Chapter 7. J2SE Security Fundamentals
| < Day Day Up > |
| Java technology is not just for applets any more. Developers now use Java technology to build stand-alone, enterprise-class applications to enable disparate clients , such as workstations, personal computers, Java-based network computers, mobile telephones, and personal digital assistants, to access legacy databases and share applications across the network. The J2EE security architecture builds on the basic characteristics of J2SE security. It is therefore helpful to understand J2SE security before studying the advanced features J2EE offers. This chapter describes the basic J2SE security model and introduces all the main concepts related to Java security. Chapter 8 discusses the Java 2 permission model, and Chapter 9 focuses on how Java Authentication and Authorization Service (JAAS) augments the basic permission model by providing user authentication and authorization. Readers who are already experienced with the basic J2SE security model can quickly glance through this part of the book or even skip it entirely. However, readers who do not have a solid background on J2SE security will find that this material will help them understand J2EE security. The J2SE security model has evolved and matured over the years and has become very complex and articulated . We begin this chapter by discussing access restrictions to classes, interfaces, methods , and fields. We then cover the three legs of Java security, which are three fundamental security components of the Java Runtime Environment:
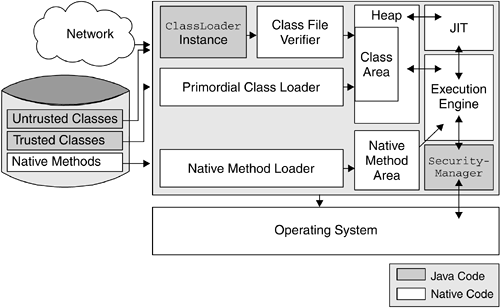
Figure 7.1 shows a simplified view of the JVM, from which we can see where the three security legs fit in the architecture of the JVM. Figure 7.1. JVM Components This chapter is useful for anyone who wants to understand the foundation of Java security. J2EE product providers in particular will find this chapter helpful in understanding how they can customize class loaders and SecurityManager to achieve a more sophisticated control on the security implementation of their J2EE products. |
| < Day Day Up > |
EAN: 2147483647
Pages: 164