Securing and Monitoring Remote Administration
| Remote administration of servers is a valuable tool for distributed IT organizations. It is important, though, when enabling remote administration features in Windows Server 2003, to maintain a high level of security for the server resources. Windows Server 2003 installs but disables remote access features by default for security purposes. When enabling these features, ensure that only administrators with the proper credentials will be able to remotely gain access to the server. This section provides tips on securing and monitoring remote administration. Securing Remote AdministrationThe security implications of enabling remote administration are fairly obvious. With remote administration features enabled, users who log on remotely can perform tasks as if they were sitting right in front of the server. Depending on the role the server plays in the organization, unauthorized access to a server can jeopardize a company's entire business. For this reason, it is important to protect the server from unauthorized access. Part I of this book, "Security Solutions," provides detailed approaches to securing Windows Server 2003. The following checklist points out key items to keep in mind for servers with remote administration features enabled:
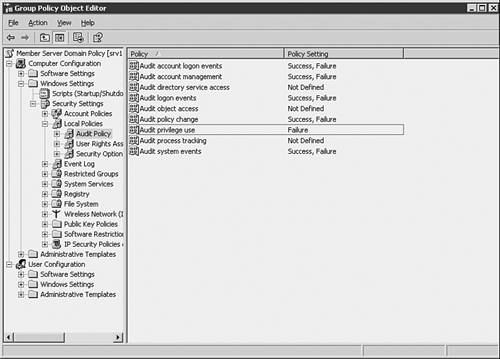
Monitoring Remote AdministrationProper auditing practices go hand-in-hand with any good security policy. The Terminal Services Manager tool can be used to view and interact with remote connections in real time, but this is only helpful to view a server's current status. It is important to maintain and review the security logs of servers, as well as set up the proper items to monitor for events that occur when you are not actively watching for remote connections. Auditing policies can be enforced on a server-by-server basis by applying security templates through the Security Configuration and Analysis MMC snap-in. In an Active Directory environment, auditing policies can be applied by group policy, as shown in Figure 8.7. Figure 8.7. Setting up an audit policy in group policy. For servers enabled for remote administration, it is important to audit the success and failure of logon events, account management, policy changes, and system events. Also, failure of privileged use events should logged. |
EAN: 2147483647
Pages: 325