Internet Protocol (IP) Addressing and Subnet Mask
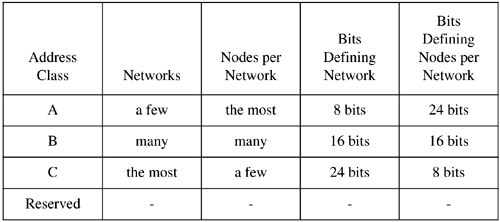
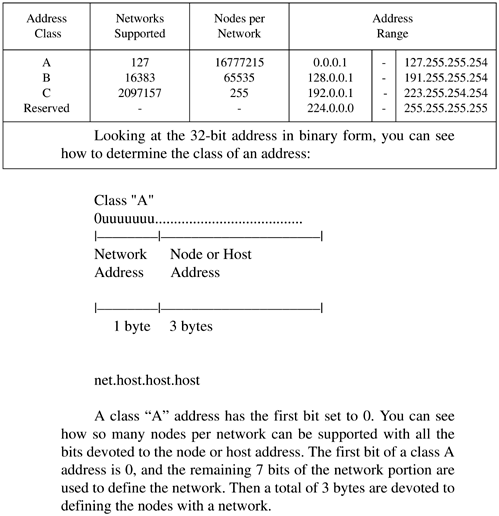
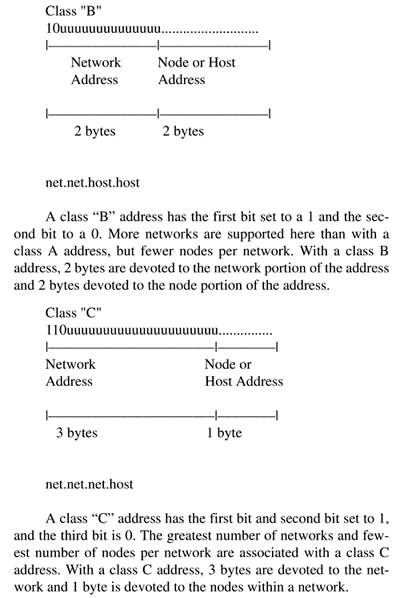
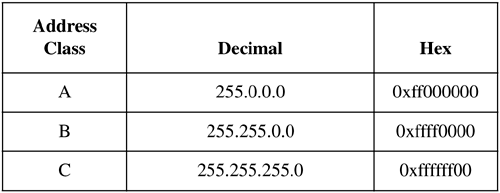
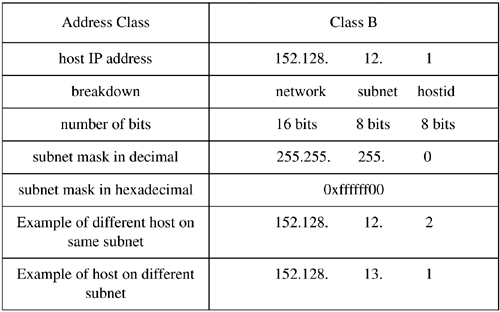
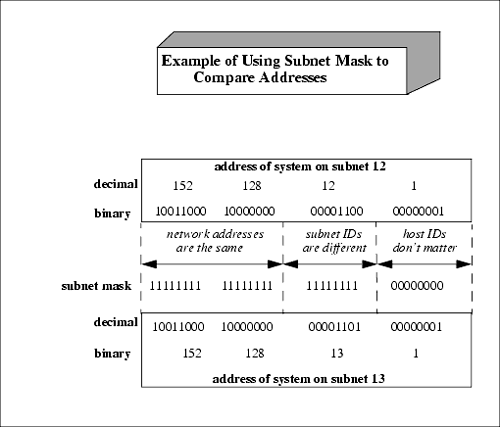
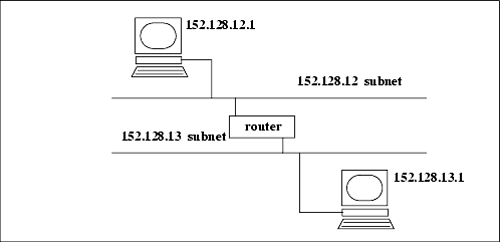
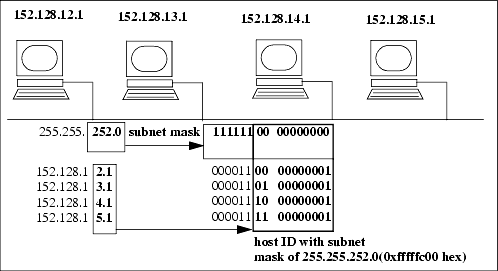
| The Internet Protocol address (IP address) is either a class "A," "B," or "C" address (there are also class "D" and "E" addresses I will not cover). A class "A" network supports many more nodes per network than either a class "B" or "C" network. IP addresses consist of four fields. The purpose of breaking down the IP address into four fields is to define a node (or host) address and a network address. Figure 12-3 summarizes the relationships between the classes and addresses. Figure 12-3. Comparison of Internet Protocol (IP) Addresses These bit patterns are significant in that the number of bits defines the ranges of networks and nodes in each class. For instance, a class A address uses 8 bits to define networks, and a class C address uses 24 bits to define networks. A class A address therefore supports fewer networks than a class C address. A class A address, however, supports many more nodes per network than a class C address. Taking these relationships one step further, we can now view the specific parameters associated with these address classes in Figure 12-4. Figure 12-4. Address Classes These addresses are used in various setup files that are covered later when the /etc/ hosts file is described. Every interface on your network must have a unique IP address. Systems that have two network interfaces must have two unique IP addresses. Subnet MaskYour UNIX system uses the subnet mask to determine whether an IP datagram is for a host on its own subnet, a host on a different subnet but the same network, or a host on a different network. Using subnets, you can have some hosts on one subnet and other hosts on a different subnet. The subnets can be separated by routers or other networking electronics that connect the subnets. To perform routing, the only aspects of an address that your router uses are the net and subnet. The subnet mask is used to mask the host part of the address. Because you can set up network addresses in such a way that you are the only one who knows which part of the address is the host, subnet, and network, you use the subnet mask to make your system aware of the bits of your IP address that are for the host and which are for the subnet. In its simplest form, what you are really doing with subnet masking is specifying which portion of your IP address defines the host, and which part defines the network. One of the most confusing aspects of working with subnet masks is that most books show the subnet masks in Figure 12-5 as the most common. Figure 12-5. Subnet Masks This way of thinking, however, assumes that you are devoting as many bits as possible to the network and as many bits as possible to the host, and that no subnets are used. Figure 12-6 shows an example of using subnetting with a class B address. Figure 12-6. Class B IP Address and Subnet Mask Example In Figure 12-6, the first two bytes of the subnet mask (255.255) define the network, the third byte (255) defines the subnet, and the fourth byte (0) is devoted to the host ID. Although this subnet mask for a class B address did not appear in the earlier default subnet mask figure, the subnet mask of 255.255.255.0 is widely used in class B networks to support subnetting. How does your UNIX system perform the comparison using the subnet mask of 255.255.255.0 to determine that 152.128.12.1 and 152.128.13.1 are on different subnets? Figure 12-7 shows this comparison. Figure 12-7. Example of Using Subnet Mask to Compare Addresses Figure 12-8 shows these two systems on the different subnets: Figure 12-8. Class B Systems on Different Subnets You don't have to use the 8-bit boundaries to delineate the network, subnet, and host ID fields. If, for instance, you want to use part of the subnet field for the host ID, you can do so. A good reason for this approach would be to accommodate future expandability. You might want subnets 12, 13, 14, and 15 to be part of the same subnet today and make these into separate subnets in the future. Figure 12-9 shows this setup: Figure 12-9. Future Expandability Using Subnet Mask These systems are connected to the same subnet, even though part of the third byte, normally associated with the subnet, is used for the host ID. In the future, the subnet mask could be changed to 255.255.252.0 and have four separate subnets of 12, 13, 14, and 15. This arrangement would require putting routers in place to route to these separate subnets. Chapter 13 covers configuring and using UNIX networking. |
EAN: 2147483647
Pages: 301
- Seeing Services Through Your Customers Eyes-Becoming a customer-centered organization
- Success Story #3 Fort Wayne, Indiana From 0 to 60 in nothing flat
- Success Story #4 Stanford Hospital and Clinics At the forefront of the quality revolution
- Service Process Challenges
- Designing World-Class Services (Design for Lean Six Sigma)