Implementing Bluetooth Security in Mac OS X
| Because Bluetooth is used by consumer devices such as cell phones, headphones, keyboards, mice, and laptop computers, an important goal is that Bluetooth users should be able to effortlessly and quickly pair devices to work together and share information. However, ease-of-use is a tradeoff with security. If pairing devices and sharing information is made too easy, attackers will take advantage. Security options are necessary to make Bluetooth acceptably safe for most environments. In its "Mac OS X v10.3.x Panther Security Configuration Guideline," the National Security Agency (NSA) of the U.S. federal government recommends completely disabling Bluetooth. (As of this writing, a newer version of the document isn't available, but the next version will likely make the same recommendation.) The NSA document has detailed recommendations on how to completely disable Bluetooth for all Macintosh users. IT professionals and users in environments with stringent security requirements should read the NSA document and implement the recommendations in it, where appropriate. Bluetooth should be disabled by default and enabled as necessary. Less rigorous and restrictive approaches can be taken in environments in which users regularly connect wireless keyboards, mice, and other devices, or share files between Bluetooth-enabled laptops, cell phones, and PDAs. Some aspects of Bluetooth (such as using it for Internet connectivity) can be disabled, while others can be allowed, depending on your specific security requirements and policies. You can completely disable Bluetooth by removing the Bluetooth kernel extensions (IOBluetoothFamily.kext and IOBluetoothHIDDriver. kext) located in /System/Library/Extensions/. Keep in mind that these drivers can be replaced with a software update, so you still need to perform regular preventative measures. That means, for example, creating a launchd item to watch the Extensions directory for the Bluetooth kernel extensions and remove them as necessary. And before installing Bluetooth on your production computers, it's a good idea to test software updates on another computer. Securing Bluetooth Internet AccessBluetooth users have the ability to pair their Macintosh computers with a Bluetooth-enabled cell phone that has Internet access, and access the Internet using that link. This should be discouraged. Although the speed of the link is so slow that most attacks would not succeed, slow speed is not a good excuse for lax security measures. Attackers are persistent. Note There are actually two links in this example that are vulnerable to sniffing and other attacks: the Bluetooth link and the cellular Internet link. A network administrator or IT professional who distributes laptops to mobile users can configure the laptops so that users who don't have the administrator password can't use Bluetooth for network connectivity and Internet access.
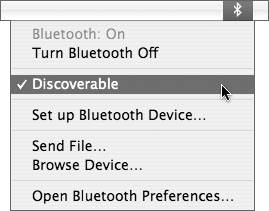
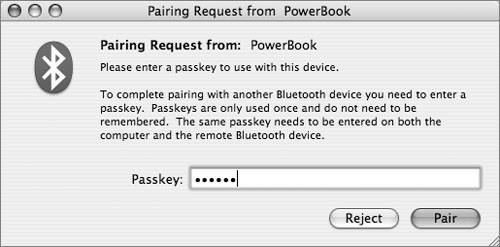
Controlling Bluetooth DiscoverabilityBluetooth discoverability allows devices on a Bluetooth network to easily find each other. Configuring a device to be nondiscoverable makes it harder to find. To prevent attackers from discovering a Bluetooth device, especially a Bluetooth-enabled Macintosh, configure the device to be nondiscoverable. In Mac OS X, you can do this in the Bluetooth System Preferences by deselecting Discoverable in the Bluetooth Status menu. Another Bluetooth device can still connect to your computer even if you make your computer nondiscoverable. One way to accomplish this is for you to initiate the connection. Another possible security weakness is that your computer was once configured as discoverable and another device still "remembers" how to access your computer with Bluetooth. In other words, making your computer nondiscoverable doesn't make it completely inaccessible via Bluetooth; other devices just have a harder time finding it, which enhances security. Using Bluetooth File Transfer Security OptionsBluetooth file transfer allows other devices to browse files on your computer, but your computer must be discoverable for this to work. Beginning with Mac OS X 10.4.1, Bluetooth file transfer is not turned on by default, which is good from a security point of view. In some situations, however, allowing other users to browse your files could come in handy. For example, some cell phones can share files with a Macintosh, which can be useful for getting contact information onto a cell phone. In situations like this, you can temporarily make your computer discoverable. Then temporarily enable file transfer and specify a folder that other devices can browse and drop files into. Other users can also retrieve files from this folder. Make sure you require pairing for file transfer. You can enable file transfer options by opening the Bluetooth System Preferences and clicking Sharing. Note Use caution when attempting to pair Bluetooth devices in a public place, since attackers can harvest the passkey for later use. 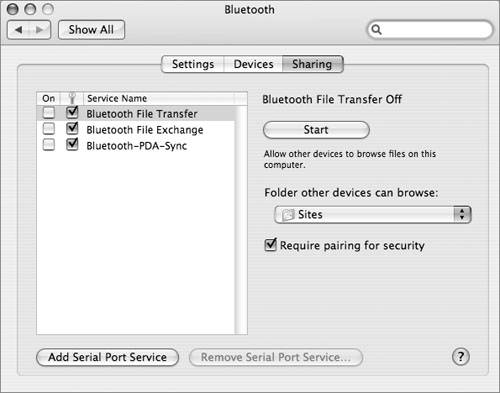 When you require pairing for security with Bluetooth file transfer, if another user wants to browse your files, you will be warned and given the opportunity to enter a passkey. Because Bluetooth has limited range, you should be able to physically look around and see who wants to browse your files. If it's a coworker, friend, or other legitimate user, enter a passkey and tell the person what it is. That person will also enter the passkey on his device. If you don't see anyone other than some shadowy figure in the dark looking at you with a sneaky, anticipatory smirk, then simply reject the invitation to pair. A Pairing Request dialog box appears when another user tries to browse the files in your public folder. Using Bluetooth File Exchange Security OptionsMac OS X Bluetooth preferences also include options for securing the Bluetooth File Exchange utility. Bluetooth File Exchange is on by default. You should turn it off until you need it. To maximize the security of file exchange, configure Mac OS X to prompt for each file that it receives, and to ask before accepting Personal Information Management (PIM) or other types of files. Also, be sure to select "Require pairing for security." 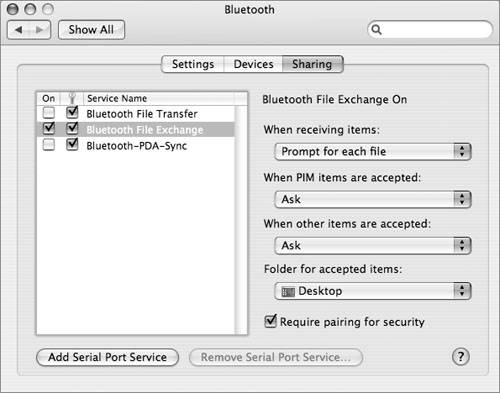 Using Bluetooth PDA Sync Security OptionsUnder the Bluetooth Sharing preferences, best security practices dictate not turning on the serial port, not showing the serial port in Network preferences, and requiring pairing for security. 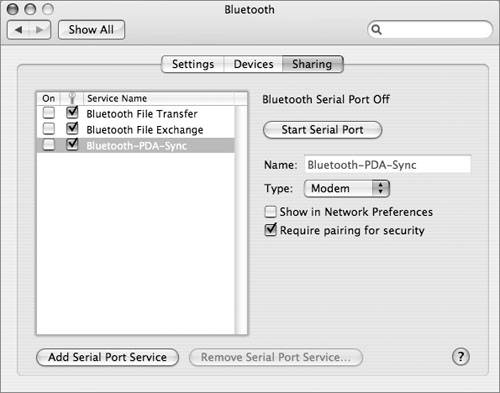 |
EAN: 2147483647
Pages: 258