| Now that you have seen the user experience with the Active Directory plug-in, let's go behind the scenes to understand how the plug-in makes integration so easy. Before users can log in, the plug-in must be configured. When an administrator clicks the Bind button and authenticates, the plug-in begins a sequence of events to appropriately configure Mac OS X. 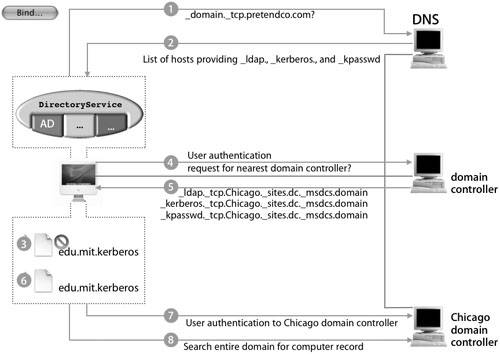
The plug in uses _domain.tcp.domain.com to find the DNS server, which should return a list of hosts providing LDAP and Kerberos services.
It then uses LDAP to find out what domain it's currently in. The plug-in will attempt to authenticate to that domain to look for the closest domain controller.
Assuming a successful authentication, the domain controller will use another extension of DNS, which supports site records, and respond by supplying the host information for the nearest domain controller to the Mac OS X computer.
With a list of domain controllers now returned, the plug-in chooses one and builds an edu.mit.Kerberos configuration file based on it.
The plug-in will attempt to authenticate to the new domain controller and begin searching the domain and forest for a computer record with a computer ID that corresponds to the one specified for the plug-in.
If a match is found, the plug-in will use that computer record.
If a match is not found, the plug-in will create a new computer record with the plugin's specified computer ID.
A password is then attached to the newly created computer ID or changed if the computer account already exists.
Tip The plug-in can create this record only if the user name and password provided belong to an account with the authority to add computer records to the domain.
At this point, Mac OS X is fully configured to integrate with Active Directory. Encountering Errors To cleanly unbind Mac OS X from an Active Directory domain, first connect the computer to the domain to ensure that the plug-in can remove the associated record. When you clicked the Bind button, it automatically changed to an Unbind button, so all you have to do now is click Unbind. Administrators can forcefully remove the binding configuration information by deleting the ActiveDirectory.plist file. If you choose to do this, you will need to remove the computer record from the Active Directory domain manually, then remove the listing from the authentication path. Note The ActiveDirectory.plist file is located at /Library/Preferences/ DirectoryService/.
However, several errors can occur when attempting to bind to Active Directory. Below are explanations of the more common errors: Invalid domain: This message refers to the plug-in's inability to find a domain controller or Global Catalog server with the existing Mac OS X network configuration. This is due to incorrect names being typed during plug-in configuration or because the Mac OS X computer is using a DNS server lacking the appropriate service records that would normally be populated through Dynamic DNS. For best results, Mac OS X computers should be using a Microsoft Dynamic DNS server or another DNS server that has been configured to allow Dynamic DNS updates from Active Directory servers. 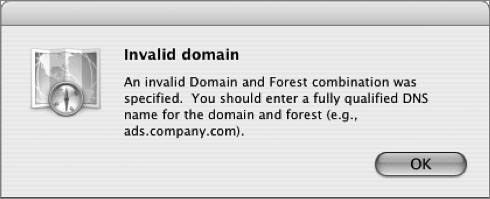 Active Directory time error: This error occurs because the plug-in depends on a functional Kerberos environment. Kerberos requires that all Kerberos host and client clocks be relatively in sync. In any Kerberos deployment, the use of a network time server is essential to reliable operation. In general, a 5-minute time difference is all that is permitted. 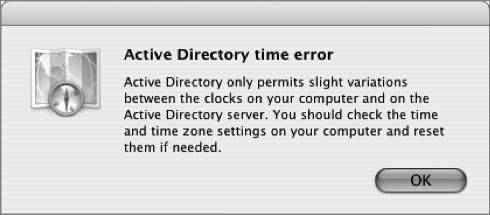 Insufficient privileges: This error will occur when the user name and password supplied do not have permission to join a computer to the listed domain. 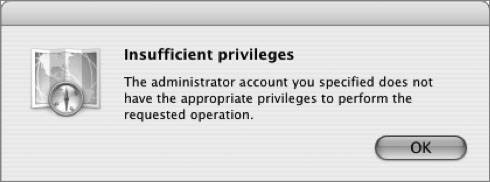
Troubleshooting To troubleshoot Active Directory DNS issues, you can run nslookup in interactive mode: nslookup -sil
The prompt turns to >. To look at various service records associated with binding, type any of the following, depending on your query: host -t SRV _ldap._tcp.domain.com host -t SRV _kerberos._tcp.domain.com host -t SRV _kpasswd._tcp.domain.com Note For the word domain, substitute your Active Directory domain.
Each one of these will return information based on your lookup. If you do not see any results for the entries, then the entries are not valid domains. You can also use nslookup to test reverse DNS lookups. To look up standard records, type set type=A and enter the server address, such as mainserver.pretendco.com
The results should look like the following: mainserver.pretendco.com = 10.1.0.1
Typing 10.1.0.1 should yield a result similar to this: 10.1.0.1.in-addr.arpa PTR mainserver.pretendco.com
Also, when binding with the Active Directory plug-in, you can send DirectoryService a -USR1 message to request that it log to /Library/Logs/DirectoryService/DirectoryService.debug.log. sudo killall -USR1 DirectoryService
This is a toggle switch command; running it again will turn off the debug log. Plug-in Configuration Files The Active Directory plug-in uses a collection of files to make Active Directory integration a reality: edu.mit.Kerberos: This is the primary Kerberos configuration file. It is chiefly responsible for identifying the Kerberos server used to facilitate password policies and single sign-on within the domain. This file is located in /Library/Preferences/. ActiveDirectory.plist: Contains all values for the plug-in's advanced options. Also contains the schema mappings being employed by default. Advanced users can make manual modifications to this file to further configure the plug-in. This file is located in /Library/Preferences/DirectoryService/. SearchNodeConfig.plist: Used by Directory Access to record which directories to search and in what order to search them. Administrators troubleshooting directory configurations may want to delete this file, thus resetting Mac OS X to a state in which no remote directories are searched. This file is located in /Library/ Preferences/DirectoryService/. ContactsNodeConfig.plist: Used by Directory Access to track which directories to use for contact lookups. Applications like Mail and Address Book use these directories to automatically locate contact information. This file is located in /Library/ Preferences/DirectoryService/. 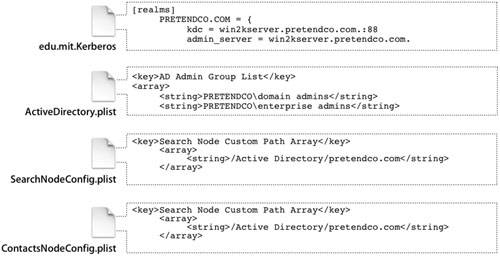
| 



