10.8 Decommissioning mailboxes
|
| < Day Day Up > |
|
Inevitably, some of a company's population leaves every year. Administrators need to be ready to secure accounts and mailboxes after users depart, prevent some messages from arriving in the mailbox, and then efficiently process any incoming messages that continue to arrive addressed to former users.
The easiest way to remove an account is to select and then delete it using AD Users and Computers. You can decide whether to remove the Exchange mailbox at the same time. Deleting a record in the AD needs replication to occur to all DCs in the forest before the deletion is completely effective. The AD maintains tombstones to mark deleted accounts and then eventually flushes the tombstones from the AD 60 days (the default) after the account deletion.
Deleting an account in this manner immediately denies access to the mailbox. However, it means that you may not be able to retrieve messages or other items in the mailbox, should the need occur. Note that even if you retain a mailbox with the intention of reviewing its contents to recover corporate information, any encrypted message will be inaccessible unless you know the recipient's private key.
Life would be simple if you could discard unwanted accounts as soon as the owner left the building. However, companies usually have processes to govern how people leave, including returning company property (e.g., lap- tops, phones, badges, and credit cards), handling of intellectual property such as documents, and access to computer accounts. The most basic step is to secure accounts against unauthorized access and preserve the information contained in any mailboxes used by the individual who is leaving.
You can quickly secure Windows accounts by disabling the accounts and changing passwords, and then testing to ensure that no one can gain access. Once you have the accounts and mailboxes locked down, it is a good idea to remove the user from internal distribution lists (groups) to prevent the generation of unnecessary messages. Since some Windows 2000 distribution groups are also security groups, this step ensures that you remove access from resources such as public folders and file shares. In addition, you should hide the user's mailbox from the GAL. Some administrators also add a comment to one of the fields in the account to indicate that the user has left and to set a date when they plan to delete the account permanently. For example, you can prefix the display name with something like "** 20031001" to show that the account is deleted and that you plan to remove it on October 1, 2003.
From a housekeeping perspective, unless you are compelled to keep accounts for longer, it is best to remove disabled accounts after a couple of months. If you put an expiration date on accounts as they are disabled, you can quickly scan the AD on a regular basis to locate expired accounts and permanently delete them. Two months is usually more than enough for an authorized user to review a mailbox's contents and decide whether to recover any information. Because the contents of a mailbox are personal and each country has its legal conditions that apply to situations in which representatives of a company access someone's mailbox, you should ensure that any access to the contents of a deleted mailbox can be defended under law.
10.8.1 Mailboxes and document retention
The next step depends on the type of document retention policy that is in place. While email can contain significant intellectual capital, some companies take positive steps not to retain information and move to delete mail-boxes and any personal documents that belong to users who leave as soon as practically possible. The logic here is that opposition lawyers cannot discover deleted messages and documents during future legal actions, so it is a form of electronic shredding. Of course, smart lawyers know that backup tapes probably exist that contain copies of the information they are looking for, so deleting a mailbox is not a sure way of hiding anything.
Most companies keep mailboxes around for a set period after the user leaves, normally between 30 days and 3 months, to allow someone to examine the contents of the mailbox to determine whether anything of value exists that the company should retain. Before you finally delete the mailbox, you can use a tool such as ExMerge to export the contents of the mailbox to a PST, which you can then archive to a writeable CD just in case you need the information again. You can apply much the same policy to the user's PC, where a coworker reviews the contents of the hard disk before an administrator wipes the PC and reloads it with a fresh copy of the operating system and applications. Again, you can export documents and other interesting material to a CD before finally rebuilding the PC.
Other companies are constrained by legal requirements as to the actions that they can take with mailboxes. If a third party is suing your company, your lawyers may require the company to keep messages sent or received by any individual who may potentially be connected to the case. If one of those individuals leaves the company, you must retain his or her mailbox until the case concludes, just in case. Exporting a mailbox to a PST may meet the legal requirements, but you should check to make sure.
In situations where document retention policies are in place or you have to keep a mailbox to satisfy a legal requirement, you can use a forwarding address to direct new messages to another user, who will then process the message. Alternatively, you can create an Outlook rule to delete new messages as they arrive, or even send an informational message to tell people who attempt to send messages to the mailbox that the user has left the company.
10.8.2 Creating a blackhole for messages
If you do not want to go to the trouble of setting up a mechanism to process incoming messages, you can create a blackhole in the form of a "Disappearing Users" distribution group that has no members and then add the SMTP addresses of former users to the email addresses of the group. This creates a blackhole for messages to go into, since the Exchange Routing Engine will be able to locate a valid address to deliver messages to, but they actually arrive nowhere. This is an effective way to stop incoming spam addressed to users who leave your company. Remember that you must delete or change the SMTP address on the user's mailbox before adding it to the distribution group, since AD Users and Computers checks to ensure that an SMTP address is unique within the organization before adding it to an object. An alternative idea is to create a mailbox and add all of the email addresses for former users to it. The advantage gained in this approach is that you can then use Outlook rules to process and respond to incoming messages, as described later on in this section.
10.8.3 Redirecting messages
Forwarding addresses allows you to tell Exchange to redirect messages sent to another mailbox. The recipient can be any mail-enabled object in the Active Directory: another mailbox (the logical choice), a contact, a public folder, or even a distribution group. The same restrictions apply for Exchange 5.5, where the selected object must be in the Directory Store.
Forwarding messages to a public folder or distribution group does not make much sense, but there can be situations where it is appropriate to forward messages to a mail-enabled contact. For example, assume that someone who uses another email system assumes the responsibilities of the user who leaves. In this instance, you create a mail-enabled contact in the AD and then select the contact as the forwarding address when editing the Delivery Options for the user who has left, as shown in Figure 10.39.
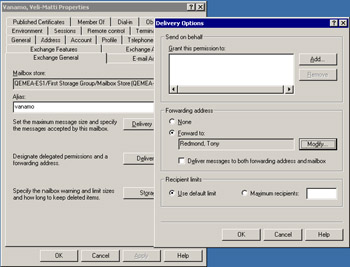
Figure 10.39: Specifying a forwarding address.
Using a forwarding address is appropriate when the user is involved in many ongoing projects and you want to preserve continuity. However, it does place a certain load on the user to whom you forward the messages, since he or she will have an extra volume of email to process, including some messages that are probably not business related. The only clue that a recipient gets that a message was not originally sent to him or her is the address shown for the recipient, and it is easy to miss this!
10.8.4 Using Outlook rules to process messages
Outlook includes a powerful rules engine that you can use to perform many tasks. In this case, the rule for processing new messages is simple and consists of the following steps:
-
Process all new messages that arrive in the mailbox.
-
Move a copy of the messages to the Deleted Items folder.
-
Optionally, send a response back to the originator to tell him or her that the user is no longer available at this address.
Figure 10.40 shows an appropriate rule as viewed through the Rules wizard. You create and edit text in the message containing the reply as you create (or later modify) the rule, and it is stored as a hidden item in the mailbox. You create or edit text in the message in exactly the same way as you create text for a regular message, so you can include any formatting required to get your message across. It is important to create a server-side rule to allow Exchange to process messages as they arrive. Otherwise, if you create a client-side rule, you have to keep Outlook running to execute the rule. Some conditions exist that force Outlook to create a client-side rule, including any attempt to delete an item permanently. For this reason, it is best to move incoming items into the Deleted Items folder, where an administrator can review and then delete the items or leave them for automatic cleanup by the Mailbox Manager.
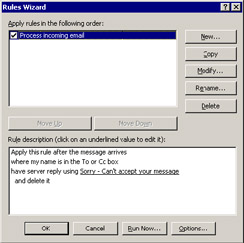
Figure 10.40: Creating a server- side rule to process new messages.
Figure 10.41 illustrates how an originator receives the informational message that you associate with the rule. It is up to you as to how much information you include in the text. Some administrators like to include a forwarding address, but this is perhaps not a great idea if the user has gone to a competitor. If users subscribe to Internet mailing lists managed by list servers, it is likely that they will forget to unsubscribe when they leave the company. As stated, our rule will work and Exchange will automatically move any messages that come from the mailing list to the Deleted Items folder. However, Exchange sends the reply message to the list server, which will then forward it to all its subscribers in the same way that it deals with every other message sent to the list. Recipients will probably not appreciate receiving these messages, so we can add another rule to examine incoming messages to see whether they originate from a list server and then quietly delete any that do.
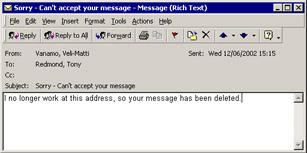
Figure 10.41: The message sent to the originator.
Of course, this approach means that the list is inaccurate, because it contains invalid subscriptions, but this is not the problem you want to solve. You could go through the mailbox to try to pick out messages generated by lists and send a note to the list administrator to ask him or her to remove the user. Some lists include unsubscribe instructions in the messages. This often requires that you send a message to the list server from the user's email address; the easiest way to do this is to configure Outlook Express to send a message with the former user's old email address. If you feel that this is too much work, you can create a rule, similar to that shown in Figure 10.42, to delete the messages silently. Obviously, you must ensure that Outlook executes this rule first before it processes other messages.
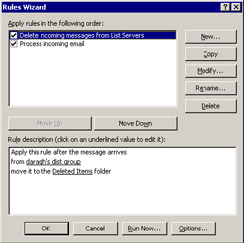
Figure 10.42: Processing for list server messages.
10.8.5 User death
The requirement to handle mailboxes for users who die is something that we would perhaps not like to think about, but it does happen. In this instance, the need to preserve information that might be useful to the company still exists, but it is easy to cause some distress to coworkers of the recently departed if a rule or auto-reply generates a message that apparently comes from the user after his or her death. For this reason, take the normal steps to remove the mailbox from the GAL and distribution lists and then check that an auto-reply or rules are not in place.
Handling the mailboxes of former users is something you probably never think about before the need occurs. Apart from the technical aspects of how to handle new messages sent to former workers as they arrive, you may have to comply with legal or document retention policies. As with documents, mailboxes are part of the intellectual capital of an organization, so a well-thought-out method to decommission mailboxes that allows you to secure intellectual capital should be part of an Exchange administrator's toolkit.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 188