Implementing WLAN Security in Mac OS X
| Security on 802.11 wireless networks is even more important than on Bluetooth networks. Whereas Bluetooth is a nice feature that some users appreciate for connecting wireless devices and sharing information, 802.11 technology has become a mainstream method for connecting computers in businesses, homes, colleges, hotels, coffee shops, stores, airports, and so on. Extensive enterprise networks based on 802.11 are much more prevalent than the smaller, personal networks that connect Bluetooth devices, and they must be protected with the security measures discussed in this lesson. Note Using a Virtual Private Network (VPN) connection, especially over a wireless network, is an excellent way to combine a tunneled connection to your network with relatively strong encryption. Before discussing detailed recommendations, it's worth exploring a few general guidelines for WLAN security:
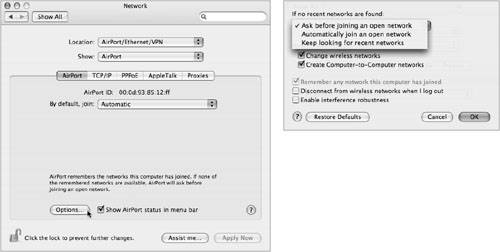
To ensure mobile users don't stumble into insecure wireless networks, configure Mac OS X systems to ask the user before the computer automatically joins a network. For corporate environments with stringent security requirements, you can also require an administrator password when a user wishes to move to a new network or to create a computer-to-computer network. To enable these options, do the following:
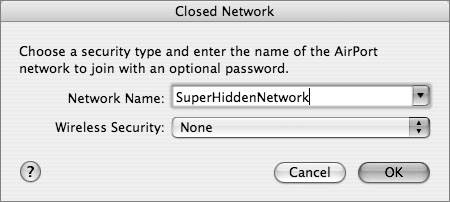
For those peripatetic users who roam to hotels, airports, coffee shops, and so on, requiring firewall and antivirus software is essential, but requiring authentication and encryption to use the wireless networks where they end up is usually not appropriate. Can you imagine a mobile user stumbling into the local coffee shop at 7 A.M., laptop under her arm, craving some caffeine, and having to ask the barista for the 128-bit encryption key to access the coffee shop's wireless network? That's not how most coffee shop networks work. When the user accesses her "enterprise" wireless network, however, whether that network is at home or at a business or school, requiring the authentication and encryption methods discussed in the next sections are absolutely appropriate. Implementing Wired Equivalent PrivacyWired Equivalent Privacy (WEP) was the first authentication and encryption standard built into the original 802.11 specification, which IEEE standardized in June 1997. You shouldn't use WEP unless your network must carry traffic for older devices that don't support newer security mechanisms. WEP isn't secure. Without much effort, attackers can derive the WEP encryption key and compromise a network that is supported only by WEP. If possible, upgrade any older devices that only support WEP right away. If upgrading isn't possible, try to use WEP in conjunction with 802.1X user authentication. This lesson discusses WEP in case you need to use it to support older devices that can't be upgraded and because it provides good background information to help understand newer security mechanisms. But keep in mind that WEP is not secure and should be avoided if possible. In wired networks, a device must physically plug into the network to have access. This provides some security. An attacker has to have physical access to a port on a hub or switch, or a live jack in a wall, to gain access. This isn't possible on a wireless network. There's nothing to plug in and there aren't any ports or jacks. IEEE recognized this issue in the early development of 802.11 and built authentication capability into the standard. IEEE specified both open authentication (which is essentially no authentication) and shared key authentication using WEP. WEP requires that a device send a key to log on to the network. From that point, the key is also used to encrypt data sent on the network. This shared key must be configured on the wireless access point and on any devices that join the network. WEP supports two lengths for the shared key: 64 bits and 128 bits. Both of these key lengths include a 24-bit initialization vector. The 64-bit key is often called a 40-bit key, which represents the key length minus the 24-bit initialization vector. The 128-bit key is rarely referred to as a 104-bit key, even though that is technically accurate and would match the terminology used for 64-bit keys. As part of the encryption process, WEP concatenates the shared key with the randomly-generated 24-bit initialization vector. WEP includes the initialization vector in the clear (unencrypted) in the first few bytes of a packet. The receiving station uses the initialization vector along with the shared key to decrypt the payload portion of a packet. The 24-bit initialization vector is one of the sources of WEP's infamous vulnerabilities. WEP eventually uses the same initialization vector for different data packets. If an attacker collects enough packets based on the same initialization vector, the attacker can eventually discover the shared key. For high-usage WLANs, an attacker can capture traffic for a few hours and discover the key. This allows the attacker full access to the network and to any confidential data being transmitted on the network. Note that the IEEE knew they weren't providing strong privacy with WEP, but the same amount of privacy found on wired networks. As Sun Microsystems Inc. chairman and CEO Scott McNealy said, "You have no privacy. Get over it." Wired networks don't have much privacy, and neither do WLANs that use WEP. Configuring WEPBecause WEP is reasonably easy to crack, don't use it unless it's the only option. Apple supports other options, but you may need to configure WEP for compatibility with non-Apple devices or Macintosh computers running older system software. To configure WEP, you need to know the shared key that is configured on the access point. You should enter the key in the exact format that the administrator for the access point specifies. A WEP key can be a plain-language password, an exact number of ASCII characters, or an exact number of hexadecimal digits. Access points that permit a plain-language password don't require the network administrator to create a key of an exact length. Instead, the access point handles the "heavy lifting" for the user and hashes the password to a key of the right length. Unfortunately, the hashing used on one vendor's access point may not match the hashing used by other vendors' wireless network interface cards (NICs), resulting in a multiplatform compatibility problem. In this case, you may need to enter a precise number of characters or digits for the key. For a 40-bit WEP key, you may have to enter precisely 5 ASCII characters or precisely 10 hex characters. Each ASCII character is 1 byte or 8 bits. Five of them add up to the 40 bits in the 40-bit key, which some access points may call a 64-bit key (because they include the length of the 24-bit initialization vector). For a hex-based key, you need to enter exactly 10 hex digits because each hex digit is 4 bits. Valid hex digits are 0 through 9 and A through F. For a 128-bit WEP key, you may need to enter precisely 13 ASCII characters or precisely 26 hex digits. Thirteen multiplied by 8 adds up to the 104 bits in the 128-bit key, not counting the 24-bit initialization vector. Twenty-six multiplied by 4 also adds up to 104. Again, this is only if you need to use WEP for compatibility with older machines. When your Macintosh tries to join a network that uses WEP, you will be prompted to enter a WEP key. You can also enter a WEP key by using the menu from the AirPort status icon in the menu bar. (If the AirPort status icon isn't visible in the menu bar, go to System Preferences and select the Network pane to make it visible.) Choose Other from the menu and enter the name of the network. After you enter the name of the network, use the Wireless Security pop-up menu to choose the right type of password. If the network you are joining is already up and running, you will see only the options that are allowed by the administrator of the access point for that network. Understanding 802.1X AuthenticationWEP uses a shared key for authentication and encryption that is configured on all clients and the access point. Management of this key can be difficult. How does the administrator securely let everyone know that the key has changed? If a laptop gets stolen, how does the administrator lock out the thief from the wireless network? What does the administrator do if an attacker captures enough packets to recover the supposedly secret WEP key? Wireless vendors realized during the early days of WEP deployment that a better method for authentication was necessary. Fortunately, the IEEE already had an authentication protocol that was gaining popularity in the wired world. That protocol is 802.1X, standardized in IEEE's "802.1X Port-Based Network Access Control" document. The IEEE adopted 802.1X as a standard in August 2001. IEEE 802.1X specifies a method for authenticating a user who attaches a device to a LAN port. It is used on both wired switches and on wireless access points (where the "attachment" is not purely physical). 802.1X can be used with an authentication server, such as a Remote Authentication Dial-In User Service (RADIUS) server, which is good practice for larger enterprises. The Apple Wi-Fi Protected Access (WPA) Enterprise security feature, for example, works with a RADIUS server and is described later in this lesson in the "Using WPA Enterprise" section. For older environments that still use WEP due to legacy NICs or access points, WEP security can be enhanced by requiring 802.1X. 802.1X supports many authentication algorithms. The most common are varieties of the Extensible Authentication Protocol (EAP), which is an Internet Engineering Task Force (IETF) standard, documented in Request For Comments (RFC) 2284. With 802.1X and EAP, devices take on one of three roles:
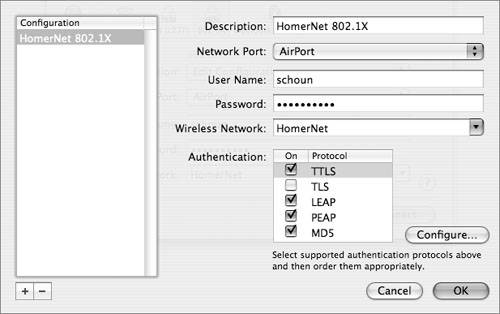
When 802.1X and EAP are implemented, a client device that associates with a wireless access point cannot use the wireless network until the user is authenticated. An EAP supplicant on the client obtains credentials from the user, which could be a user name and password, a user name and one-time password, or a digital certificate. The credentials are passed to the authenticator and then to the authentication server where a session key is developed. With 802.1X, the heavy lifting is done on the supplicant (the wireless client) and the authentication server, and the access point has very little work to do. Configuring 802.1X on most access points is as simple as enabling the option to use 802.1X and then pointing the access point at a RADIUS server that supports 802.1X. Some access points are even easier to set up because they support a built-in authentication server. This can make deployment much faster, especially if setting up a RADIUS server is a bit daunting for novice network administrators. When using 802.1X and EAP, session timeouts force a client to reauthenticate to maintain network connectivity. This causes a WEP key to be regenerated. This feature mitigates statistical key derivation attacks and is a critical WEP enhancement. Note Reauthentication can cause some delay, when compared to using a static WEP key. This may cause a problem for users who roam with delay-sensitive devices, such as 802.11 phones. Note that 802.1X and EAP authenticate users, whereas basic WEP authentication is device-based. A WEP shared key is entered into wireless devices and the access point. If a thief steals a laptop computer using a static WEP key, the thief can access the wireless network which would probably require the network administrator to change the WEP key on the affected access points and all clients. 802.1X and EAP, on the other hand, generate a unique key for each user. This relieves network administrators from the burden of managing static keys. EAP also supports mutual authentication, which allows a client to be certain that it is communicating with the intended authentication server and not an attacker posing as a server. EAP supports the use of digital certificates. A digital certificate is a special kind of data structure that contains information about who it belongs to, who it was issued by, a unique serial number or other unique identification, valid dates, and an encrypted "fingerprint" that can be used to verify the contents of the certificate. Digital certificates are issued by trusted third parties known as certificate authorities. A wireless user's digital certificate can include a user name and password, a one-time password provided by a smart card, or any other identity credentials that the IT administrator is comfortable using. Selecting EAP TypesWhen setting up wireless clients, access points, and authentication servers, you need to choose the right EAP standard to match your users' needs and security policies. Selecting the right EAP type can be challenging because there are so many options and because they go by funny names, such as LEAP and PEAP. You need to get this right though. The supplicant, authenticator, and authentication server must all be configured for the same variety of EAP, which is mostly likely one of the following:
The following table summarizes features of the various EAP types:
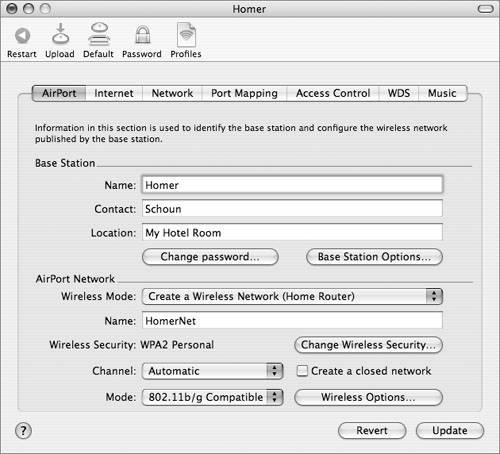
Combining 802.1X With WEPFor networks with legacy equipment that don't support newer wireless security standards such as WPA, 802.1X can be used to enhance the security of WEP. Although WEP encryption is still crackable in theory, 802.1X means every connection authenticated with 802.1X gets its own WEP key, which can be changed as often as the network administrator controlling the WLAN desires. A second benefit with 802.1X is that the administrator actually knows who is on the network. Bandwidth thieves and other attackers can't get on without getting authenticated and that requires going through a true authentication dialog where a user name and password must be entered. Understanding Wi-Fi Protected AccessThe IEEE started working on enhancements to WEP as soon as its problems became known, and in June 2004, the IEEE 802.11i Working Group ratified a new security standard called 802.11i. Because there was quite a long gap between the time that WEP vulnerabilities were proven (2001) and the release of 802.11i, vendors started implementing parts of 802.11i long before 2004, under the auspices of an industry consortium known as the Wi-Fi Alliance. In 2003, the Wi-Fi Alliance finalized WPA. WPA is a subset of 802.11i, leaving out the more complicated aspects of 802.11i which would require a hardware upgrade on some vendors' equipment, including a requirement to use the Advanced Encryption Standard (AES). WPA includes the following features:
In September 2004, the Wi-Fi Alliance introduced WPA2. With WPA2, the entire IEEE 802.11i specification is supported. Like WPA, WPA2 supports IEEE 802.1X/EAP authentication or preshared keys. It also includes support for AES, which is newer and stronger than WEP or TKIP. AES satisfies U.S. government security requirements. It has been adopted as an official government standard by the U.S. Department of Commerce and the National Institute of Standards and Technology (NIST). Apple added support for WPA2 in Mac OS X 10.4.2. Unlike some vendors, Apple equipment does not require a hardware upgrade because Apple base stations and cards already have an AES chip built in. 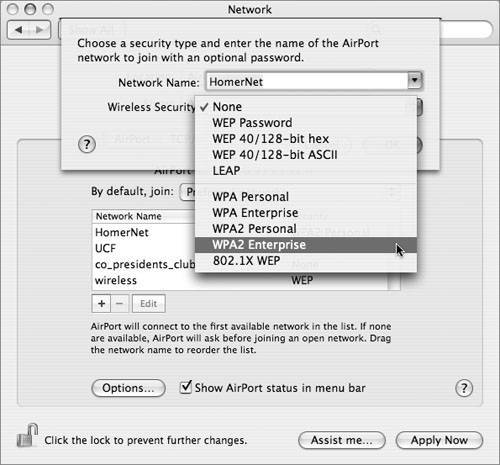 Apple offers two modes for both WPA versions:
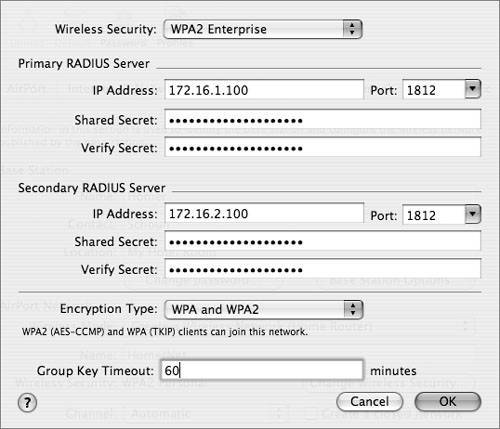
Using WPA EnterpriseWPA Enterprise is intended for large organizations, such as businesses and educational institutions, with rigorous security requirements and sizeable wireless installations. WPA Enterprise leverages the IEEE 802.1X authentication framework, which uses an EAP type with an authentication server to provide strong mutual authentication between a client and authentication server via an access point. (See "Understanding 802.1X Authentication," earlier in this lesson.) The authentication server is a RADIUS server, which could be running on Mac OS X Server or any other server that supports RADIUS. Each user is assigned a unique user name and password for access to the WLAN. This affords a high level of individual privacy. As with WPA Personal, WPA Enterprise uses TKIP encryption. TKIP issues a new encryption key for each data packet sent for each session of each user, making the encryption extremely difficult to break. What distinguishes Apple WPA Enterprise from WPA Personal is that WPA Enterprise requires a RADIUS server whereas WPA Personal does not. Large institutions with many mobile users often have numerous wireless access points. Users roam from one access point to another. With a good network design, which access point their computers have associated with is transparent to users. To make this secure, all access points must have knowledge of user authentication information. Here's where the benefits of a RADIUS server come into play. Network administrators could configure authentication information in each access point, but that is cumbersome. Instead, authentication information can be configured in one RADIUS server (which is optionally backed up by a secondary server). Livingston, Inc. developed the RADIUS protocol to authenticate dial-up users back in the early 1990s. It was formalized by the IETF and is currently standardized in RFC 2865. It has become a de facto standard for authenticating users of all types, not just dial-up modem users. RADIUS gives an administrator the option of having a centralized database of user information. The database can include user names and passwords, configuration information, and the type of services permitted by a user. RADIUS is a client/server protocol. In a wireless network, an access point acts as a client of a RADIUS server. RADIUS uses User Datagram Protocol (UDP) for its underlying transport. The registered UDP port number for RADIUS is 1812. More advanced versions of RADIUS can also use ports 2083 and 3799. Early implementations of RADIUS used port 1645. Because of these multiple port numbers, most access points let you configure which port number to use to reach the RADIUS primary and secondary servers. Several companies offer RADIUS server implementations for Mac OS X Server. Setting up a RADIUS server is not difficult; refer to the documentation that came with the RADIUS server. An access point must be configured with the Internet Protocol (IP) address of the RADIUS server (and optionally the address of a secondary server). For Apple AirPort Extreme Base Station, you can use the AirPort Admin Utility to configure the addresses of the RADIUS servers.
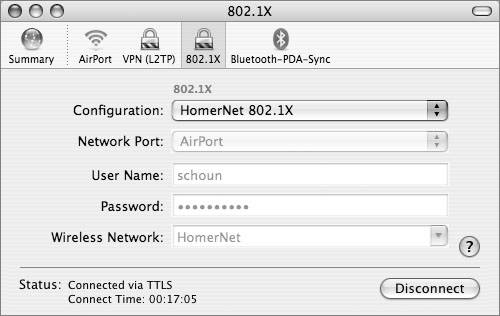
Setting up Mac OS X clients to use WPA Enterprise is reasonably straightforward. To make it even simpler, Apple supports a feature whereby the administrator can save a configuration file that can be placed on each user device. Follow these steps to create such a file:
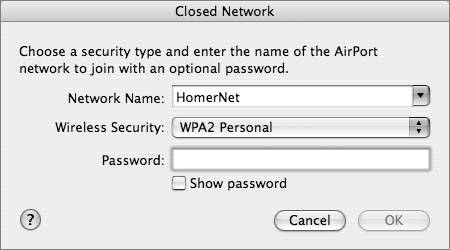
To join a WPA network, users can double-click the configuration file to open it in Internet Connect. When prompted, the users should then enter the user name and password they were given for the network and, if necessary, choose the network from the Wireless Network pop-up menu. Using WPA PersonalIn small and home offices, WPA Personal allows the use of a single, shared password. A RADIUS server is not required. The user enters the password (also called a key) into the access point and each client. WPA takes over from there. The password ensures that only devices and users with proper credentials can join the network. Entering a correct password starts the TKIP encryption process. TKIP derives its encryption keys mathematically from the password and regularly changes and rotates the key so that the same key is never used twice. WPA Personal supports two types of passwords:
TKIP makes it extremely difficult for attackers to derive the key simply by capturing network traffic (as they could with WEP). To increase security, though, it's still a good idea to follow standard password security practices with the key and make sure it's a complicated, somewhat long word or phrase with lowercase and uppercase letters, numbers, and symbols. Also, note that although the key changes (it's temporal), the starting key is a shared key that is configured on the access points and on users' computers. Users are notorious for not keeping secrets. They have a tendency to write passwords on sticky notes. They tell passwords to friends or send them in e-mails, or they type passwords into files stored on their computers. For this reason, WPA Enterprise, which uses a unique password for each user, is preferable. Other than entering the password, the network administrator and users aren't required to do anything to make WPA Personal work, which is beneficial for small businesses and home users where the expertise for setting up a RADIUS server may not exist. For larger networks, however, the added security and the economies of scale associated with having one RADIUS server manage all user credentials for all wireless access points outweigh the disadvantages associated with the need for expertise. If you have more than about five users, WPA Enterprise is recommended over WPA Personal. Comparing WLAN Security MechanismsThe previous sections covered WEP, WEP with 802.1X, WPA Enterprise, and WPA Personal. Each of these mechanisms has a place in configuring WLAN security (although WEP's place should be strictly limited to networks that must support older devices). This table summarizes the features, benefits, and liabilities of the security options covered in the lesson.
|
EAN: 2147483647
Pages: 258