Acceptance Testing
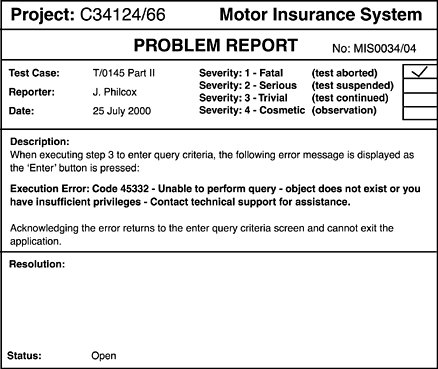
| Acceptance testing is the final phase of testing before going live. It is a crucial process and eventually will determine whether a product is acceptable to the business. When a product is deemed to be acceptable, it progresses through to implementation and becomes operational, but what happens if either the user acceptance or the system acceptance tests fail? During acceptance testing, problem logs are created when either a bug is found or the application responds in an unexpected manner. The logs are passed to the developer(s) for resolution. An example of a problem log is shown in Figure 4.1. The tester often provides additional information by attaching a screen dump showing clearly the point at which the error occurs. Sometimes the resolution is procedural and may require only a trivial update to the documentation, but on other occasions, a fix may have to be supplied. For the latter, a patch is issued and installed on the system. However, it's not that simple because the fix could invalidate all the testing already done. Figure 4.1. The problem log represents a formal document of the testing phase with a unique reference. It is often stored in a database using a program such as PVCS Tracker, allowing further analysis to be undertaken. Consider the following example: While testing the application, a user receives the wrong results for a query operation. A problem log is raised and passed to the developers to fix. A patch is delivered containing the fixed module. The query module is shared by several forms and is also used to gather the information for the management and financial reports . Clearly, in this example, the impact of the change is much wider than just the query being tested . The point is that any changes to a system or application under review must include a detailed impact assessment so that its effect is known and understood . In the example, the change is fundamental to the system and may require the testing to be restarted from the beginning. In reality, testing would probably be completed (without installing the patch) so that any other problems can be addressed before rerunning the tests. Regression TestingRegression testing is used as a mechanism of ensuring that there have been no unexpected side effects of a change. It allows tests to be rerun, knowing exactly what the result should be, thereby highlighting immediately any deviation. For example, consider an application that calculates the payroll for the employees of the company. Suppose that a new application is being developed to replace the existing one, which cannot handle the increased number of employees since the company expanded. Using the existing system for calculating the payroll, a test would be devised, using specific test data (say, a dozen employees), and their payroll details calculated. When the new system is installed and tested, the same calculations would be carried out, using the same test data. The results should be exactly the same ”if not, then the new system is not functioning correctly. For an application such as payroll, despite the fact that a new way of doing things has been developed, maybe using a new GUI front end, the functionality ”that is, the results of the calculations ”should be the same. Regression testing is used for this purpose, to be able to verify that the application still performs as expected. Without the benefit of regression testing, it would be extremely difficult to identify the effects of any changes on other parts of the application, leaving the potential for problems to be found only after the system is live. System TestingSystem testing involves testing all the features of a new application. The IT department carries out the system acceptance and fully tests the functionality against an agreed criteria, usually the functional specification. System testing differs from user acceptance testing in that the management and configuration of the application or system is tested in addition to the functionality. Some of the types of tests are listed here:
User AcceptanceThe user community must have the opportunity to test the application before implementation. For larger projects, a user assurance coordinator (UAC) should be assigned to the project, normally from within the IT department. As a system manager, I have fulfilled this role. The UAC looks after the users' interests to ensure that the application meets their expectations. UAT should be carried out on a dedicated test environment in which changes to the application cannot be made without being carefully controlled and documented. At this stage of the process, changes are acceptable only when delivered as patches, and these would be as a result of problem logs being created by the UAT team. This stage of testing is crucial to a project being successful for the following reasons:
Recovery Testing Recovery tests can sometimes be extremely difficult to accomplish, particularly with sealed units that can't be accessed directly. Certain tests likely may need the cooperation of the vendor so that the required scenarios can be fully tested.
Performance TestingThe other areas of testing discussed so far verify, as much as possible, that the application functions as expected. Performance testing looks at a further aspect that is sometimes less obvious: the testing of the application when under load, or busy, conditions. Performance testing has become even more important since businesses started using the Internet, particularly with reference to Web servers. There might be a point at which the application, or the server, crashes if too many people try to use it at the same time, so the performance capability must be tested so that the anticipated demand can be met. It is extremely difficult to accurately predict the level of demand that a new Web site will generate ”companies are often victims of their own success. For example, when an advertising campaign has much greater success than predicted , the increase in demand can be more than the system can handle. Producing test conditions and data for performance testing can be a time-consuming and expensive business, requiring a great deal of coordination. It often involves creating large amounts of test data, as well as having the relevant technical staff in attendance to accurately monitor the performance as the testing is carried out. From the system manager's point of view, however, the testing can be of great benefit because it might provide firm justification for upgrading a server that was proved to be inadequate, or the purchase of a new, more powerful machine. |
| Top |
EAN: 2147483647
Pages: 101