from cordless handsets, local area networks or cellular base stations." But it was noted that the type of radio handset made a large difference to the likelihood of interference. At a distance of 1 meter (3.28 feet): 41% of medical devices suffered interference from emergency services handsets, and 35% suffered interference from security/porters handsets, but only 4% from cell phones.
You should know, however, that the test didn't specifically test Wi-Fi devices; it included all types of radio components.
A recent set of EMC tests conducted at the Walter Reed Army Medical Center to ensure EMC compliance should set your mind at ease. Biomedical Maintenance conducted an independent validation and verification study in 2002, using different vendors' 802.11b WLAN products: Symbol Technologies' Spectrum 24 and Symbol 2800 handhelds, and Cisco Systems' Aironet 340 and HP iPaq 3670 handhelds.
It initiated the tests by deploying a WLAN in the biomedical lab complex that had the access points set to maximum power output (100 mW). Then the testers used medical equipment-patient monitoring unit, vital signs unit, pediatric defibrillator-with documented EM susceptibility, and assessed interference at varying distances. The tests demonstrated no electromagnetic or radio frequency interference. Thus Walter Reed concluded that, based on preliminary findings, the tested biomedical devices are not compromised through the use of Wi-Fi technology. (It is also noted, however, that comprehensive testing is pending with the FDA to generate a more thorough report.)
Nonetheless, before committing to a wireless LAN installation, a healthcare organization should undertake field strength measurements with the proposed WLAN equipment to ensure they are operating within safe limits. But, since Wireless LAN technology radiates at about 5% the power of a mobile phone, no serious problems should be encountered with a device/transceiver separation greater than 1 meter (3.28 feet).
Many people worry about Wi-Fi interfering with hearing aids or pacemakers. The possibility is remote. The tests that have shown interference could occur have been conducted with cordless and cellular phones held up to the ear, not the typical access point and mobile computing device, which are generally nowhere near a person's hearing aid. As far as the pacemaker is concerned, while it is noted that older pacemakers are subject to interference from microwave ovens, the newer models are not. Furthermore the interference came from systems operating in the 900 MHz or lower bands, not the 2.4 GHz or 5 GHz bands. Also, changes and improvements in pacemaker design have helped to eliminate many interference problems.
To further ease concerns about possible EMC interference, it is noted that in 1996 tests were conducted by Greater Chicago's Ingalls Memorial Hospital to verify that no problems would occur between 2.4 GHz radios and pacemakers. Also, the Ohio State University Medial Center tested Wi-Fi components in its MRI facility and found no interference to the radios or the MRI unit.
However, to ensure safe operation of your WLAN system, obtain the services of a WLAN installation specialist to verify noninterference.
HIPAA
In July 1996, President Clinton signed the Health Insurance Portability and Accountability Act (HIPAA) into law. One of the objectives of that law was to protect patients' health information against unauthorized access.
Failure to secure identifiable health information that traverses your WLAN can have costly consequences. Organizations can be penalized both for failure to adhere to HIPAA standards and for wrongful disclosure of health information. Thus HIPAA has great influence over how a healthcare organization designs and deploys its WLAN. Insurance companies must be confident that identifiable health information is protected from outside interests, and there must be reliable and appropriate access to health information stored in information systems.
To ensure that identified health information is protected, the proper security, privacy and confidentiality measures must be put into place. A healthcare facility's WLAN must use encryption and advanced security solutions, such as virtual private networking. It is also imperative that the site survey ensures that the WLAN's signals do not "leak" out of the intended coverage area, either inside or outside the facility.
Use as a guideline the advice set forth in Chapter 17 to help you develop a security program. Also, to ensure that patient confidentiality is maintained, it must be decided exactly who should have access to the WLAN, from what device(s), and what information can be obtained via the WLAN.
WLANs are Flexible
Because wireless networking is both flexible and scalable, a healthcare facility can take a modular approach to deployment rather than commiting to location-wide coverage immediately. For instance, a WLAN could be deployed in a single department, such as a trauma center or the facility's emergency room. As network use increases, you can grow the system to cover a ward, a wing, or even entire buildings. Eventually you could even extend the WLAN across every square foot of a medical campus.
Mobile computing devices are more susceptible to theft than their stationary counterparts. Thus precautions must be taken.
First, all patient information stored on these devices must be encrypted. Next, the devices themselves should be password protected. Then, end-users must understand both their obligations to protect the information stored on their device, and what the device is capable of accessing.
Finally, wireless security policies and procedures must be developed. Although it is recognized that the policies and procedures must be specific to the healthcare environment, use the "Wireless Security Policy" section in Chapter 17 as a starting point. Then ensure that all end-users agree to comply with whatever security policies and procedures that are put into place.
All Wi-Fi certified wireless solutions should seamlessly integrate with existing wired solutions, and work smoothly with all wireless equipment built upon the same 802.11 specification. However, if you initially implement wireless gear that provides added functionality such as Quality of Service and/or security, you may be locked into using only the initial vendor's equipment. That is because the vendor, in all likelihood, used proprietary solutions to provide the additional functionality.
Building Bridges
If your healthcare facilities include buildings that are not on the main campus, such as emergency medical centers and/or outpatient treatment locations, you can seamlessly connect them to the core network, using wireless bridge technology as discussed in Chapter 9. Wireless bridges save enormous time and cost incurred for dedicated lines or leased lines. For example, the Cisco Aironet 350 Series wireless bridges provide highspeed, long-range, building-to-building wireless connections.
Case Studies
Memorial Medical Center, Springfield, Illinois
Memorial Medical Center is the teaching hospital for Southern Illinois University School of Medicine. About 3000 of the hospital staff need daily access to patients' medical records. In September 2002, in an effort to improve patient care by providing fast access to standardized information, the hospital began work on a program to introduce electronic records that could be accessed wirelessly by physicians, nurses, and other hospital staff.
The hospital administrators understood that by providing the staff access to patient information as needed, no matter the location within the hospital grounds, it could eliminate error-prone paper documents, prevent unintended drug interactions, eliminate illegible handwriting through the use of electronic forms, and ensure that procedures were instantly documented and that they followed hospital, insurance, and government regulations.
At the outset, Memorial Medical planned to offer 802.11b wireless access just in locations that were hard to wire or where the staff was very mobile, such as in patient wards. But CIO O.J. Wolanyk argued that it made more sense to make the entire hospital wireless-including the parking structures and cafeterias, so doctors and nurses and other personnel could access information from any location within the facility. He also wanted the full coverage so the hospital could later implement Voice-over-Wi-Fi phones.
The hospital administrators gave their approval to Wolanyk's $900,000 wireless-everywhere project. When fully implemented, the WLAN will serve not only medical wards, but also other areas including accounting, billing, and human resources.
"Memorial's need for a wireless LAN could not be more mission-critical," said Wolanyk. "We were running out of places for PCs and had to reduce the $770,000 we spent annually on scanning medical records. The wireless network is the predominant means by which we access medical records. We are not experimenting here; we had to be confident that the solution would meet all our expectations."
Initially, Wolanyk thought there would be a need for around 300 access points, based on the square footage of the hospital. But after an outside firm performed an extensive site survey, it was determined that, with optimal access point placement, the facilities would need fewer than 150 access points.
After evaluating a number of vendors, Wolanyk and his staff decided that Cisco wireless access points, Cushman antennae, and ReefEdge Connect System (a server with Edge Controllers), had the most to offer. It was also determined that the wireless network would have three levels of security to ensure that patient data is protected, and that only authorized users can log onto the network. Those three levels consist of Windows NT Active Directory authentication, policy-based firewall access (to ensure that users get only access to the information they are allowed to see), and 128-bit Dynamic IPSec 3-DES data encryption.
The infrastructure was designed to provide a secure system with session persistence across subnets to enable seamless roaming between access points. The ReefEdge Connect System also ensures concurrent access to medical records by staff, and allows administrators to remotely manage the wireless LAN. Furthermore, the WLAN meets federal regulations set by the Health Insurance Portability and Accountability Act (HIPAA), according to Ajei Gopal, ReefEdge's CEO.
Everyone is pleased with the new WLAN set-up. The fully operational WLAN can directly support all tertiary hospital services including cardiology, cancer, burn, orthopedics, pharmacy, radiology, medical laboratory, and trauma.
Even though the hospital does not expect the system to greatly affect its per-patient care costs, Wolanyk is enthusiastic about the project. Having better, safer operations will be payback enough, he says. Wolanyk also "wanted to experience this myself." Toward that end, he uses a laptop computer as his primary computing device so he can work throughout the hospital. Since he has no office, he connects wirelessly or via Ethernet jacks just like the hospital's 550 on-staff physicians and 2400 employees. Those care-givers access the wireless system on a regular basis via laptops, PC tablets, and handheld computers as they move about the hospital's facilities. Even PC workstations are equipped to access the wireless network.
The ReefEdge Connect Server and Edge Controllers work together to ensure high availability, even in the event of network connectivity failures. To provide redundancy Memorial deployed standby Edge Controllers (EC100 and EC200) to monitor the primary ones. In the unlikely event of a failure, a standby Edge Controller can automatically reroute wireless traffic through a redundant path to the network in a matter of seconds, with virtually no disruption of user sessions.
That's not the end of Memorial's foray into wireless connectivity. Recognizing that doctors are not technology adopters, and realizing that it's critical that the care givers find the system easy to use, and that it actually helps to make patient care easier to deliver, Wolanyk asked doctors to help design the applications and work methods.
Wolanyk also wants doctors and hospital staff to recharge their devices easily without having to find an open power jack. He is planning on installing custom-built power racks throughout the hospital, so multiple devices can be recharged from one power outlet, instead of every recharger needing its own power jack.
Physicians typically affiliate with more than one hospital in order to better serve their patients. So Wolanyk also works with the other major hospital in the area in an effort to standardize medical information systems, including the wireless access. If and when the project is completed, physicians can treat patients wherever they are located and not worry about changing procedures or technologies.
Still to be decided, at this writing, is how the hospital will connect to the outpatient care facilities across the street. Although the staff that works in the main hospital doesn't often visit the outpatient building, and vice versa, Wolanyk would like to have both on the same network. The holdup is that the hospital must work with other tenants in the outpatient building, since several have wireless networks that overlap the outpatient unit's space.
St. Luke's Episcopal Hospital, Houston Texas
St Luke's in Houston, Texas, is located in the heart of the world's largest medical center. The hospital's wireless network originally consisted of non-802.11b Proxim access points (APs) and Cisco Aironet 802.11b APs. (The hospital is phasing out the Proxim APs in favor of an all-Cisco 802.11b WLAN.) Users connect to the network through Dell Latitude mini-laptops and NEC MobilePro handheld devices. The laptops run on Windows 2000 and NT, and the handhelds use Windows CE. All are equipped with Cisco Aironet 802.11b wireless NICs
The APs are distributed throughout several hospital buildings, and are used to access a variety of network applications in many different areas. The wireless computing devices are employed to obtain medical data as the hospital's staff make their rounds.
According to Gene Gretzer, senior analyst and project leader for the wireless rollout at St. Luke's, the WLAN was originally deployed in January 1998 in a single building using Proxim access points. Yet, while the WLAN was supposed to improve the efficiency of care at the hospital, it sometimes had the opposite effect. For instance, once the staff started using the wireless network, the staff noticed that the wireless signals didn't always maintain a constant connection.
The reason for signal fluctuation varied from ongoing construction within the building, to medical equipment, to roaming between floors and from building to building. Each time a connection was dropped, the user would have to get back within the range of a wireless access point, reconnect to the network, go through the log-on and authentication process, start the application(s) again, and re-enter whatever data was lost in the process. This wasn't what the IT department or the hospital administrators had in mind when they decided to go wireless. In fact, with the WLAN's then infrastructure, there were disruptions in many hospital-related activities.
Time and attention to detail are everything, and staying connected is absolutely essential. Is it any wonder that when the hospital surveyed the staff on their WLAN experience, the staff identified disconnected wireless sessions as one of their primary user complaints?
"People using the handheld devices had trouble maintaining their sessions walking around the floor," says Gretzer. "[The operating system] had a tendency to drop the connection." Naturally, this situation frustrated busy doctors and nurses, who resented both the waste of time and the distraction from patient care.
In addition, the hospital's physical construction itself caused problems with wireless signals. The walls in the original building were built using chicken wire, which interferes with radio waves. Some patients' rooms were also located in pockets that had weak radio signals. Nurses and doctors working in these rooms sometimes had to step out into the hallway to reconnect. Microwave ovens in the kitchenettes on each floor also occasionally caused interference.
To remedy the problem, St. Luke's turned to NetMotion Wireless Inc. and its Mobility Server solution. Mobility is a software solution that provides persistent application connection for wireless devices. Gretzer deployed Mobility software to 20 Microsoft CE client devices in March 2000.
The Mobility software maintains the state of an application even if a wireless device moves out of range, experiences interference, or switches to standby mode. Once users come back into range or switch into active mode, they can resume the application where they left off, without having to login or reenter data.
The product consists of a Mobility server and Mobility agents for the individual client computing devices. The Mobility server, which runs on Windows NT/2000, acts as a proxy between the clients and the network server that runs the applications. The server solution manages each application session to keep a continuous connection between the wireless device and the application server on the wired network, and provides several security features, including encryption and basic firewall functions. These features help to protect sensitive patient data.
The Mobility clients are then able to communicate with the Mobility server via UDP (although the Mobility software supports both UDP and TCP, and can use either protocol to communicate with applications). "We encapsulate application traffic using UDP to avoid many of the commonly understood issues surrounding the use of TCP in a wireless environment," says Emil Sturniolo, chief scientist at NetMotion Wireless. Those issues include:
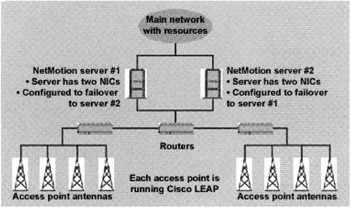
Figure 15.1: St. Luke's WLAN. The mobility software is deployed on a proxy server and individual mobile computing devices. The proxy server brokers IP addresses for the client computing devices, maintains network and applications sessions, and acts as a firewall between the wired and wireless networks. Graphic courtesy of NetMotion Wireless Inc.
-
TCP will drop its virtual circuit when a wireless client goes out of range of a radio signal, forcing the user to login, reconnect to the network, and restart whatever applications were open.
-
TCP attributes packet loss to network congestion or packet collision, even when the cause is a device going out of range. Under this assumption, TCP waits a specified length of time before resending the packets, which NetMotion says can degrade performance.
-
When retrying to send lost packets, TCP may send data that the client has already received, thus eating up bandwidth unnecessarily. This may not be an issue on a 100 Mbps wired network, but bandwidth is at a premium on more constrained WLANs.
Sturniolo says that the Mobility software employs a guaranteed delivery system much like TCP, so that if a frame is lost, it gets retransmitted, shielding the application from network errors. Just how NetMotion does this is confidential.
In March 2002, the wireless project expanded to all three of St. Luke's buildings, but with the expansion came a host of new problems. "We changed from having the wireless on a single Virtual LAN-a single IP segment-to a multi-facility network," says Gretzer. The result was that when a user roamed onto a new segment of the WLAN, the client device would be assigned a new IP address, causing it to lose its current session. For undisclosed reasons, the hospital didn't deploy access points in the hallways that connected the three buildings. That served to increase the incidents where a loss of signal incurred as users moved to a new building.
Gretzer once again turned to NetMotion to help alleviate its mobility problems. Besides maintaining application persistence, NetMotion has a system for managing the IP addresses of mobile devices.
Each Mobility client has two IP addresses-a Point of Presence (POP) address and a virtual access. The POP address is the address assigned to the client by whatever WLAN segment it happens to be in at the time. If a user roams onto a new coverage area, it gets a new POP address. It is typical for roaming users to change POP addresses numerous times while on a shift.
Each client device also has a virtual address on the wired network. The Mobility proxy server tracks both the virtual address and POP address for each client, and acts as a broker between the wired and wireless networks. When the Mobility server gets data from an application server on the wired side, it forwards those packets to the client's POP address, and reverses the process to send packets from the client back to the application server.
Without this feature, clients who roamed onto a new WLAN segment would have to reconnect to the network every time the POP address changed. With NetMotion at the helm, transitions are invisible to the end-user, since the network and application connections are maintained at all times. NetMotion clients obtain their IP addresses from standard DHCP servers.
NetMotion is also assisting St. Luke's as the hospital swaps the Proxim APs for access points from Cisco. The reason? Well, according to Gretzer, "Proxim's pipe is only 1.6 Mbps and Cisco's is 11 Mbps-nearly ten times faster," and the hospital's wired network infrastructure is Cisco-based.
In the meantime, NetMotion plays a vital role in the interoperability of the two vendors' products. Support for both wireless systems once meant that nurses had to switch between devices as they moved about. On floors with Proxim access points, they used devices installed with Proxim radio cards; on Cisco floors, they could only use devices with Cisco cards. In moving from floor to floor, staff members would have to log out of one device, then log back in on a new one.
"With NetMotion, you just need two radio cards in one laptop," says Gretzer. "The Mobility system lets nurses and doctors transition seamlessly between floors that have the old Proxim and new Cisco." Thus staffers can continue to use the same machine, regardless of the technology in the APs.
Let's not forget security. If the thought of sensitive medical information floating blithely through the ether causes your heart to palpitate, you're not alone.
"Of course security is an issue," says Gretzer. "The Cisco network we put in uses Lightweight Extensible Authentication Protocol (LEAP), which is basically just a rotating Wired Equivalent Privacy (WEP) key, and WEP has been broken, so we wanted some extra layers of security."
NetMotion's Mobility software provides two of those extra layers. First, all the traffic between the Mobility clients and the Mobility server is encrypted using the Advanced Encryption Standard (AES) at 128-bits. Second, the Mobility server also functions as a basic firewall, separating the WLAN from the wired network.
"We treat the wireless side of the network as hostile," says Gretzer. "The mobile devices do not have access to the corporate network. They have to go through the Mobility server." The server itself will only talk to clients that it recognizes.
Gretzer says that he also employs other methods to secure wireless traffic. While he wouldn't give details, he did say that a security company, which performs penetration tests among other measures, regularly audits the hospital's network.
"We also do our own wardriving to see what our vulnerabilities are," says Gretzer. "You can receive a signal in the parking lot, but with the multiple layers of security we have, you can't get any usable information. In fact," he adds with a laugh, "we end up finding out everybody else's vulnerabilities. We're the only ones implementing higher-level security."
However, one prominent feature of the NetMotion system-its ability to maintain application persistence-can up the system's overall vulnerability quotient. Here's an example: suppose a nurse entering patient data steps away from the device in the middle of a session-anyone who picks up that device would have authenticated access to the application and the records stored there. (This applies to wired PCs deployed in the hospital as well.) And while Gretzer realizes that this is a risk, he says that the risk can be minimized through careful management. First, to enter or change data, users have to enter their user name and password again. Then, sensitive applications are set to time out after a specified period, if they're left open but unused. The staff has been trained not to leave sessions up and running, and to question anyone who picks up a laptop or handheld, if they don't recognize that person.
This kind of risk is familiar to every administrator. "Users want access, access, access and don't care about security, but we have to consider security and then functionality," says Gretzer. "There's a fine balance in that relationship."
The hospital has 21 floors dedicated to patient care, but not all of them have been wireless-enabled. Floors without the WLAN are still using paper charts. Gretzer laments that the transition to a paperless hospital is taking longer than expected. What was supposed to be a three-year project is stretching into five. One reason for the delay is simply a matter of convincing staff members to accept a more computerized working environment, and then training them to use the devices properly.
"We anticipated a faster rollout because we didn't see the barriers to the staff accepting the devices," says Gretzer. "A lot of nurses and doctors are set in their ways. They sometimes have difficulties adjusting to the new system."
Regarding performance, Gretzer says that the NetMotion software functions perform as advertised. "We haven't found any applications that don't work with NetMotion. We're getting the performance we need." And although proxy servers sometimes have a reputation for adding latency to a session, Gretzer says that any overhead that Mobility might be adding is negligible. This is particularly noteworthy considering that the proxy server encrypts and decrypts all of the wireless traffic, in addition to maintaining application and connection states for its clients.
In one case, nurses using the Mobility software complained of poor performance. "We turned off AES encryption because we assumed that may have been the problem," says Gretzer. In fact, the problem was with the radio cards. "A card was trying to hold onto a signal from a transmitter two floors above," he explains. After tuning the card to only talk to transmitters on its own floor, the problem went away. "We turned AES back on and the users didn't even notice a difference," says Gretzer.
There was also some problem with intermittent functionality of the Mobility proxy server, which necessitated a visit from one of NetMotion's senior developers. However, like any good administrator, Gretzer has a backup server standing by. While NetMotion supports failover, users still have to log back into their applications because the server's address changes. "It's a nuisance," says Gretzer, "but computers break down. The client computing devices know that if they can't talk to the main server, they switch to the backup."
Gretzer's has a couple of gripes associated with wireless networking. One is that if a staff member says his or her mobile computing device is running slow, it is sometimes difficult to determine if it is the computing device, the network connection, or the connection from the access point to the server. Normally, he would send a trace packet from the device to the server to see where the problem was, but his network management tool, Lucent's VitalAgent, doesn't work well with WEP or other data encryption methods. According to NetMotion, because WEP encrypts traffic from Layer 2 and up, traffic sniffers have difficulty tracking packets based on IP addresses because they're encrypted. Gretzer is looking for a monitoring tool that addresses that problem.
The other complaint is that his IT people must physically touch each laptop and handheld in order to deploy and upgrade the Mobility agents. He is evaluating different applications for wireless device management.
When asked about return on investment, Gretzer was hard-pressed to come up with an amount. "When you consider what the hospital staff does, it's hard to get a dollar figure." Rather than save money, he says that the point of the system is to make life easier for the staff. An internal report, however, estimates a 15 to 20 percent increase in efficiency with the wireless system. For instance, before the wireless network was installed, staff members would spend 30 minutes uploading new patient records to a laptop in the morning, and another 30 minutes downloading those records at the end of the evening. Now that the staff updates records in real-time, that hour can be spent on more important tasks.
According to Gretzer, the NetMotion system adds to this efficiency because staff members don't continually reattach to the network or start over when an application session is interrupted.
In terms of hard costs, he says that the NetMotion system has saved St. Luke's from having to add access points to transitional areas, such as the corridors that connect the hospital's three buildings. "It's nice to be able to close your laptop's lid, walk to the next building, and open it up and you're still where you left off," says Gretzer.
In the hurried environment of a hospital floor, time is at a premium for busy nurses and doctors. Technical glitches that interfere with their ability to provide quality patient care are unacceptable. NetMotion ensures that St. Luke's WLAN maintains application sessions and network connections, even as users move out of range or place devices on standby. This application and connection persistence improves productivity and allows medical professionals to focus on the most important task at hand: caring for the patients.
Gretzer is so pleased with the results that he's prescribing a Mobility client for every wireless device that accesses patient records. "As long as the applications work as needed, my users are happy," he says. For a network administrator, that's the best medicine.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 273
- The Effects of an Enterprise Resource Planning System (ERP) Implementation on Job Characteristics – A Study using the Hackman and Oldham Job Characteristics Model
- Distributed Data Warehouse for Geo-spatial Services
- Data Mining for Business Process Reengineering
- Healthcare Information: From Administrative to Practice Databases
- Development of Interactive Web Sites to Enhance Police/Community Relations