Chapter8.Establishing Security Model Settings
Chapter 8. Establishing Security Model SettingsIN THIS CHAPTER
Security is separated into two distinct criteria: use permissions (functionality) and data permissions (data access). Use permissions define what a user can do in the system, and data permissions define what data will populate views visible by the user. Use permissions are maintained by the Group to which a user is assigned, and data permissions are maintained by the Category or Categories associated with the Group to which a user is assigned. Hence, the user's system security, what a user can do and what data a user can see, is defined through a Group and Category. It is important to remember that the security model in Microsoft Office Project Server 2003 is a matrix that allows a user to be assigned to multiple Groups depending on her role in the system. Also, multiple Categories can be assigned to a Group to define specific conditional data requirements for users in the Group. These combinations provide a mix of functionality and data access appropriate for the roles the user will perform using Project Server. Project Server security is complex. A thorough understanding of and adherence to best practices will guarantee a successful configuration and enhance your ability to easily maintain the complex criteria of Project Server system security as shown in Figure 8.1. Figure 8.1. Security model process flow diagram.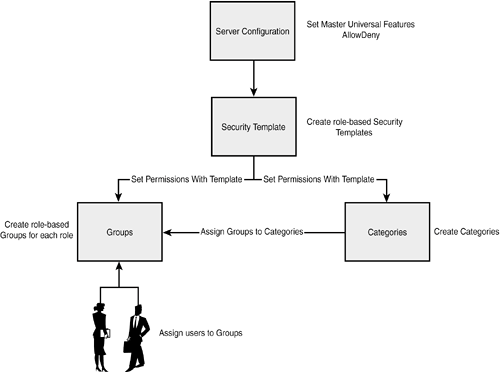 |
EAN: 2147483647
Pages: 227