Overview of ISA Server Client Types
ISA Server 2004 clients are determined by how the computer requesting external resources connects to and through the ISA Server firewall. These three clients can be used individually or in conjunction with one another:
-
SecureNAT Any computer that is configured to route requests to the ISA server by making it the default gateway, or by setting up routes in a complex network that has other routers that lead to the ISA server.
-
Web proxy Requires configuring any Conseil Européen pour la Recherche Nucléaire (CERN)—compliant client (which includes all major Web browsers) to direct HTTP, HTTPS, and FTP download requests to the Firewall service on ISA Server.
-
Firewall client This software can be installed on Microsoft Windows 98 and Microsoft Windows NT 4.0 operating systems and above. It directs requests to the Firewall service on ISA Server, and can support many protocols.
Table 4-1 shows these clients and their capabilities.
| Web Proxy | Firewall Client | SecureNAT | |
|---|---|---|---|
| Supported protocols | HTTP, HTTPS, FTP, and Gopher | Limited by protocol rules | Limited by protocol rules; can't support secondary connections without use of application filters |
| Installation and configuration requirements | No installation required; must configure browsers or Web-based applications | Must install client on Windows and configure it | No installation; might require some client configuration (gateway) |
| Operating system (OS)/application requirements | Any OS with a CERN-compatible Web application | Only Windows operating systems (OSs) are supported | No requirements |
| User authentication | Yes | Yes | For VPN clients only |
| Advantages | Simple, with many options for automating configuration | Provides access to all protocols; ;supports authentication | Easiest configuration in a simple network |
| Disadvantages | Limited only to Web protocols | Must install software on client | Complex networks require additional configuration; limited support of complex protocols without a filter, and no support for authentication |
Choosing the Right Client
Choose the client you require for your environment based on the needs of your organization. Figure 4-1 illustrates the strengths and weaknesses of the different clients.
-
Use the SecureNAT client if you don't need authentication of users (and the resulting ability to track users in reports), and want the least amount of configuration possible.
-
Use the Web Proxy client if you only require HTTP, HTTPS, and FTP traffic.
-
Use the Firewall client if you need to authenticate users and require support for many different, or complex, protocols.
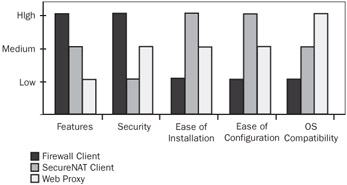
Figure 4-1: This chart shows how the different ISA Server clients compare based on different requirements.
You are not tied to just a single client, however. You can use all three clients together on a single machine, should you desire. See Table 4-2 for a reference showing which clients are most suitable for specific requirements.
| Requirement | Preferred Client |
|---|---|
| Avoid installing software | SecureNAT |
| Forward caching (caching only) | SecureNAT or Web proxy |
| Authenticated clients | Firewall client or Web proxy |
| Publish servers | SecureNAT |
| Non-Windows OS | SecureNAT or Web proxy |
| Note | ISA Server handles all HTTP requests, regardless of the client type, as though they are Web Proxy clients. |
EAN: 2147483647
Pages: 173