The Architecture of the WebLogic Security Service
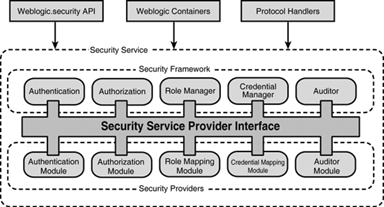
| This section describes the architecture of the WebLogic Security Service. As shown in Figure 26.3, the architecture comprises four major components , which are discussed in the following sections. Figure 26.3. The architecture of the WebLogic Server Security Service. The WebLogic Security FrameworkThe primary function of the WebLogic Security Framework is to provide a simplified application programming interface (API) that security and application developers can use to define security services. The framework comprises interfaces, classes, and exceptions located in the weblogic.security.service package. The WebLogic Security Framework also acts as an interface between the WebLogic containers (Web and EJB), the Resource Adapter, and the security providers, delegating requests to the appropriate security plug-in through the corresponding SPI. The Security Service Provider InterfacesSecurity in WebLogic Server is based on a set of Security Service Provider Interfaces (SSPIs) for developing security providers that can be plugged into the WebLogic Security Framework to provide security services to WebLogic applications. Security providers are developed by implementing the appropriate SSPIs from the weblogic.security.spi package to create runtime classes. The current security SPIs available for WebLogic Server include Authentication, Authorization, Auditing, Credential Mapping, Role Mapping, and Public Key Infrastructure. The WebLogic Security Framework knows what security providers are installed, when they should be used, and how decisions should be made. However, it is not the decision maker on security; these decisions are brokered to security providers. The Security Provider DatabaseThe primary role of a security provider database is to store the data the security provider requires to provide a security service, as in these examples:
Types of security provider databases include a relational database that has been structurally aligned with the requirements of a security provider, a properties file, and an LDAP server. By default, a complete embedded LDAP server is provided out-of-the-box with WebLogic Server to support the WebLogic Authentication, Authorization, Role Mapping, and Credential Mapping security providers. You can use this WebLogic-embedded LDAP server to do the following:
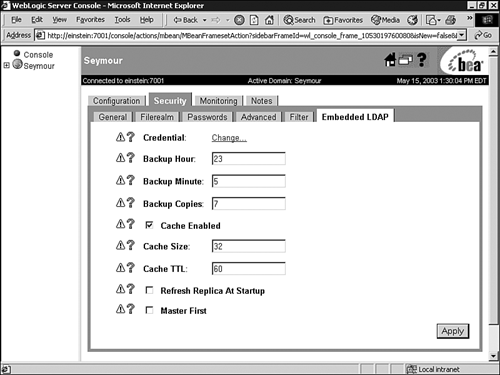
A WebLogic LDAP server is created for each WebLogic Server instance in a domain. However, the WebLogic LDAP server associated with the WebLogic Administration Server is considered the master LDAP server. The information stored in this LDAP server is managed by the WebLogic Administration Server via the Administration Console, and then replicated to the other WebLogic LDAP servers associated with the domain's managed servers. You can configure properties of the master WebLogic LDAP server, such as backup, cache, and replication settings, via the Administration Console as follows :
After you have modified your LDAP server's Credential attributes and rebooted your WebLogic server, you can view the contents of your WebLogic LDAP server by using any LDAP browser, such as Softerra's LDAP Browser 2.5 (http://www.ldapbrowser.com) or the University of Chicago's LDAP Browser\Editor (LBE) Java utility, which are freeware. To use an LDAP browser to navigate the hierarchy of the WebLogic LDAP server, use the following LDAP connection information:
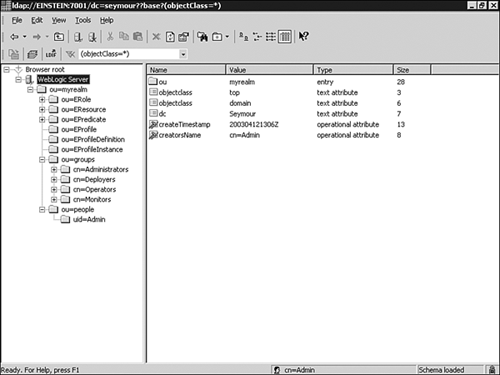
Figure 26.5 shows the contents of the WebLogic LDAP server using the Softerra LDAP browser. Figure 26.5. View the contents of the embedded LDAP server through an LDAP browser. Tip An LDAP browser can also be used to export and import data stored in the embedded LDAP server. Because this LDAP server is specifically structured to support the WebLogic security providers only, you cannot add attributes to its structure. |
EAN: 2147483647
Pages: 360