What to Expect After Installation
As part of Microsoft's Trustworthy Computing Initiative, ISA Server 2004 is secure by design, secure by default, and should be secure in deployment. Out of the box, you will not have connectivity to the Internet, but must take action to configure your ISA server to provide the connectivity that is appropriate for your environment.
| Caution | Be aware that the default installation of ISA Server 2004 allows access to certain domains to help manage ISA Server through the Allowed Sites configuration group in the system policy. By default, the ISA Server computer can access the following domains:
See Microsoft Knowledge Base article 867687 to learn more about the reasons behind this configuration and how to modify it. |
Know Your System Policies
ISA Server 2004 introduces a new term: system policy. This policy is configured from within the Firewall Policy node, and defines how your ISA server (the computer system) behaves in relation to the rest of the network. For example, you will use system policies to allow remote administration of the ISA server from other computers on your network.
| Tip | Many people familiar with ISA Server 2000 create firewall policies to enable the ISA server to communicate with other systems. Be sure to familiarize yourself with the system policies before creating any firewall policies. |
Your ISA server will have system policies that allow certain types of internal traffic to your ISA server, and the network relationship between the internal network (all IP addresses that fall within the internal IP address range defined in the Networks node) and the external network (all IP address ranges that are not explicitly defined in the Networks node) is set to perform NAT on traffic, rather than to route it.
To view and configure system policies, follow these steps:
-
In the ISA Server Management console, expand the ISA Server node, then click the Firewall Policy node. The Firewall Policy tab is displayed in the center pane.
-
In the right pane, click the Tasks tab, then in the System Policy Tasks section click Show System Policy Rules. The system policies are then displayed in the center Firewall Policy pane as shown in Figure 2-4.
-
Select the system policy you wish to manage by double-clicking it to activate the System Policy Editor, as shown in Figure 2-5. On the General tab, you can choose to enable the policy and certain features. There is also another tab—either To or From—that allows you to choose the destination or sources to which the policy applies.
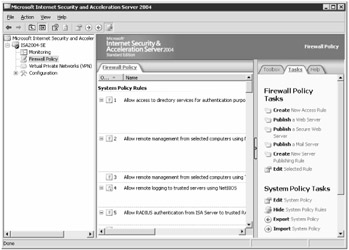
Figure 2-4: When you click Show System Policy Rules on the Tasks tab, system policies appear in the center Firewall Policy pane.
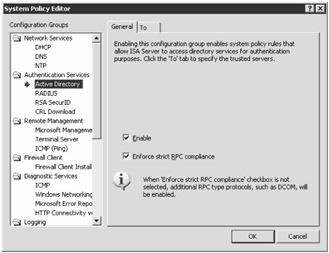
Figure 2-5: The System Policy Editor allows you to configure system policies from a single interface.
EAN: 2147483647
Pages: 173