Chapter 7: Designing Security for Internet Information Services
|
| < Day Day Up > |
|
Internet Information Server (IIS) is a group of services that host web communications. This includes the World Wide Web Publishing Service that uses the HyperText Transfer Protocol (HTTP), File Transfer Protocol (FTP), Simple Mail Transfer Protocol (SMTP), and Network News Transfer Protocol (NNTP), all of which allow you to communicate with clients or other servers that support these protocols. These services support many of the functions that we use daily to retrieve and send information through the Internet. Because these services are generally connected to the Internet or host important applications for businesses, they are the target of many types of attacks. These attacks include denial of service (DoS) attacks, defacement of websites, and the use of viruses and worms designed to take advantage of programming or administration mistakes in IIS. You should make sure you focus on IIS when designing security. In the following chapter we will look at securing IIS. We will explore the strategies used in creating security and monitoring policies for IIS. We will also discuss the authentication options when connecting to IIS. Finally, we will look at techniques that can be used when designing for a content management and update.
| Note | Securing domain controllers, network infrastructure servers, file servers, and POP3 mail servers is covered in Chapter 8, “Designing Security for Servers That Have Specific Roles.” Securing Terminal Server is covered in Chapter 10, “Designing Secure Network Management Infrastructure.” |
Designing Security for Internet Information Server
When designing security, you will begin by finding out the business and security requirements with respect to the use of the Web by a company and its applications. You will use the information to determine the baseline of services, permissions, and applications to install on the various IIS servers in the organization. You will then decide what the minimum services required for each website hosted on the IIS server are and prohibit the services not required.
Designing an IIS Baseline Based on Business Requirements
Many organizations use the Internet to generate cost savings by expanding their applications to include partners or to make it easier for employees to work. They can see these cost savings wiped out by a security incident or two. Therefore, you will need to analyze your organization’s business, application, and security requirements carefully. You will then need to establish a baseline for security.
Requirements can usually be determined by asking a series of questions. The following list includes some examples of the types of questions you should ask:
What is the organization’s tolerance for lost data? You will need to determine how much data the business can afford to lose versus the cost of backing up the data. You can obtain systems that do real-time backup if you cannot afford to lose any data, but these systems come at a cost. Some organizations may determine that their nightly backups are just fine and they can recreate the day’s information in case of a loss at a cheaper cost, or that taking out an insurance policy would be cheaper.
How important is it that the data is kept private when it is sent across a WAN link? You will need to discuss with the business whether the data contains sensitive or secret information. If this is the case, you will need to consider the network connection’s vulnerability, which you can use to determine if you need encryption and the strength of encryption required.
What are the requirements for controlling access to the data? You will need to consider what groups of users or applications should have access to the data and then what types of permissions they need. You will want to give them the minimum permissions required to accomplish the tasks for which they will use the data.
Are there groups of employees that require different levels of access to a website? You will want to create groups for these employees and use either different virtual directories or URL authentication to control access to parts of the web application. You can secure virtual directories with NTFS permissions or through the web.config <authorization> section for ASP.NET applications.
What means will users use to update the content? You will need to determine the requirements that the organization has for updating content on a website. This will require determining the security, application, and ease of use preferences that are in the organization.
What level of auditing will be required? There are many things that could go wrong in relation to security. For example, someone can exploit a bug in your web server software or web application, or one of your server administrators could be stealing information and selling it to your competitors. You can determine whether or not a break-in occurred and what action was taken by using auditing.
Will the server be able to see the Windows domain controller or will another server be used for authentication? You will need to analyze the network architecture to determine if the web server will be able to communicate with the domain if you need to authenticate users with your organization’s domain. If you determine that this is not possible, then you will need to configure a solution that uses Remote Access Dial-in User Service (RADIUS), a separate domain, or the local Security Accounts Manager (SAM) database that redirects or contains only the accounts that need to authenticate against the web server.
Will the IIS server be located on the network, and if so, where? You can place the IIS server in the perimeter network, internally, externally, or you can outsource hosting and not even install the server on your network. You will need to determine where it is located and take the proper security precautions to protect the server.
What services are required by the applications that the business runs? You will need to analyze the applications that the business runs and determine the minimum amount of services required on a given server to support the applications. This will minimize the number of services that can be attacked on the server.
Is the risk of enabling the service outweighed by the value of the application to the business? You will also need to look at the services that an application requires and determine if the risk associated with enabling the service outweighs the convenience, cost savings, or features of using the application.
What is the means to protect the server from viruses? You will need to install adequate virus protection on your servers to help guard against viruses, worms, or Trojans that may be uploaded to your servers.
How will software updates be installed? You can use a manual/custom mechanism or Microsoft’s Software Update Service (SUS) to make sure that the services, applications, and operating systems that you are using are kept up-to-date to guard against vulnerabilities due to bugs in the software. You will learn more about keeping servers patched and up-to-date in Chapter 9, “Designing an Infrastructure for Updating Computers.”
These are a few of the questions you should ask when evaluating the business and security requirements for IIS. After you have gathered requirements, you will generate a baseline for the IIS servers that are installed or will be installed in the organization. You will need to consider the following:
Set suitable access control lists (ACLs) on Web content. You should consider the minimum permissions with regard to content. You will need to pay attention to permissions on log files to prevent alteration or revealing too much information. If you enable Write permissions, you should enable disk quotas to prevent too much space from being used if there is a problem. You will need to make sure the scripts and executables have the necessary Execute permissions. You can make managing security on your web server easier by creating directories for common content and setting permissions on the directories. You should also define groups based on the roles or groupings that represent the various tasks that people need to do on the website. For example, if managers need access to content that regular users can’t access, you would have a managers group and a users group. You would then apply the permissions to the groups.
Install only components that are being used by the IIS server. Software that is installed but not used is usually not maintained or set up properly. This makes it a great target for attacks. Having extra services running also increases the odds that you will be attacked through a bug in one of the components. Also, an attack can be difficult to track down because generally you are not logging information properly.
Enable only the services being used by a website. An IIS server may host more than one website. Some websites may require Web Distributed Authoring and Versioning (WebDAV), Active Server Pages (ASP), or common gateway interface (CGI) scripts to run, while others will not. You can disable application extensions on an individual website basis through the Web Service Extensions section of the IIS Manager. You should make sure only the extensions required by the website are enabled.
Evaluate the rights of accounts used by IIS and applications. IIS uses many accounts to run applications, log on anonymous users, and run its own services. You will need to evaluate what permissions the following accounts have:
-
IUSR_ComputerName This is the default account used by everyone with anonymous access to the server. Scrutinize the permissions on this account closely.
-
Network Service This is a new account that was created for Windows Server 2003 to allow the services of IIS and other services to run under an account with the minimum rights granted. This allows you to avoid using the Local System account, which has administrative rights to the server.
-
ASPNET ASP.NET applications run under the context of this account.
-
IWAM_ComputerName This account is used by ASP and Internet Service API (ISAPI) applications that are running in isolated processes. You will need to evaluate this account if you are running in IIS 5 Isolation mode to support legacy applications that don’t function properly under IIS 6.
You will also need to pay attention to accounts used to access services like databases and directories on the network. In addition, you should make sure that your services are not running in the security context of a domain account; if they are, it will be easier to obtain domain account passwords if the server is physically compromised. Make sure all accounts that are used have the minimum amount of rights and permissions necessary. It is usually easier to use Group Policy objects (GPOs) to apply the permissions consistently and repeatedly.
Use secure communication mechanisms where appropriate. Determine what connections are vulnerable to eavesdropping and use appropriate encryption mechanisms over the connection. The most common mechanism for HTTP applications is Secure Sockets Layer (SSL). You should choose transport layer IP Security (IPSec) for encryption of protocols like FTP and NNTP. You can choose to use Transport Layer Security (TLS), which works like Secure Sockets Layer (SLL), to establish an encrypted SMTP session.
Decide what protocols you need and filter anything else. You will need to evaluate the protocols you are using on the server. This means not only evaluating the application’s protocols (like HTTP and SMTP), but also looking at the protocols used to manage the application and to update the content of the application. You will then apply TCP\IP packet filtering or, for more security, IPSec filters to deny access to the server for protocols that are not used. Filtering on the server should not take the place of a good firewall; it is an added precaution. You never know when something will be configured improperly or a bug will be discovered.
You should use IPSec filters to enhance the level of security on your vulnerable IIS servers, like those serving content to the Internet. In its Windows Server 2003 Security Guide, Microsoft recommends that you apply the following IPSec filters:
| Service | Protocol | Source Port | Destination Port | Source Address | Destination Address | Action | Mirror |
|---|---|---|---|---|---|---|---|
| Terminal Services | TCP | Any | 3389 | Any | Me (localhost) | Allow | Yes |
| Domain Member | Any | Any | Any | ME | Domain Controller | Allow | Yes |
| HTTP Server | TCP | Any | 80 | Any | Me | Allow | Yes |
| HTTPS Server | TCP | Any | 443 | Any | Me | Allow | Yes |
| All Inbound Traffic | Any | Any | Any | Any | Me | Block | Yes |
These settings act as a basic starting point for an IIS server hosting web pages. Depending on your administration requirements, application requirements, and content update strategy, you may need to apply additional filters. You may also want to tighten up the communication to domain controllers in this recommendation by only opening the appropriate ports for Active Directory, RPC, DNS, and other protocols running on the server.
Remove any samples or demonstration applications. The sample applications are meant to show a developer how to solve some particular problem or use a certain technology. As a result, they are generally not secure and can be the source of attacks that are relatively easy to make on your infrastructure. They should be removed from production servers.
Enable logging on the server. Logging is how you track what is happening on the server. You will be able to use logging information to report trends about usage and performance. It can also be used after a security incident to determine the damage done to the server or as evidence to prosecute the attacker. IIS supports protocol logging, HTTP.sys logging, Windows auditing, and monitoring with System Monitor.
Install and configure UrlScan. You can install UrlScan 2.5 on a Windows Server 2003 service with IIS 6 installed. UrlScan is an ISAPI filter that screens and analyzes URLs and requests before IIS has a chance to process them. IIS 6 incorporates features that make UrlScan less necessary than with previous versions of IIS. You still need UrlScan if you want to do the following:
-
Filter URLs based on their length
-
Filter HTTP commands, which are called verbs (GET, POST, PUT, SEARCH, BPROP to name a few)
-
Remove the server header to conceal the identity and version of the web server and operating system.
You can download UrlScan 2.5 from Microsoft’s web site. They move it around from time to time so it is easiest just to search for UrlScan 2.5. Alternatively, you can install it from the Windows Security Update DVD in TechNet. Once installed, UrlScan will create a directory called urlscan that will include the urlscan.ini file with the settings of what you want to filter and what you want to allow. It will also contain the log files for UrlScan, which will have information about what was blocked by UrlScan and why it was blocked. You can use these log files to troubleshoot applications that are having trouble connecting to the server.
Install and configure Authorization Manager. Managing permissions for applications at a granular level through New Technology Filesystem (NTFS) can be tedious and difficult. IIS 6 introduces the ability to provide authorization to URLs. This means that you can assign a group or user access to applications, or parts of applications, and not have to worry about the NTFS permissions. You can use Authorization Manager to provide for this role-based access control. You will be able to control access to your web application through URLs, instead of relying on NTFS permissions.
Create a plan to keep the server up-to-date. Keeping up with security updates on a server with IIS is very important. You can use the automatic update service to directly connect to Microsoft and update the server, or if you need more control, you can install Software Update Service. Just make sure you have a plan to keep up with the critical security updates. For example, the patch for the Code Red worm came out a month before the worm struck, yet the worm was able to infect an estimated 250,000 servers.
| Note | See Chapter 9, “Designing an Infrastructure for Updating Computers,” for more information. |
Create a plan to back up all of the server content. The successful implementation of a backup plan can help you recover the server quickly in the case of a security breach, like a website defacement. You will need to consider a plan for backing up the log files on a regular basis and determine how much information you will need to keep.
| Note | See Chapter 1, “Analyzing Security Policy, Procedures, and Requirements,” for more information. |
Create a plan for updating content on the server. You will need to decide how new content will get moved to the server. Moving content can introduce security issues if it is not carefully considered. You should understand what protocols are available and what the network infrastructure will allow. We will discuss this in more detail later in the chapter in the section titled “Designing a Content Update and Management Strategy.”
You must make sure that the IIS baseline does not have conflicting settings. For example, suppose you install UrlScan 2.5 and design rules to filter URLs that do not meet your application or business needs. You carefully analyze the applications used by the business and determine a safe URL length. You also decide that FrontPage Server Extensions are dangerous and filter URLs that contain the letters vti, which are in URLs that are used by FrontPage Sever Extensions. If the business has decided to use Microsoft Visual InterDev to update its website based on ASP, then you will have broken its publishing mechanism. In this case, the security and business requirements may conflict. If the security requirements conflict with the business requirements, you will need to determine which is more important, typically by considering the potential costs of changing them. For example, you would compare the cost of upgrading software and training users with the cost of a potential security breakdown. This could be an easy decision if there was already a plan to update the tools or technology, say to Visual Studio .NET with ASP.NET, in which case you can make sure the tools support features that will work with your security plan.
You should take advantage of tools that Microsoft provides to aid in enforcing and verifying your baseline. You can use the Group Policy File System node to create a policy for the permissions you decide are appropriate for your website. The policies will be applied to the IIS servers. You can use the Microsoft Baseline Security Checker to verify that you are up-to-date with your patches on the server. You can use UrlScan to guard against attacks that use a URL by filtering based on the length and content of the URL. Just make sure that, if your business requirements change, you look at the implementation in your tools to determine if you need to change them.
In the Design Scenario “Designing a Baseline Based on Business Requirements,” you will use the business requirements to determine the security baseline for an IIS server.
Design Scenario: Designing a Baseline Based on Business Requirements
Background
Wonder, Inc. is a company that manufactures and sells electronics and electronic parts. Its corporate headquarters is located in Denver, Colorado. The company has retail outlets in many cities through the U.S. It also sells components to other companies. It either sells stock components or works with a company to manufacture and provide the component. Wonder, Inc. has a sales staff that handles this work. In addition, each of the retail stores sell stock electronic components to the public.
Interviews
Chief Information Officer All content sent between the field and corporate is done over network connections that are not secure. This content can contain sensitive information, like sales projections or pricing formulas, and should be protected. We also need to track individual access to the applications.
Direct Sales Manager We need to have access to portions of the sales and customer management application in the field. These applications are web applications that use the user’s network logon to authenticate them.
VP Retail Sales We need access to information about inventories in our store and other stores to locate parts a customer may request. We only need access to POS information for the store itself.
-
Question: What are the business requirements for the web server? Answer: You would need to authenticate user s of the website to meet the requirements that they need to track access to applications and have access to the sales and customer management application. You would then be able to authorize users to have access only to the content or applications they are allowed to use. You would also need to enable logging on the server to meet the CIO’s requirement to track indi vidual access to the applications. You will also encrypt the communication o ver the WAN links to protect sensitive information.
Designing for Minimum Required Services for Websites
One of the reasons many servers are infiltrated is that they have services running that they do not require. These services may have been installed when they were needed or simply because someone was afraid that something would break if the service was not installed. Therefore, when you are designing for a secure IIS implementation, you should consider what services you will require on your website. You will need to decide what services and web server extensions (ISAPI applications or filters) must be installed or which ones will be allowed on the server.
For example, if have made a business decision to support the web portion of a line-of-business application written with Active Server Pages (ASPs), you will need to install and start the World Wide Web Service on the server and enable ASP to run on the server.
You can decide what services to include by analyzing the security baseline generated by your business requirements. You will first need to make sure that the minimum services are installed on Windows Server 2003. Then you can decide what services you will install for IIS. Finally, determine the minimum Web Service Extensions that your website will require.
Real World Scenario: Code Red Worm
The Code Red worm was the first big worm to attack IIS and has inspired many derivatives, such as the Nimda worm and Code Red 2. This virus took advantage of a buffer overflow error in the Index Server service. A buffer overflow attack attempts to exploit a program that does not validate a text value, like a URL, for length and allows a larger value to be placed in memory than the amount of space allocated. For example, the Code Red virus uses the following URL to exploit IIS:
/default.ida?NNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNN NNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNN NNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNN%u9 090%u6858%ucbd3%u7801%u9090%u6858%ucbd3%u7801%u9090%u6858%ucbd3%u7801%u9090%u909 0%u8190%u00c3%u0003%u8b00%u531b%u53ff%u0078%u0000%u00=a
The N in the URL is taking up space to overflow the string buffer (an array of characters with a finite length), and the %u represents binary commands that the sender wants to execute. Sub-sequently, the program will not allocate enough space in memory to store a text value, which means that the additional information will “break the stack” and insert the value starting at the %u9090 as the next command on the stack to execute. This value represents code that will run with the permissions of the service running the code (administrator equivalent).
As a result of the buffer overflow, the sender of the Code Red worm is allowed to execute arbitrary code with the Local System Account privileges. This is dangerous because it means that the attacker has complete control over the infiltrated system. If you have IIS 4 or IIS 5 servers that have Index Server installed they will be affected by this vulnerability unless they are patched. The Code Red exploit can occur even if the indexing server service is installed but stopped or disabled. You will need to make sure that you do not have the indexing service installed.
This is an example of why you need to make sure that you install only the products you are using. If you don’t need it, don’t install it. You can also avoid the Code Red worm by keeping your server up-to-date with security patches, which would be appropriate if you depend on index server. You can also help prevent worm type attacks by configuring IIS to only respond through host headers since most worms use the IP address of the IIS server, and not the host name.
Designing for Minimum Services on Windows Server 2003
When you’re using IIS 6, your website is hosted on a Windows Server 2003 server. You will need to determine what services you will allow to be installed on the server to minimize security risks on your network. When you first install Windows Server 2003, there are services installed that you will not want on your IIS server in many situations. The services installed by default that you might consider disabling are listed in Table 7.1.
| Service Name | Description |
|---|---|
| Application Layer Gateway Service | This service allows third-party vendors to write plug-ins for Internet Connection Sharing (ICS)\Internet Connection Firewall (ICF) that support their protocols. Disabling this service will prevent the server from running ICS or ICF. Generally, these services are provided more securely through a dedicated firewall. |
| Application Management | This service is used in conjunction with Software Policies on a GPO to assign, publish, enumerate, and remove programs. Most environments do not use this on their servers and therefore it is not needed. |
| COM+ System Application | This service is responsible for tracking and configuring COM+ applications that are installed on the server. Many servers do not host COM+ applications, so this service can be disabled. |
| Distributed File System | This service creates a logical namespace that will integrate your file-sharing resources. It is not needed on IIS servers in general unless you use it to replicate your site content. |
| Distributed Link Tracking Client | This service acts as the client to Distributed Link Tracking service and will disseminate information about shortcuts and respond to change events from the server. |
| Distributed Link Track Server | This service will track files on an NTFS partition across a network or on a local computer and will automatically update shortcuts when the file is renamed or moved. |
| Distributed Transaction Coordinator | This service coordinates operations that occur between multiple computers on the network to make sure they were all successful or all unsuccessful. It is used against databases, message queues, and file systems. You will need to verify that the applications on the server are executing distributed transactions. Most servers are not. |
| Error Reporting Service | This service collects and reports errors in running applications to Microsoft, which is then used to improve the product. It is not needed on a production server. |
| File Replication | This service allows files to be automatically copied to other servers on the network. This is very useful on domain controllers, but may have limited use on an IIS server unless you are using DFS for replication. |
| Help and Support | This service allows the Help and Support application to run on the server. You generally will not need to use it on the server. |
| Logical Disk Manager | This service integrates with the Plug and Play events for new drives being added and sends the information about the new drive to the Logical Disk Manager Administrative Service. You generally don’t dynamically add drives to your server, so it can be disabled. |
| Print Spooler | This service manages and prints to local and network print queues. You will not need to print from a server, so it can be disabled. |
| Remote Access Auto Connection Manager | This service will attempt to discover an unsuccessful authentication attempt to the remote access service and will automatically provide another means to connect if available. For example, if a program tries, but fails to connect to a remote network, this service will offer to try a dial-up connection if it is configured. |
| Remote Access Connection Manager | This service manages dial-up and VPN connections from the server to the remote network. |
| Remote Desktop Help Session Manager | This service launches and manages the Remote Assistance feature of the Help and Support application. This is needed only on client computers. |
| Remote Procedure Call (RPC) Locator | This service enables RPC clients to automatically locate RPC services using the RPC name service database. This is not required for RPC connectivity. |
| Removable Storage | This service identifies and catalogs removable media. It is used by Windows Backup, so don’t disable it if you are using Windows Backup. |
| Secondary Logon | This service allows a user to launch a process with different security credentials than the user’s current security context. This is usually used to launch administrative tools from a restricted account. This is generally not beneficial on a server because you are usually required to be an administrator or operator to log on to the server locally and there is potential for abuse. |
| Shell Hardware Detection | This service will perform the autoplay function on CD and DVD media. |
| Smart Card | This service reads smart cards. It is not needed if you do not have a smart card reader attached to your computer. |
| Special Administration Console Helper | This service allows you to remotely manage a server through an out-of-band method like a serial port. This is needed only if you have headless operation configured. |
| Task Scheduler | This service enables you to schedule executables to run based on time or CPU usage. It must be started if you are using Windows Backup to schedule backups of your server. |
| Telephony | This service provides a means to control telephony and voice over IP connections. It is generally not needed on an IIS server. |
| Upload Manager | This service is used to upload drive data to Microsoft, where it is used to help users find the proper device drivers for their computers. This is a synchronous or asynchronous file transfer service. |
| WinHTTP Web Proxy Auto-Discovery Service | This service uses the Web Proxy Auto-Discovery (WPAD) protocol to find and configure the web browser’s proxy configuration. |
| Wireless Configuration | This service automatically configures IEEE 802.11 wireless adapters to connect to a wireless network. |
You may decide that you need to use some of these services to satisfy business requirements. The services in Table 7.1 are just suggestions for a minimum set of services on most installed IIS servers.
In addition, the NTLM Security Support Provider is not installed by default, and you may need to install and enable it if you want to allow clients to authenticate with the NTLM protocol. Otherwise, the server supports only Kerberos v5 authentication. You will also need to make sure the HTTP SSL, IIS Admin, and World Wide Web Publishing services are enabled to host a web server. If you need to add additional services to the server, you can do this manually through the Add Or Remove Programs Control Panel applet or you can use the Configure Your Server Wizard or the Manage Your Server administration tool.
Remember that any service, application, or executable is a potential point of attack. You need to make sure that you take precautions to remove unused services, applications, or executables. If you cannot remove them, then you will need to figure out a way to disable them. This will greatly limit the attack footprint of your server.
Many security policies will not allow IIS to be installed with other services because of the security risks that IIS poses to the other services due to the many documented vulnerabilities. For example, the security policy might state that IIS is not to be installed on a domain controller because this will pose security risks to the domain accounts that are contained on the domain controller instead of just to the local accounts database on the IIS server itself.
Designing for Minimum Service on IIS
After an analysis of the services allowed on the Windows Server 2003 machine, you will need to determine what IIS services to install. By default, IIS is not installed on a Windows Server 2003 computer, so you will need to install it. During the installation you will have the option of installing many different services. Consult your baseline to determine the minimum services that you should install. You can install or uninstall services for IIS through the Windows Components Wizard’s Internet Information Services dialog box, as shown in Figure 7.1.
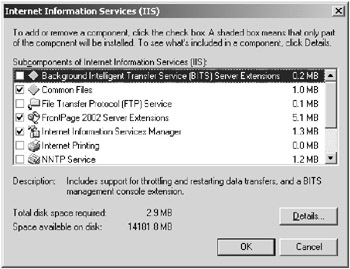
Figure 7.1: Selecting the IIS services to install through Windows Component Wizard’s Internet Information Services (IIS) dialog box
You can also use the Application Server dialog box through the Control Panel’s Add and Remove Program and the Add\Remove Windows Components to install or uninstall the components of IIS that you require.
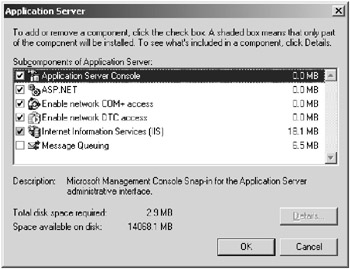
Table 7.2 describes the services that you can choose from.
| Service | Description |
|---|---|
| ASP.NET | Enables ASP.NET applications to be run on the server. |
| Enable Distributed Transaction Coordinator (DTC) | Enables network access to the DTC. |
| Message Queuing | Installs guaranteed message delivery for applications. |
| Background Intelligent Transfer Service (BITS) | Enables support for throttling and restarting file transfers using the BITS. Software Update Service (SUS) and Automatic Update do not require this component to run; they use only the BITS client and do not require the service. |
| File Transfer Protocol (FTP) | Supports transferring files through the standard FTP protocol. |
| FrontPage 2002 Server Extensions | Installs support for the authoring of web pages through Microsoft FrontPage, Visual InterDev, or Visual Studio .NET. |
| Internet Printing | Allows printers to be managed and shared over the Internet. |
| Network News Transfer Protocol (NNTP) | Enables support for the Usenet news articles, including distribution and posting. |
| Simple Mail Transfer Protocol (SMTP) | Enables support for sending e-mail over the Internet. |
| World Wide Web Publishing Service (HTTP) | Enables support for the World Wide Web. |
| Note | You will need to set the Enable Network COM+ Access setting to enable network access for COM+ applications; otherwise, they are limited to local access. This setting is required for FTP, HTTP, and BITS. You will also need it set for any custom COM+ application that you may be running on your server. You can set this setting in the Application Server dialog box. |
These services should be disabled unless you need them. For example, if you enable the World Wide Web Service, you will need to enable network COM+ access.
The following components on the Internet Information Services (IIS) dialog box are generally recommended as a baseline to be installed for a server acting as a web server:
-
World Wide Web Service
-
Common Files
-
Internet Information Services Manager
On the Application Server dialog box, the following components are recommended:
-
Enable Network COM+ Access
-
Internet Information Services
You will also want to consider configuring the rights on the server to prevent access to the Deny Access To This Computer From A Network setting and adding the following accounts to this group:
-
Anonymous Logon
-
Built-In Administrator
-
Guest
-
All Non-Operating System Service Accounts
The Deny Access To This Computer From A setting will deny access to the server from a network for most of the network protocols like Hypertext Transfer Protocol (HTTP), Server Message Block (SMB), NetBIOS, COM+, and FTP, to name a few. This will guard against someone using another logon to gain access to your server.
You can then decide to include additional components as required by your business. You will also be able to decide if Web Service Extensions are installed on the server through the World Wide Web Service dialog box in the Windows Component Wizard. You need to install the proper components if they are used by a website on your server. If you decide to install them, you will need to determine the Web Service Extensions each website will support on a per-site basis.
Designing for Web Service Extensions
Finally, you will need to determine the types of applications that your website will host. By default, a website only serves static HTML pages and images like GIF and JPEG files. If you would like to host Active Server Pages (ASPs), Active Server Pages .NET (ASP.NET), common gateway interface (CGI), or Web-based Distributed Authoring and Versioning (WebDAV) applications, you will need to enable these features for your website. Figure 7.2 shows where you can enable and disable the Web Service Extensions.
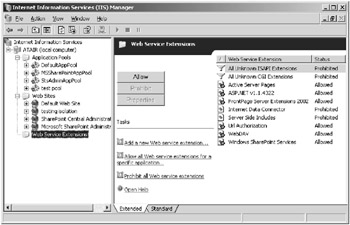
Figure 7.2: Prohibiting or Allowing Web Service Extensions.
You can use this dialog box to allow or prohibit the application extensions that your website requires or to add custom ISAPI or CGI extensions that you require. The ISAPI or CGI applications that you add to the Web Service Extensions define the DLLs or EXEs that are required for the ISAPI applications and whether it is allowed or prohibited.
You will need to analyze the applications that you are running on the web server for the application extensions that are required. If there is poor documentation, you can look for file extensions on the server to determine if the application uses extensions like .asp or .aspx. You could also look at the WWW protocol log to determine what HTTP verbs or URLs are being used on your web server. This may aid in determining if the web application uses WebDAV or FrontPage Server Extensions. Table 7.3 illustrates signatures for various applications.
| Web Service Extension | Extension or Verb Signature |
|---|---|
| ASP.NET | .aspx |
| ASP | .asp |
| Server Side Includes | .ssi, .inc |
| Internet Data Connector | .ida, .idc |
| WebDAV | SEARCH, BPROPS, PUT for example; basically anything other than GET and POST (see RFC 2068 for a complete list) |
| FrontPage Server Extensions | Anything that refers to a directory, which contains .vti |
| CGI or Custom ISAPI Application | Anything the developer wants to create |
Table 7.3 is generally the case for what files are processed by ISAPI extensions, but there may be a custom ISAPI application or CGI application installed, which could process requests for anything that the developer wants. You will need to consider this and add a Web Service Extension to process the custom ISAPI or CGI application.
In the Design Scenario “Designing for Minimum Services with IIS,” you will design for minimum services on a Windows Server 2003 server running IIS 6.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 168
- Structures, Processes and Relational Mechanisms for IT Governance
- An Emerging Strategy for E-Business IT Governance
- A View on Knowledge Management: Utilizing a Balanced Scorecard Methodology for Analyzing Knowledge Metrics
- Governing Information Technology Through COBIT
- The Evolution of IT Governance at NB Power