Chapter 38: Information Security
|
| < Day Day Up > |
|
With the advent of computerization, information security has gained importance because, after all, "information is power". Organizations have to ensure that their information is not stolen or tampered with, either by employees or outsiders. This has become a very challenging task, particularly with the convergence technologies. On one hand, antisocial elements use the technology to hack computers, spread viruses, and pose many security threats to the organizations. On the other hand, the organizations need to devise methods to contain the security threats by employing the latest technologies. Cryptography is used extensively for providing secure applications. Steganography is now being used in conjunction with cryptography to provide highly secure information systems. In this chapter, we will study the various security threats and how to overcome them using cryptography and steganography. We have discussed many security protocols in various chapters of this book, and this chapter gives an overview of security issues and solutions, with special emphasis on multimedia-based information security products.
38.1 INFORMATION LEAKS
Every organization has to protect its information. Depending on the type of organization, this information is of different categories—organizations involved in design have to protect their design documents as the intellectual property developed is very precious; organizations involved in marketing have to protect their market research organizations involved in services (for example, hospitals) have to protect the information of their clients (for example, patient information), and so on. Surveys show that in 70% of cases, the employees of an organization leak information. Sometimes employees leak information out of ignorance, and some employees intentionally commit a crime. Many organizations are now resorting to surveillance—monitoring the activities of employees to check information leaks.
To protect valuable information, every organization needs to make use of surveillance equipment to contain information leaks.
As shown in Figure 38.1, information can be leaked by an employee through an office telephone, a fax machine, a mobile phone, or a computer. Many organizations listen in on the telephone conversations of employees. Similarly, all e-mails can be checked to find out whether any information is being leaked.
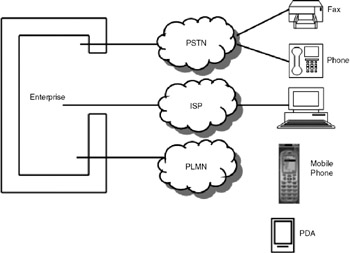
Figure 38.1: Information leaks.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 313