Finger Biometrics
| < Day Day Up > |
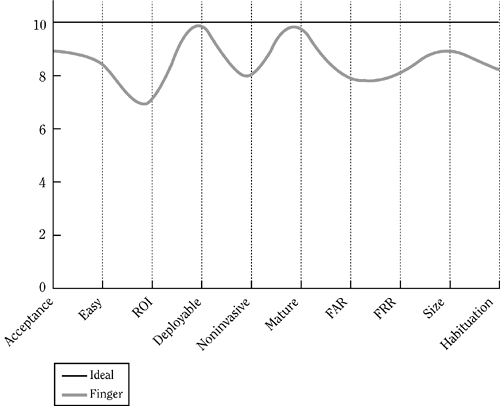
| The finger biometric scored very well relative to the ideal biometric, as shown in Figure 9-1. Its greatest strengths are its deployability and maturity. The greatest weakness comes from the cost and hence ROI. What follows is a breakdown of each characteristic for the finger biometric. Figure 9-1. Scores for finger biometrics. Acceptance: 9Finger biometrics are some of the oldest and most studied methods of biometric identification. People accept them because of their long history. It also helps that finger biometrics are active, which means that the user needs to submit to the biometric system for sampling. It does not qualify for ideal status because some people feel that using their fingerprint is very similar to being fingerprinted for a criminal offense. Easy: 8.5The ease of use of finger biometrics has increased greatly. The new sensors available and the use of better ergonomics have led to this increase in ease of use. Some devices may not be optimal for use with all fingers, and others may not work well with all finger types. ROI: 7The decreasing cost of devices and the ease of deployment and training make this a very cost-effective technology. With biometrics being used for password replacement or as a strong factor of authentication for SSO, the savings alone on password resets present a very attractive ROI. Deployable: 9.9Deployability considers how easy it is to get a device on a desktop. Finger biometric devices for network security have become much smaller. USB connections have freed the devices from having to use legacy serial or parallel ports and the associated hassles that come from using those connection methods. Noninvasive : 8Since finger biometrics are associated with active devices, and they image only an exterior feature, they are much more noninvasive than many other biometric methods. A higher score was not given since many feel that fingerprints are very private due to the fact that they are used by law enforcement. This can mean that there is some stigma associated with using finger-based biometrics. Mature: 9.9As stated in the opening, fingerprint biometrics are some of the oldest and most studied biometrics. This continued study and time on the market have allowed the fingerprint biometric to mature to a point where the research in the field has turned to increasingly difficult features to implement. FAR: 8The FAR measurement is somewhat important depending on the reason for deployment. A deployment done for convenience would want the FAR to be set where the majority of the users can authenticate at a meaningful level. If security is the primary concern, then an increase in FAR will lead to a decrease in user convenience. FRR: 8The FRR measurement is somewhat important depending on the reason for deployment. A deployment done for convenience would want the FRR to be set as low as possible to still have some confidence in the verification and/or identification taking place. Size: 9Due to the limited desk space that most users have, it is not surprising to have to fight for desktop real estate. Again, through good design and maturity, this device has significantly reduced its physical footprint on the desktop. Habituation: 8.5A user can become habituated to a fingerprint biometric rather quickly. This stems from the fact that on a daily basis, we use our hands for everything, and so we have built up a fair amount of dexterity and coordination with them. The placing of a finger on a scanner is relatively straightforward, but it still requires a bit of coordination. |
| < Day Day Up > |
EAN: 2147483647
Pages: 123
- The Four Keys to Lean Six Sigma
- Key #3: Work Together for Maximum Gain
- Making Improvements That Last: An Illustrated Guide to DMAIC and the Lean Six Sigma Toolkit
- The Experience of Making Improvements: What Its Like to Work on Lean Six Sigma Projects
- Six Things Managers Must Do: How to Support Lean Six Sigma