Understanding and Using the Microsoft Active Directory Migration Tool 2.0 (ADMT v2)
| < Day Day Up > |
| The Active Directory Migration Tool (ADMT) is an effective way to migrate users, groups, and computers from one domain to another. It is robust enough to migrate security permissions and Exchange mailbox domain settings, and it supports a rollback procedure in the event of migration problems. ADMT is composed of several components and functions:
ADMT v2 installs very easily, but requires knowledge of the various wizards to properly use. In addition, a best-practice process should be used when migrating from one domain to another. The migration example illustrated in the following sections describes the most common use of the ADMT, an inter-forest migration of domain users, groups, and computers into another domain. This procedure is by no means exclusive, and many other migration techniques can be used to achieve proper results. Matching the capabilities of ADMT with the migration needs of an organization are important. Deploying ADMT in the LabADMT v2 comes with unprecedented rollback capabilities. Not only can each wizard be tested first, the last wizard transaction can also be rolled back in the event of problems. In addition to this, however, you should reproduce an environment in a lab setting and test a migration in advance, to mitigate potential problems that might arise. The most effective lab can be created by creating new domain controllers in the source and target domains, and then physically segregating them into a lab network, where they cannot contact the production domain environment. The Operations Master (OM) roles for each domain can then be seized for each domain using the ntdsutil utility, which creates exact replicas of all user, group, and computer accounts that can be tested with the ADMT. Installing and Configuring ADMTThe installation of the ADMT component should be accomplished on a domain controller in the target domain to which the accounts will be migrated. To install, follow these steps:
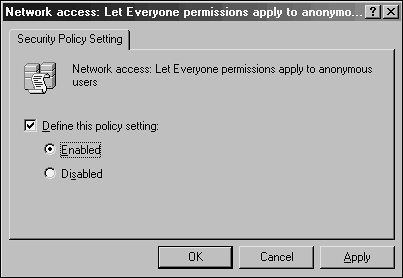
Domain Migration PrerequisitesAs previously mentioned, the most important prerequisite for migration with ADMT is lab verification. Testing as many aspects of a migration as possible helps establish the procedures required and identify potential problems before the procedures are done in the production environment. There are several functional prerequisites that must be accomplished before the ADMT can function properly. Many of these requirements revolve around the migration of passwords and security objects, and are critical for this functionality. Creating Two-Way Trusts Between Source and Target DomainsThe source domain and the target domains must be able to communicate with each other and share security credentials. Consequently, it is important to establish trusts between the two domains before the ADMT can be run. Assigning Proper Permissions on Source Domain and Source Domain WorkstationsThe account that will run the ADMT in the target domain must be added into the Builtin\Administrators group in the source domain. In addition, each workstation must include this user as a member of the local administrators group for the computer migration services to be able to function properly. Domain group changes can be easily accomplished, but a large workstation group change must be scripted, or manually accomplished, prior to migration. Creating a Target OU StructureThe destination for user accounts from the source domain must be designated at several points during the ADMT migration process. Establishing an OU for the source domain accounts can help simplify and logically organize the new objects. These objects can be moved to other OUs after the migration and this OU can be collapsed , if desired. Modifying Default Domain Policy on Target DomainUnlike previous versions of Windows Operating Systems, Windows Server 2003 does not support anonymous users authenticating as the Everyone group. This functionality was designed to increase security. However, for ADMT to be able to migrate the accounts, this must be disabled. After the process is complete, the policies can be reset to the default levels. To change the policies, follow this procedure:
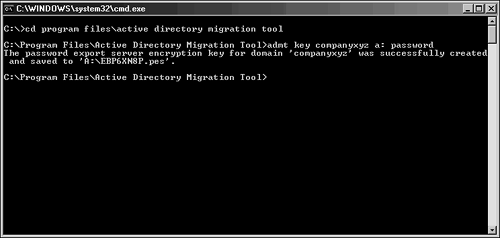
Exporting Password Key InformationIf current passwords will be migrated, a 128-bit encrypted password key from the target domain should be installed on a server in the source domain. This key allows the migration of password and SIDHistory information from one domain to the next. To create this key, perform the following procedure from the command prompt of a domain controller in the target domain where ADMT was installed:
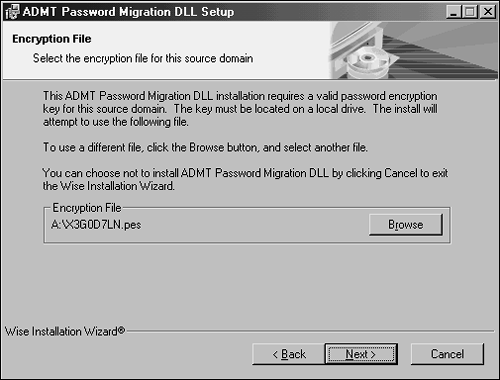
Installing Password Migration DLL on Source DomainA special Password Migration DLL should be installed on a domain controller in the source domain. This machine will become the Password Export Server for the source domain. The following procedure outlines this installation:
Setting Proper Registry Permissions on the Source DomainThe installation of the proper components creates special Registry keys, but leaves them disabled by default, for security reasons. A specific Registry key should be enabled to allow passwords to be exported from the Password Export Server. The following procedure outlines the use of the Registry Editor to perform this function:
At this point in the ADMT process, all prerequisites have been satisfied and both source and target domains are prepared for the migration. |
| < Day Day Up > |
EAN: 2147483647
Pages: 393