Security Policy Administration
This section of the chapter illustrates how to configure the following:
-
RADIUS servers
-
Intrusion detection
-
IP preferences
-
Connection limits
Defining RADIUS Servers
Remote Authentication Dial-In User Service (RADIUS) servers allow you to configure authentication for an ISA server when it is not a member of the client's domain.
For more information about RADIUS in Windows, see http://www.microsoft.com/windowsserver2003/technologies/ias/.
To identify the RADIUS servers used by ISA Server when RADIUS authentication is selected, follow these steps:
-
Open the ISA Server Management console. In the console tree, expand the server name, expand the Configuration node, and click General.
-
In the details pane, under Additional Security Policy, click Define RADIUS Servers.
-
In the RADIUS Servers dialog box, click Add.
-
In the Add RADIUS Server dialog box, shown in Figure 10-5, you need to provide the following information:
-
Server Name Text box provided for you to type either the server name or IP address of the RADIUS server.
Note If using a server name, ensure a fully qualified domain name (FQDN) is specified and that the ISA server can resolve the server name using Domain Name System (DNS).
-
Server Description Text box provided for you to type a server description (optional).
-
Shared Secret Text box provided for you to configure a shared secret. If you want to configure a shared secret, click Change. In the Shared Secret dialog box, type a new secret, confirm the shared secret, and click OK.
Note The shared secret should be highly complex, and therefore more secure. For example, it should contain more than 24 characters and include both uppercase and lowercase letters, numerals, and special characters (such as $%^&).
-
Port Text box provided for you to specify the port number to be used when communicating with the RADIUS server.
-
Time-Out (Seconds) Text box provided for you to specify the time out value in seconds.
-
Always Use Message Authenticator Check box provided to ensure a message authenticator is used when authenticating a client to the RADIUS server. Not all RADIUS clients support this setting, so verify that your clients are configured correctly.
Note See the ISA Server Help file and your RADIUS server documentation for more information.
-
-
In the RADIUS Servers dialog box, once someone has added at least one RADIUS server, you can choose to edit or remove the server, and you can also change the order of the RADIUS servers to determine the order in which the servers are queried. Click OK.
-
In the details pane, click Apply to save your changes, and then click OK.
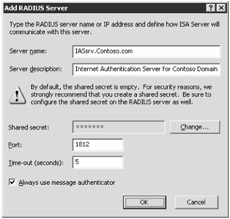
Figure 10-5: The use of a RADIUS server is beneficial for authentication when the Web client and ISA Server are not in the same domain.
Configuring Intrusion Detection
Intrusion detection and IP preferences are two ways to configure your ISA server to respond to various attacks, whether application-level attacks or port attacks. In the next two sections, we discuss these options.
Although ISA Server always protects against these attacks, you will be informed of them only if intrusion detection is configured to do so. Intrusion detection is now enabled by default in ISA Server 2004, whereas in ISA Server 2000 it shipped disabled out of the box. To select the types of attacks that ISA Server will warn you against, follow these steps:
-
Open the ISA Server Management console. In the console tree, expand the server name, expand the Configuration node, and click General.
-
In the details pane, under Additional Security Policy, click Enable Intrusion Detection And DNS Attack Detection.
-
In the Intrusion Detection dialog box, two tabs have configurable information: Common Attacks and DNS Attacks. On the Common Attacks tab, select the Enable Intrusion Detection check box to enable intrusion detection. To enable detection of particular attacks, select the appropriate check boxes after you understand the meaning of each attack as described in Table 10-2.
Tip For more detailed descriptions of the abovementioned attacks, see the ISA Server Help file.
ISA Server also includes the ability to track intrusion detection at the application level by using DNS intrusion detection filters. By default, the DNS intrusion detection filters are enabled, regardless of whether you've enabled intrusion detection. To enable detection of particular attacks, click the DNS Attacks tab, and select the appropriate check boxes after you understand the meaning of each attack as described in Table 10-3.
-
Click OK once you have selected the appropriate attacks to monitor.
-
In the details pane, click Apply to save your changes, and click OK.
| Type of Intrusion Attack | Description |
|---|---|
| Windows Out-Of-Band (WinNuke) | This type of attack is a denial of service (DoS) attack used to make a computer crash or a network interface unavailable (detection enabled by default). |
| LAND | This type of attack creates a spoofed IP address and source port to match the destination IP address and destination port. This process creates a loop to bring down the affected computer (detection enabled by default). |
| Ping Of Death | This type of attack causes a buffer overflow in the computer when the computer attempts to respond continually to an extremely large Internet Control Message Protocol (ICMP) echo request packet (detection enabled by default). |
| IP Half Scan | This type of attack establishes half of the common three-step Transmission Control Protocol/Internet Protocol (TCP/IP) communication session to consume resources on the system that is being attacked (detection enabled by default). |
| UDP Bomb | This type of attack uses a maliciously configured User Datagram Protocol (UDP) packet to create an operating system failure (detection enabled by default). |
| Port Scan | This type of probe detects open ports on a computer to identify potential vulnerabilities (detection disabled by default). |
| Type of DNS Intrusion Attacks | Explained |
|---|---|
| DNS Hostname Overflow | This type of attack is a DNS response to a host name that exceeds a certain fixed length, causing an internal buffer overflow. This overflow allows a remote attacker to execute commands on the targeted computer. |
| DNS Length Overflow | This type of attack occurs when an IP address contains a length field larger than 4 bytes, causing an internal buffer overflow. This overflow allows a remote attacker to execute commands on the targeted computer. |
| DNS Zone Transfer | This type of attack occurs when a computer uses a DNS client application to transfer DNS zones from an internal DNS server to an external DNS server, which makes sensitive information about your network vulnerable to interception. |
Intrusion Detection Alerts and Actions
ISA Server includes alerts for intrusion detection and DNS intrusion. You can configure each of these alerts to perform a variety of actions when an attack is detected and the alert is triggered:
-
Stop selected services
-
Start select services
-
Send an e-mail message or page
-
Run a previously specified program or script
-
Write an event to the event log
Each of these actions is discussed in detail in Chapter 6, "Monitoring and Reporting," in the section entitled "Alerts." One notable feature available is the Log Dropped Packets check box, which, when selected, logs the packets that the ISA server detects as being part of an attack. Selecting this option helps to identify the types of attacks being performed against your system.
| Tip | This option will also show packets dropped when denied by a policy rule when you select the Log Packets That Match This Rule check box in the policy rule. |
Defining IP Preferences
The second option for providing improved security is the configuration of IP preferences, which are used to configure how ISA Server handles IP packets.
To configure IP preferences, complete the following steps:
-
Open the ISA Server Management console. In the console tree, expand the server name, expand the Configuration node, and click General.
-
In the details pane, under Additional Security Policy, click Define IP Preferences.
-
In the IP Preferences dialog box are three tabs, which are described in Table 10-4.
-
Click OK once you have configured the IP preferences.
-
In the details pane, click Apply to save your changes, and click OK.
| Tab Name | Explanation | Setting Recommendation |
|---|---|---|
| IP Options | Allows you to configure ISA Server to deny packets that have an IP Options flag set in the header, or to drop packets with only specific IP options enabled. | Ensure that the Enable IP Options Filtering check box is selected. Source routing should be disabled because an attacker can use source routing to reach addresses on an internal network that normally are not reachable. |
| IP Fragments | Allows you to block any packets containing IP fragments. Configurable through a single check box. | To enable, select the Block IP Fragments check box. Enabling this feature can interfere with streaming audio and video, plus L2TP over IPSec connections. You will be presented with a warning dialog box if you select this check box to confirm you want to enable. |
| IP Routing | Allows you to configure ISA Server to route the original packet from network to network. When disabled, ISA Server only routes the data, not the original packet. | To disable, clear the Enable IP Routing check box. Disabling IP routing provides additional security, but significantly affects the performance of protocols like File Transfer Protocol (FTP) and H.323 that pass large amounts of data through secondary connections. ISA Server's application filters for such applications allow enhanced performance by using kernel mode transfers in these caseswhen IP routing is enabled. |
Defining Connection Limits
ISA Server can control the client connections made to it or through it to help prevent malicious traffic, such as worms. The connection limits are configurable for non-TCP connections and TCP connections. Additionally, the connection limits can be checked by access rules, Web publishing rules, and server publishing rules. If a connection limit threshold is exceeded, an alert is triggered, providing you with information of the client IP that triggered the alert. Be cautious of setting this value too low (preventing valid sessions) and too high (missing the opportunity to detect an attack). The default values provided are generally acceptable.
To configure connection limits, complete the following steps:
-
Open the ISA Server Management console. In the console tree, expand the server name, expand the Configuration node, and click General.
-
In the details pane, under Additional Security Policy, click Define Connection Limits.
-
In the Connection Limits dialog box, shown in Figure 10-6, you can determine the connection limits made to or through the ISA server using the following settings:
-
Limit The Number Of Connections Use this check box to enable or disable this functionality.
-
Connections Created Per Second, Per Rule (Non-TCP) Configured to 1,000 by default. This value applies to all non-TCP connections made per second per rule created in the firewall policy.
Note When this value is exceeded, new connections cannot be established, but existing connections remain connected.
-
Connection Limit Per Client (TCP And Non-TCP) Configured to 160 by default. This value applies to a single client.
Note When this value is exceeded, new connections cannot be established, but existing connections remain connected.
-
Custom Connection Limit Allows you to configure a value that would be applied to specific IP addresses of clients. The default value is 1,000,000.
-
Apply The Custom Limit To These IP Addresses You can click Add to select computer sets that should be configured to use the custom connection limits.
-
-
Click OK when you have configured the connection limits.
-
In the details pane, click Apply to save your changes, and click OK.
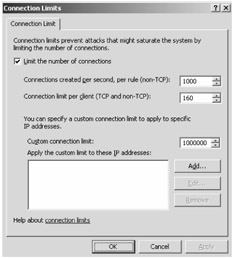
Figure 10-6: Connection limits are important for preventing a worm from bringing down your corporate network, as alerts will be triggered when the values you have set are exceeded.
EAN: 2147483647
Pages: 173
- Assessing Business-IT Alignment Maturity
- Measuring and Managing E-Business Initiatives Through the Balanced Scorecard
- Technical Issues Related to IT Governance Tactics: Product Metrics, Measurements and Process Control
- Governing Information Technology Through COBIT
- Governance in IT Outsourcing Partnerships