Isolating Insecure Networks
|
| < Day Day Up > |
|
Most organizations have a network perimeter, which is any point that connects the internal network to external networks. Network perimeters include the network connection point to the Internet, links to a satellite office, or a remote access server. A screened subnet is also on the perimeter of a network. A screened subnet is a protected area on the network that is used to run services that are shared outside of the organization. Business-to-business (B2B) services are typically run from this type of subnet. A DMZ is a type of screened subnet, DMZ stands for demilitarized zone, which is an isolated network segment at the point where a corporate network meets the Internet. Other examples of network perimeters are wireless access point or virtual private network (VPN) connections.
The network perimeter is the part of any network that is most vulnerable to attack. The attack can be random or targeted. Because of the prevalence of threats that affect public network access points, you should take great care to minimize your internal network’s exposure to the public network, also referred to as the “wild.”
Some companies choose to use firewall services or a screened subnet. As previously mentioned, a demilitarized zone is a specialized type of screened subnet in which the external network is the Internet. Routers and firewalls can be used to screen the traffic that passes into and out of the screened subnet. There are typically three types of configurations that an organization will take when securing its network perimeters:
Bastion host A bastion host acts as the only connection for computers on the internal network to use to access the Internet (or other external networks). This configuration is illustrated in Figure 2.8. When configured as a firewall, the bastion host is specially designed to prevent attacks against the internal network. The bastion host uses at least two network adapters; one is connected to the internal network while the other is connected to the external network. This configuration physically separates the internal network from the outside. Its weakness is that it is a single point of failure; should it be compromised, the attacker can gain access to the internal network.
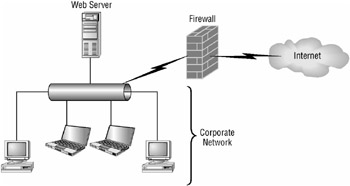
Figure 2.8: A bastion host
Three-pronged configuration In a three-pronged configuration, the firewall system will have a minimum of three network adapters. One adapter will be connected to the internal network, one to the external or public network, and the third to a screened subnet. This configuration allows for hosts from the public and internal networks to access the available resources in the screened subnet while continuing to isolate the internal network from the wild. Figure 2.9 depicts this configuration.
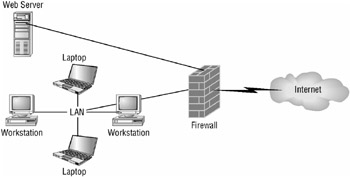
Figure 2.9: A three-pronged configuration
Back-to-back configuration The back-to-back configuration places the screened subnet between two firewalls. The screened subnet is connected through a firewall to the Internet on one end and connected through another firewall to the internal network on the opposite end. This is probably the most secure configuration while still allowing for public resources to be accessed. This would require an attacker to breach both firewalls in order to compromise the internal network. Figure 2.10 shows an illustration of this configuration.
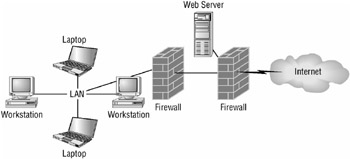
Figure 2.10: A back-to-back configuration
Real World Scenario: The Importance of Perimeter Security
Quovadimus Incorporated is a technology firm specializing in biotechnology. The organization works with educational and government institutions frequently. The CIO tells the network administrator to provide the partnering organizations with access to the company’s data. Quovadimus also hosts its own web and mail servers that are accessible from the Internet. The CIO has promised the partnering organizations that the data will be available to them within an hour of their conversation. As a result of not properly preparing for this type of data access, there is no time to develop a secure perimeter.
Using basic techniques like port scanning, an attacker is able to footprint the Quovadimus perimeter network. The attacker learns what operating systems and services are running on the perimeter network. The attacker now has enough information to create an entire diagram of the organization’s perimeter. The attacker researches the known vulnerabilities of the services that are running in the perimeter network and can now systematically attack the network. The attacker can now gain access to some or all of the services that are accessible, including those of the organization’s partners.
You will need to make sure that the network perimeter is properly secured, especially if there is a possibility of its resources being consumed outside of your organization.
Design Scenario: Segmenting Networks for Security
ABC Incorporated manufactures explosive space modulators to be sold by its partners. ABC has an Internet website that it hosts on Server1. In addition, ABC’s partners need to be able to access the inventory data that is exposed from a web service that is running on Server2. All access to the web service needs to be screened, and the web service and website need to be on separate networks. All of the employees of ABC Incorporated use the corporate network to access their data and to access the other resources. ABC has room in the budget to purchase only one more server to maintain security.
-
Question: Which technique should you use in this scenario to meet the requirements and prevent external networks from accessing the internal network? Answer: The three-pronged configuration is the only option that meets all of the requirements in the gi ven scenario. There are three separate networks that need to be in place: the network with the website, the network with the web service, and the corporate network. Therefore, the bastion host configuration with only one more computer cannot secure all three networks. Back-to-back configuration requires at least two more computers, configured as firewalls, to be purchased to segregate the DMZ, the LAN, and the Internet. A single server, with three network adapters, will meet the requirements without compromising security.
One of the best techniques in securing the computers that physically leave your network perimeter, such as laptop computers that travel with the user or users who access an organization’s resources from their homes (for example, using a dial-up or VPN connection) is to simply educate the users. Make sure the users are using updated antivirus software as well as personal firewall software.
In the “Segmenting Networks for Security” Design Scenario, you will be evaluating a scenario and choosing the best technique to isolate, or segment, the internal network from external networks.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 168
- An Emerging Strategy for E-Business IT Governance
- Linking the IT Balanced Scorecard to the Business Objectives at a Major Canadian Financial Group
- A View on Knowledge Management: Utilizing a Balanced Scorecard Methodology for Analyzing Knowledge Metrics
- Measuring ROI in E-Commerce Applications: Analysis to Action
- Technical Issues Related to IT Governance Tactics: Product Metrics, Measurements and Process Control