| Setting up a network is an intensive planning exercise for both network and system administrators. No two networking environments are alike. There is typically a lot of networking electronics to which your system is connected. There are many useful commands related to testing connectivity to other systems and networking configuration. Should you encounter a problem, you want to have an understanding of some networking commands that can be lifesavers. In addition, you can encounter some tricky aspects to networking setup if you have some networking hardware that your UNIX systems must interface to, such as routers, gateways, bridges, etc. I give an example of one such case: connecting a UNIX system to a router. At the same time, I cover some of the most handy networking commands as part of this description. Consider Figure 13-11, in which a UNIX system is connected directly to a router. Figure 13-11. UNIX System and Router Example 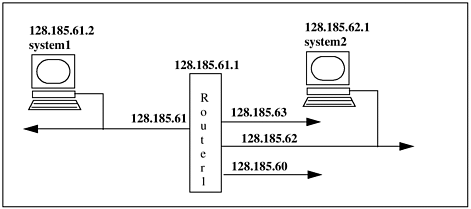 Here we have a UNIX system connected to segment 128.185.61. This is a class "B" Internet address with subnetting enabled. The /etc/hosts file needs to have in it the UNIX system with node ID 2, the router, and any other systems on this segment or segments on the other side of the router. If the router is properly configured, we should be able to seamlessly connect from 61 to systems on segments 60, 62, and 63. The router should be configured to allow our system to connect to systems on other segments (60, 62, and 63) by going through the router. Some unforeseen configuration was required to make this simple network operate seamlessly. In this case, a problem occurred getting system1 to connect to systems on the other side of the router on 60, 62, and 63. Before discussing the additional configuration that needed to be done, I first show the /etc/hosts file and then use some very useful UNIX commands that show the state of the network. Here is the /etc/ hosts file showing just the UNIX system and router: | $ cat /etc/hosts | | 127.0.0.1 | localhosts loopback | | 128.185.61.1 | router1# router | | 128.185.61.2 | system1# UNIX system on 61 | | 128.185.62.1 | system2# UNIX system on 62 |
This host file is simple and allows system1 to connect to router1 and system2. The connection from system1 to system2 is accomplished by going through the router. ping Let's look at one of the most commonly used networking commands - ping. This command is used to determine whether or not a connection exists between two networking components. ping is a simple command that sends an ICMP echo packet to the host you specify once per second. You may recall that ICMP was covered earlier under the network, or third layer. ping stands for Packet InterNet Groper. ping differs somewhat among UNIX variants, mostly in the reporting that ping produces when no options are provided. Some systems provide performance information when ping is issued with no options; others report that the system "is alive". The following is an example of checking the connection between the local system and another system on the network called austin: martyp $ ping austin austin is alive martyp $ You can adjust the packet size and number of iterations on most UNIX variants as in the HP-UX example shown below specifying a packet size of 4096 and interval of 5: # ping l2 4096 5 PING l2: 4096 byte packets 4096 bytes from 10.1.1.12: icmp_seq=0. time=2. ms 4096 bytes from 10.1.1.12: icmp_seq=1. time=2. ms 4096 bytes from 10.1.1.12: icmp_seq=2. time=2. ms 4096 bytes from 10.1.1.12: icmp_seq=3. time=2. ms 4096 bytes from 10.1.1.12: icmp_seq=4. time=2. ms ----l2 PING Statistics---- 5 packets transmitted, 5 packets received, 0% packet loss round-trip (ms) min/avg/max = 2/2/2 # AIX allows you to specify the interval with -I as well as other options, including packet size, and number of iterations. These options are shown for an AIX system in the following example: martyp $ ping -I 5 austin 4096 10 PING austin: 4096 data bytes 4104 bytes from austin (128.185.61.5): icmp_seq=0. time=8. ms 4104 bytes from austin (128.185.61.5): icmp_seq=1. time=9. ms 4104 bytes from austin (128.15.61.5): icmp_seq=2. time=9. ms 4104 bytes from austin (128.15.61.5): icmp_seq=3. time=9. ms 4104 bytes from austin (128.15.61.5): icmp_seq=4. time=8. ms 4104 bytes from austin (128.15.61.5): icmp_seq=5. time=9. ms 4104 bytes from austin (128.15.61.5): icmp_seq=6. time=9. ms 4104 bytes from austin (128.15.61.5): icmp_seq=7. time=9. ms 4104 bytes from austin (128.15.61.5): icmp_seq=8. time=9. ms 4104 bytes from austin (128.15.61.5): icmp_seq=9. time=9. ms ----austin PING Statistics---- 10 packets transmitted, 10 packets received, 0% packet loss round-trip (ms) min/avg/max = 9/9/15 martyp $ In this example, we ping austin every five seconds, with a packet size of 4096 bytes for a total of ten times. Let's now get back to our example. How do I know that I have a connection between system1 and the router and the other systems on the other side of the router? I use the ping command. Here is how I know that system1 is connected to router1: $ ping router1 PING router1: 64 byte packets 64 bytes from 128.185.61.2: icmp_seq=0. time=0. ms 64 bytes from 128.185.61.2: icmp_seq=1. time=0. ms 64 bytes from 128.185.61.2: icmp_seq=2. time=0. ms Each line of output here represents a response that was returned from the device that was pinged. This means that the device responded. You continue to get this response indefinitely and have to type ^c (control c) to terminate the ping. If no output is produced, as shown below, then no response occurred and you may have a problem between your system and the device to which you are checking the connection: $ ping system2 PING router1: 64 byte packets In this scenario, you would see this message and that is as far as you would get. A ^c will kill the ping, and you see that some number of packets were sent and none were received. I did indeed get this response when issuing the ping command, so I know that a problem exists with the connection between system1 and router1. ping should be used only for testing purposes such as manual fault isolation, because it generates a substantial amount of network traffic. You do not want to use ping on an ongoing basis, such as in a script that is running continuously. A nice variation of ping that I use is to specify a packet size of 4096 bytes, rather than the default of 64 bytes shown in the previous examples, and count the number of times ping transmits before terminating, rather than having to type ^c to terminate ping. The following example shows this: $ ping router1 4096 5 PING router1: 64 byte packets 4096 bytes from 128.185.51.2: icmp_seq=0. time=8. ms 4096 bytes from 128.185.51.2: icmp_seq=1. time=8. ms 4096 bytes from 128.185.51.2: icmp_seq=2. time=9. ms 4096 bytes from 128.185.51.2: icmp_seq=3. time=8. ms 4096 bytes from 128.185.51.2: icmp_seq=4. time=8. ms Notice that the time required to transmit and receive a response, the round-trip time, is substantially longer than with only 64 bytes transmitted. I usually find that the round-trip time for 64 bytes is 0 ms, although this depends on a number of factors, including network topology and network traffic. netstat From the earlier description of the subnet mask, you can see that routing from one host to another can be configured in a variety of ways. The path that information takes in getting from one host to another depends on routing. You can obtain information related to routing with the netstat command. The -r option to netstat shows the routing tables, which you usually want to know, and the -n option can be used to print network addresses as numbers rather than as names. With the -v option, you get additional information related to routing, such as the subnet mask. In the following examples, netstat is issued with the -r option (this is used when describing the netstat output), the -rn options, and the -rnv options, so you can compare the outputs: # netstat -r Routing tables Dest/Netmask Gateway Flags Refs Use Interface Pmtu o2 o2 UH 0 1890905 lo0 4136 o2 o2 UH 0 343 lan1 4136 o2 o2 UH 0 0 lan0 4136 10.1.1.0 o2 U 2 0 lan0 1500 10.1.1.0 o2 U 2 0 lan1 1500 127.0.0.0 o2 U 0 0 lo0 4136 default 10.1.1.1 UG 0 0 lan1 1500 # # netstat -rn Routing tables Dest/Netmask Gateway Flags Refs Use Interface Pmtu 127.0.0.1 127.0.0.1 UH 0 1891016 lo0 4136 10.1.1.10 10.1.1.10 UH 0 343 lan1 4136 10.1.1.110 10.1.1.110 UH 0 0 lan0 4136 10.1.1.0 10.1.1.110 U 2 0 lan0 1500 10.1.1.0 10.1.1.10 U 2 0 lan1 1500 127.0.0.0 127.0.0.1 U 0 0 lo0 4136 default 10.1.1.1 UG 0 0 lan1 1500 # # netstat -rnv Routing tables Dest/Netmask Gateway Flags Refs Use Interface Pmtu 127.0.0.1/255.255.255.255 127.0.0.1 UH 0 1891036 lo0 4136 10.1.1.10/255.255.255.255 10.1.1.10 UH 0 343 lan1 4136 10.1.1.110/255.255.255.255 10.1.1.110 UH 0 0 lan0 4136 10.1.1.0/255.255.255.0 10.1.1.110 U 2 0 lan0 1500 10.1.1.0/255.255.255.0 10.1.1.10 U 2 0 lan1 1500 127.0.0.0/255.0.0.0 127.0.0.1 U 0 0 lo0 4136 default/0.0.0.0 10.1.1.1 UG 0 0 lan1 1500 # The first and second outputs show that our system, o2, has three interfaces: The first is the loopback interface called lo0. The second. is at .10, and the third is at .110 (which we can see from the -rn output). The next two lines show that our destination of 10.1.1.0, which is a network, can be accessed through either the card at .10 or .110. The third output provides verbose information. The last line is for the default route. This entry says to send packets to 10.1.1.1 if a more direct route can't be found. With netstat, some information is provided about the router. The -r option shows information about routing, but many other useful options to this command are also available. Of particular interest in this output is "Flags," which defines the type of routing that takes place. Here are descriptions of the most common flags from the UNIX manual pages: | 1=U | Route to a network via a gateway that is the local host itself. | | 3=UG | Route to a network via a gateway that is the remote host. | | 5=UH | Route to a host via a gateway that is the local host itself. | | 7=UGH | Route to a host via a remote gateway that is a host. |
Also, I use two forms of netstat to obtain network statistics, as opposed to routing information. The first is netstat -i, which shows the state of interfaces that are autoconfigured. Because I am most often interested in getting a summary of lan0, I issue this command. netstat -i gives a good rundown of lan0, such as the network it is on, its name, and so on. The following example shows the output of netstat -i on a Solaris and HP-UX system, respectively: # netstat -i Name Mtu Network Address Ipkts Ierrs Opkts Oerrs Coll ni0* 0 none none 0 0 0 0 0 ni1* 0 none none 0 0 0 0 0 lo0 4608 loopback 127.0.0.1 232 0 232 0 0 lan0 1500 169.200.112 169.200.112.2 3589746 2 45630 0 104 # netstat -i Name Mtu Network Address Ipkts Opkts lan1 1500 10.1.1.0 o2 59935480 163641547 lan0 1500 10.1.1.0 o2 139173 12839358 lo0 4136 127.0.0.0 o2 1892333 1892345 # Here is a description of the fields in the netstat example: | Name | The name of your network interface (Name), in this case, lan0. | | MTU | The "maximum transmission unit," which is the maximum packet size sent by the interface card. | | Network | The network address of the LAN to which the interface card is connected (169.200). | | Address | The host name of your system. This is the symbolic name of your system as it appears in the file /etc/hosts. |
The statistical information includes: | Ipkts | The number of packets received by the interface card, in this case lan0. | | Ierrs | The number of errors detected on incoming packets by the interface card (on some UNIX variants). | | Opkts | The number of packets transmitted by the interface card. | | Oerrs | The number of errors detected during the transmission of packets by the interface card (on some UNIX variants.) | | Collis | The number of collisions that resulted from packet traffic (on some UNIX variants.) |
netstat provides cumulative data since the node was last powered up; you might have a long elapsed time over which data was accumulated. If you are interested in seeing useful statistical information, you can use netstat with different options. You can also specify an interval over which to report statistics. I usually ignore the first entry, because it shows all data since the system was last powered up. Therefore, the data includes non-prime hours when the system was idle. I prefer to view data at the time the system is working its hardest. The following netstat example provides network interface information every five seconds on a Solaris system: # netstat -I lan0 5 (lan0)-> input output (Total)-> input output packets errs packets errs colls packets errs packets errs colls 3590505 2 45714 0 104 3590737 2 45946 0 104 134 0 5 0 0 134 0 5 0 0 174 0 0 0 0 174 0 0 0 0 210 0 13 0 0 210 0 13 0 0 165 0 0 0 0 165 0 0 0 0 169 0 0 0 0 169 0 0 0 0 193 0 0 0 0 193 0 0 0 0 261 0 7 0 0 261 0 7 0 0 142 0 8 0 0 142 0 8 0 0 118 0 0 0 0 118 0 0 0 0 143 0 0 0 0 143 0 0 0 0 149 0 0 0 0 149 0 0 0 0 With this example, you get multiple outputs of what is taking place on the LAN interface. As I mentioned earlier, you may want to ignore the first output, because it includes information over a long time period. This may include a time when your network was idle, and therefore the data is not important to you. The following netstat example provides network interface information every five seconds on an HP-UX 11i system: # netstat -I lan0 5 (lan0)-> input output (Total)-> input output packets packets packets packets 139185 12841621 61968131 178375605 139185 12841714 61968172 178375698 139185 12841810 61968213 178375794 139185 12841877 61968247 178375861 139185 12841912 61968265 178375896 139185 12842095 61968358 178376079 139187 12842244 61968413 178376240 139189 12842352 61968470 178376360 139189 12842453 61968525 178376461 139190 12842482 61968565 178376498 139190 12842539 61968594 178376555 139190 12842671 61968667 178376699 You can specify the network interface on which you want statistics reported by using -I interface; in the case of the example, it was -I lan0. An interval of five seconds was also used in this example. Yet another use of netstat is to show the state of network sockets. netstat -a produces a list of protocols, queues, local and remote addresses, and protocol states. All this information is useful for showing active communications, as shown in the following example: # netstat -a Active Internet connections (including servers) Proto Recv-Q Send-Q Local Address Foreign Address (state) tcp 0 2 system1.telnet atlm0081.atl.hp..1319 ESTABLISHED tcp 0 0 *.1095 *.* LISTEN tcp 0 0 *.psmond *.* LISTEN tcp 0 0 *.mcsemon *.* LISTEN tcp 0 0 localhost.8886 localhost.1062 ESTABLISHED tcp 0 0 localhost.1062 localhost.8886 ESTABLISHED tcp 0 0 *.8886 *.* LISTEN tcp 0 0 *.8887 *.* LISTEN tcp 0 0 *.1006 *.* LISTEN tcp 0 0 *.978 *.* LISTEN tcp 0 0 *.22370 *.* LISTEN tcp 0 0 *.389 *.* LISTEN tcp 0 0 *.8181 *.* LISTEN tcp 0 0 *.1054 *.* LISTEN tcp 0 0 *.1053 *.* LISTEN tcp 0 0 *.diagmond *.* LISTEN tcp 0 0 *.1045 *.* LISTEN tcp 0 0 *.1038 *.* LISTEN tcp 0 0 *.135 *.* LISTEN tcp 0 0 *.smtp *.* LISTEN tcp 0 0 *.1036 *.* LISTEN tcp 0 0 *.appconn *.* LISTEN tcp 0 0 *.spc *.* LISTEN tcp 0 0 *.dtspc *.* LISTEN tcp 0 0 *.recserv *.* LISTEN tcp 0 0 *.klogin *.* LISTEN tcp 0 0 *.kshell *.* LISTEN tcp 0 0 *.chargen *.* LISTEN tcp 0 0 *.discard *.* LISTEN tcp 0 0 *.echo *.* LISTEN tcp 0 0 *.time *.* LISTEN tcp 0 0 *.daytime *.* LISTEN tcp 0 0 *.printer *.* LISTEN tcp 0 0 *.auth *.* LISTEN tcp 0 0 *.exec *.* LISTEN tcp 0 0 *.shell *.* LISTEN tcp 0 0 *.login *.* LISTEN tcp 0 0 *.telnet *.* LISTEN tcp 0 0 *.ftp *.* LISTEN tcp 0 0 *.795 *.* LISTEN tcp 0 0 *.792 *.* LISTEN tcp 0 0 *.* *.* CLOSED tcp 0 0 *.787 *.* LISTEN tcp 0 0 *.783 *.* LISTEN tcp 0 0 *.779 *.* LISTEN tcp 0 0 *.portmap *.* LISTEN tcp 0 0 *.2121 *.* LISTEN udp 0 0 *.1127 *.* udp 0 0 *.177 *.* udp 0 0 *.1003 *.* udp 0 0 *.* *.* udp 0 0 *.* *.* udp 0 0 *.* *.* udp 0 0 *.* *.* udp 0 0 *.nfsd *.* udp 0 0 *.976 *.* udp 0 0 *.22370 *.* udp 0 0 *.1097 *.* udp 0 0 *.1095 *.* udp 0 0 *.1079 *.* udp 0 0 *.135 *.* udp 0 0 *.* *.* udp 0 0 *.1045 *.* udp 0 0 *.snmp *.* udp 0 0 *.1040 *.* udp 0 0 *.tftp *.* udp 0 0 *.chargen *.* udp 0 0 *.discard *.* udp 0 0 *.echo *.* udp 0 0 *.time *.* udp 0 0 *.daytime *.* udp 0 0 *.ntalk *.* udp 0 0 *.bootps *.* udp 0 0 *.1023 *.* udp 0 0 *.787 *.* udp 0 0 *.798 *.* udp 0 0 *.797 *.* udp 0 0 *.1037 *.* udp 0 0 *.* *.* udp 0 0 *.1036 *.* udp 0 0 *.1035 *.* udp 0 0 *.777 *.* udp 0 0 *.portmap *.* udp 0 0 *.1034 *.* udp 0 0 *.syslog *.* udp 0 0 *.2121 *.* Active UNIX domain sockets Address Type Recv-Q Send-Q Inode Conn Refs Nextref Addr bb9c00 stream 0 0 af9000 0 0 0 /tmp/.AgentSoA ced700 dgram 0 0 c99400 0 0 0 /opt/dcelocalr ce9e00 dgram 0 0 d23000 0 0 0 /opt/dcelocalr b0d200 dgram 0 0 b87000 0 0 0 /opt/dcelocalr 997a00 stream 0 0 b84800 0 0 0 /opt/dcelocal1 b24e00 dgram 0 0 b84000 0 0 0 /opt/dcelocal1 d59400 dgram 0 0 b66400 0 0 0 /var/tmp/psb_t d85c00 dgram 0 0 b67000 0 0 0 /var/tmp/psb_t c8b200 dgram 0 0 b12000 0 0 0 /opt/dcelocalr c8b400 stream 0 0 b78400 0 0 0 /opt/dcelocal5 c8b300 dgram 0 0 b78000 0 0 0 /opt/dcelocal5 c90900 dgram 0 0 d22400 0 0 0 /opt/dcelocalr c78c00 dgram 0 0 ba1000 c4a180 0 0 /opt/dcelocal0 b1e900 dgram 0 0 9a4400 0 c32e80 0 /opt/dcelocald d64100 stream 0 0 d24c00 0 0 0 /opt/dcelocal5 9e1600 dgram 0 0 9a4000 d4d940 0 0 /opt/dcelocal2 d64200 dgram 0 0 cfc800 0 c32c80 0 /opt/dcelocal9 d12d00 dgram 0 0 cfc000 c32c00 0 0 /opt/dcelocal1 c5ee00 stream 0 0 b1c000 0 0 0 /opt/dcelocal4 d19d00 dgram 0 0 ce4800 0 0 0 /opt/dcelocald cf0c00 dgram 0 0 a92800 0 af15c0 0 /opt/dcelocal7 d2d600 dgram 0 0 a93800 c32c00 0 d4db80 /opt/dcelocal0 c9b900 dgram 0 0 a93c00 0 0 0 /opt/dcelocald d6c800 stream 0 0 ba3000 0 0 0 /var/opt/OV/sT # A lot of information is in this output. You can refer to the online manual pages on your HP-UX system. The first line shows the Proto tcp to the Local Address system1.telnet as having a (state) of ESTABLISHED. This is the connection we have initiated to this system. We are sitting on system1 with a telnet session open to the system on which we ran netstat. Most of the remaining tcp protocol entries are listening. This means that they are listening for incoming connections, as indicated by the LISTEN. They have a wildcard in the Foreign Address field, which will contain the address when a connection has been established. We are one of the few connections that has been made, as indicated by the ESTABLISHED. All the send and receive queues, shown as Recv-Q and Send-Q, are empty as indicated by 0. The UNIX domain sockets at the end of the output are stream and datagram connections for a variety of services such as NFS. This output gives you an appreciation of the immense amount of activity taking place from a networking perspective on your UNIX system. Networking and connectivity have been among the most advanced aspects of UNIX since its inception. route The information displayed with netstat is the routing tables for your system. Some are automatically created with the ifconfig command when your system is booted or when the network interface is initialized. Routes to networks and hosts that are not directly connected to your system are entered with the route command. Routing changes can be made on the fly, as I did to change the Flags from U to UG: $ /usr/sbin/route add default 128.185.61.1 3 First is the route command. Second, we specify that we wish to add a route; the other option is to delete a route. Third, we specify the destination, in this case, the default. This could be a specific host name, a network name, an IP address, or default that signifies the wildcard gateway route that is shown in our example. Fourth is the gateway through which the destination is reached. In the above example, the IP address was used, but this could also be a host name. The 3 corresponds to the count that is used to specify whether the gateway is the local host or a remote gateway. If the gateway is the local host, then a count of 0 is used. If the gateway is a remote host, which is the case in the example, a count of >0 is used. This corresponds to UG for Flags. This manually changed the network routing table by adding a default route with the appropriate Flags. Issuing this command fixed the problem I encountered trying to get system1 to talk to the systems on the other side of the router (remember Figure 13-11). Before issuing /usr/sbin/route with the add option, you can first use the delete option to remove the existing default route, which is not working. route commands usually appear in one of the system's startup files so that every time the system boots, route commands are issued. This ensures that the right connectivity information is in place every time the system starts. ifconfig The ifconfig command provides additional information on a LAN interface. The following example provides the configuration of a network interface: $ /etc/ifconfig lan0 lan0: flags=863<UP,BROADCAST,NOTRAILERS,RUNNING> inet 128.185.61.2 netmask ffff0000 broadcast 128.185.61.255 From this example, we can quickly see that the interface is up, it has an address of 128.185.61.2, and it has a netmask of ffff0000. A gain, keep in mind that your network interface may have a different name, such as le0. You can use ifconfig to get the status of a network interface as I have done here to assign an address to a network interface, or to configure network interface parameters. The network address you have falls into classes such as "A," "B," or "C," as mentioned earlier. You want to be sure that you know the class of your network before you start configuring your LAN interface. This example is a class "B" network, so the netmask is defined as ffff0000 (typical for a class "B" address), as opposed to ffffff00, which is typical for a class "C" network. The netmask is used to determine how much of the address to reserve for subdividing the network into smaller networks. The netmask can be represented in hex, as shown above, or in decimal for-mat, as in the /etc/hosts file. Here is the ifconfig command I issued to configure the interface: $ /etc/ifconfig lan0 inet 128.185.61.2 netmask 255.255.0.0 The 255.255.0.0 corresponds to the hex ffff000 shown earlier for the class "B" subnet mask. lan0 is the interface being configured. inet is the address family, which is currently the only one supported for this system. 128.185.61.2 is the address of the LAN interface for system1. netmask shows how to subdivide the network. 255.255.0.0 is the same as ffff0000, which is the netmask for a class "B" address.
I have made good use of netstat, ping, and ifconfig to help get the status of the network. ifconfig, route, and /etc/hosts are used to configure the network, should you identify any changes you need to make. The subnet examples show how flexible you can be when configuring your network for both your current and future needs. In simple networks, you may not need to use many of these commands or complex subnetting. In complex networks, or at times when you encounter configuration difficulties, you may have to make extensive use of these commands. In either case, network planning is an important part of setting up UNIX systems. Most of the commands used throughout this chapter are a part of every system administrator's tool box. Networking is so vital to the use of UNIX systems, however, that having background in this area can help with your overall understanding of the system and how to use it more effectively. rpcinfo As a user, you may have a need to NFS mount a directory on another system or perform some other function that you haven't before used on your system. You can determine whether various pieces of functionality have been enabled by evaluating the daemons running on your system. rpcinfo allows you to generate a Remote Procedure Call (RPC) on a system, including your local system, by issuing the command rpc -p system_name. The following example shows issuing rpcinfo -p on our local system: # rpcinfo -p program vers proto port service 100000 2 tcp 111 portmapper 100000 2 udp 111 portmapper 100024 1 udp 777 status 100024 1 tcp 779 status 100021 1 tcp 783 nlockmgr 100021 1 udp 1035 nlockmgr 100021 3 tcp 787 nlockmgr 100021 3 udp 1036 nlockmgr 100020 1 udp 1037 llockmgr 100020 1 tcp 792 llockmgr 100021 2 tcp 795 nlockmgr 100068 2 udp 1040 cmsd 100068 3 udp 1040 cmsd 100068 4 udp 1040 cmsd 100068 5 udp 1040 cmsd 100083 1 tcp 1036 ttdbserver 100005 1 udp 976 mountd 100005 1 tcp 978 mountd 100003 2 udp 2049 nfs 150001 1 udp 1003 pcnfsd 150001 2 udp 1003 pcnfsd 150001 1 tcp 1006 pcnfsd 150001 2 tcp 1006 pcnfsd # Many daemons are running on the system that are important to the functionality I like to use. mountd is running, which indicates that a server could NFS mount file systems on this computer. There is other setup required for the mount to take place, but at least the daemon is running to support this functionality. In addition, pcnfsd is running, meaning that we have support for Windows-based NFS access. arp The mechanism used to maintain a list of IP addresses and their corresponding MAC addresses is the ARP cache. The mapped addresses are only held in the cache for minutes, so if you want to see what addresses have been mapped recently, you can use the arp command as shown in the following example: # arp -a o2 (10.1.1.10) at 0:10:83:f7:a2:f8 ether l1 (10.1.1.11) at 0:10:83:f7:2e:d0 ether 63.88.85.1 (63.88.85.1) at 0:30:94:b0:b8:a0 ether l3 (10.1.1.200) at 0:10:83:fc:92:88 ether tape1 (10.1.1.14) at 0:10:83:f7:e:32 ether tape1 (10.1.1.14) at 0:10:83:f7:e:32 ether tape1 (10.1.1.14) at 0:10:83:f7:e:32 ether tape1 (10.1.1.14) at 0:10:83:f7:e:32 ether 63.88.85.18 (63.88.85.18) -- no entry Current arp entries are displayed with the -a command. You can create an entry with the -s option. lanadmin lanadmin is used to view and perform administration on network cards. Issuing lanadmin with no options brings you into the interactive interface as shown in the following example: # lanadmin LOCAL AREA NETWORK ONLINE ADMINISTRATION, Version 1.0 Copyright 1994 Hewlett Packard Company. All rights are reserved. Test Selection mode. lan = LAN Interface Administration menu = Display this menu quit = Terminate the Administration terse = Do not display command menu verbose = Display command menu Enter command: lan LAN Interface test mode. LAN Interface PPA Number = 0 clear = Clear statistics registers display = Display LAN Interface status and statistics registers end = End LAN Interface Administration, return to Test Selection menu = Display this menu ppa = PPA Number of the LAN Interface quit = Terminate the Administration, return to shell reset = Reset LAN Interface to execute its selftest specific = Go to Driver specific menu Enter command: d LAN INTERFACE STATUS DISPLAY PPA Number = 0 Description = lan0 Hewlett-Packard 10/100 TX Half-Duplex TT = 1500 Type (value) = ethernet-csmacd(6) MTU Size = 1500 Speed = 100000000 Station Address = 0x1083ffcaae Administration Status (value) = up(1) Operation Status (value) = down(2) Last Change = 237321866 Inbound Octets = 0 Inbound Unicast Packets = 0 Inbound Non-Unicast Packets = 0 Inbound Discards = 0 Inbound Errors = 0 Inbound Unknown Protocols = 0 Outbound Octets = 820 Outbound Unicast Packets = 20 Outbound Non-Unicast Packets = 0 Outbound Discards = 1 Outbound Errors = 0 Outbound Queue Length = 0 Specific = 655367 Press <Return> to continue In this example, we issued lanadmin and specified that we wanted to go into the lan interface administration and that we wanted to display information about the interface. lanadmin can also be used to perform such tasks as to change the MTU or speed of a lan interface with the -M and -s options, respectively. ndd ndd is used to perform network tuning and view information about network parameters. To view information about all supported tunable parameters with ndd, you would issue ndd -h supported. You can get the value of a parameter using the -get option you can set the value of a parameter with the -set option. nslookup nslookup is used to resolve a host name into an IP address. You issue nslookup hostname and nslookup will access either the /etc/resolv.conf file or /etc/hosts to resolve the host name. The following example shows a system using /etc/hosts to produce the IP address of system l2: # nslookup l2 Using /etc/hosts on: l3 looking up FILES Name: l2 Address: 10.1.1.12 # You can also run nslookup in interactive mode by issuing the command with no command-line arguments. The following example shows issuing the command with no command line arguments to get into interactive mode and then typing help to get information on commands you can issue: # nslookup l2 > help NAME - print address information about NAME IP-ADDRESS - print hostname information about IP-ADDRESS policy - print switch policy information server NAME - set default server to NAME, using current de- fault server lserver NAME - set default server to NAME, using initial serv- er set OPTION - sets the OPTION all - print options, current server and host [no]swtrace - print lookup result and lookup switch messages > |