3.6 Simple E-Business Request Flow
| < Day Day Up > |
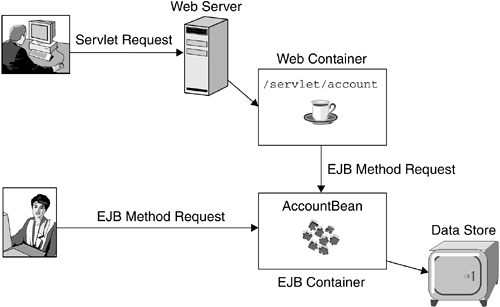
| It would be helpful to understand a simple e-business request flow in an enterprise Java environment. Figure 3.3 presents a simple request flow that does not involve security. Figure 3.3. Simple E-Business Request Flow Let us consider two types of clients : HTTP clients , such as Web browsers, and IIOP clients , regular applications capable of using IIOP to send requests and receive responses over the network. An HTTP client invokes a URL: for instance, /servlet/account/ . The request from the user 's browser gets handled by the Web server, which routes the request to a Web, or servlet, container serving the URL resource. The logic behind the URL is implemented as a Java servlet. This servlet, packaged in a Web module, is hosted in a J2EE Web container, which in turn invokes an enterprise bean, AccountBean, via IIOP. AccountBean is an entity bean, packaged in an EJB module, with its business data stored in a data store. The same enterprise bean is accessed directly from an IIOP client, packaged in an application client module. In this case, the request is not routed by the servlet but is directly accessed as a remote object from the Java client. The request flow just described does not involve security considerations. The next sections in this chapter provide an overview of the J2EE specification as it pertains the security of an enterprise. The platform roles reflect the organizational responsibilities, from application development, application assembly, and application deployment, to administration. |
| < Day Day Up > |
EAN: 2147483647
Pages: 164