Kerberos
|
| < Day Day Up > |
|
User authentication can further be controlled for certain services by Kerberos servers, discussed in this chapter. Kerberos authentication provides another level of security whereby individual services can be protected, allowing use of a service only to users who are cleared for access. Kerberos servers are all enabled and configured with authconfig-gtk (Authentication in the System Settings menu or window).
Kerberos is a network authentication protocol that provides encrypted authentication to connections between a client and a server. As an authentication protocol, Kerberos requires a client to prove its identity using encryption methods before it can access a server. Once authenticated, the client and server can conduct all communications using encryption. Whereas firewalls protect only from outside attacks, Kerberos is designed to also protect from attacks from those inside the network. Users already within a network could try to break into local servers. Kerberos places protection around the servers themselves, rather than an entire network or computer. A free version is available from the Massachusetts Institute of Technology at web.mit.edu/kerberos under the MIT Public License, which is similar to the GNU Public License. The name Kerberos comes from Greek mythology and is the name of the three-headed watchdog for Hades. Be sure to check the web.mit.edu/kerberos site for recent upgrades and detailed documentation, including FAQs, manuals, and tutorials.
| Tip | The Kerberos V5 package includes its own versions of network tools such as Telnet, RCP, FTP, and RSH. These provide secure authenticated access by remote users. The tools operate in the same way as their original counterparts described in Chapter 15. The package also contains a Kerberos version of the su administrative login command, ksu. |
Kerberos Servers
The key to Kerberos is a Kerberos server through which all requests for any server services are channeled. The Kerberos server then authenticates a client, identifying the client and validating the client's right to use a particular server. The server maintains a database of authorized users. Kerberos then issues the client an encrypted ticket that the client can use to gain access to the server. For example, if a user needs to check their mail, a request for use of the mail server is sent to the Kerberos server, which then authenticates the user and issues a ticket that is then used to access the mail server. Without a Kerberos-issued ticket, no one can access any of the servers. Originally, this process required that users undergo a separate authentication procedure for each server they wanted to access. However, users now only need to perform an initial authentication that is valid for all servers.
| Tip | On Red Hat, you can use the Kerberos Ticket Manager (Extras Accessories menu) to manage Kerberos tickets, and the authconfig-gtk tool (Authentication in the System Settings window or menu) to specify and enable Kerberos realms. |
This process actually involves the use of two servers, an authentication server (AS) and a ticket-granting server (TGS). Together they make up what is known as the key distribution center (KDC). In effect, they distribute keys used to unlock access to services. The authentication server first validates a user's identity. The AS issues a ticket called the ticket-granting ticket (TGT) that allows the user to access the ticket-granting server. The TGS then issues the user another ticket to actually access a service. This way, the user never has any direct access of any kind to a server during the authentication process. The process is somewhat more complex than described. An authenticator using information such as the current time, a checksum, and an optional encryption key is sent along with the ticket and is decrypted with the session key. This authenticator is used by a service to verify your identity.
| Note | You can view your list of current tickets with the klist command. |
Authentication Process
The authentication server validates a user using information in its user database. Each user needs to be registered in the authentication server's database. The database will include a user password and other user information. To access the authentication server, the user provides the username and the password. The password is used to generate a user key with which communication between the AS and the user is encrypted. The user will have their own copy of the user key with which to decrypt communications. The authentication process is illustrated in Figure 18-2.
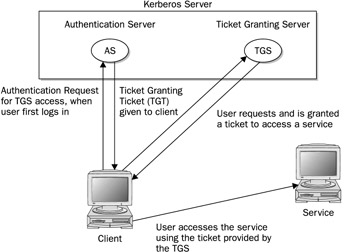
Figure 18-2: Kerberos authentication
Accessing a service with Kerberos involves the following steps:
-
The user has to be validated by the authentication server and granted access to the ticket-granting server with a ticket access key. You do this by issuing the kinit command, which will ask you to enter your Kerberos username and then send it on to the authentication server (the Kerberos username is usually the same as your username).
kinit
-
The AS generates a ticket-granting ticket with which to access the ticket-granting server. This ticket will include a session key that will be used to let you access the TGS. The TGT is sent back to you encrypted with your user key (password).
-
The kinit program then prompts you to enter your Kerberos password, which it then uses to decrypt the TGT. You can manage your Kerberos password with the kpasswd command.
-
Now you can use a client program such as a mail client program to access the mail server, for instance. When you do so, the TGT is used to access the TGS, which then will generate a ticket for accessing the mail server. The TGS will generate a new session key for use with just the mail server. This will be provided in the ticket sent to you for accessing the mail server. In effect, there is a TGT session key used for accessing the TGS, and a mail session key used for accessing the mail server. The ticket for the mail server is sent to you encrypted with the TGS session key.
-
The client then uses the mail ticket received from the TGS to access the mail server.
-
If you want to use another service such as FTP, when your FTP client sends a request to the TGS for a ticket, the TGS will automatically obtain authorization from the authentication server and issue an FTP ticket with an FTP session key. This kind of support remains in effect for a limited period of time, usually several hours, after which you again have to use kinit to undergo the authentication process and access the TGS. You can manually destroy any tickets you have with the kdestroy command.
Note With Kerberos V5 (version 5), a Kerberos login utility is provided whereby users are automatically granted ticket-granting tickets when they log in normally. This avoids the need to use kinit to manually obtain a TGT.
Kerberized Services
Setting up a particular service to use Kerberos (known as Kerberizing) can be a complicated process. A Kerberized service needs to check the user's identity and credentials, check for a ticket for the service, and if one is not present, obtain one. Once they are set up, use of Kerberized services is nearly transparent to the user. Tickets are automatically issued and authentication carried out without any extra effort by the user.
Configuring Kerberos Servers
Installing and configuring a Kerberos server is also a complex process. Carefully check the documentation for installing the current versions. Some of the key areas are listed here. In the Kerberos configuration file, krb5.conf, you can set such features as the encryption method used and the database name. When installing Kerberos, be sure to carefully follow the instructions for providing administrative access. The /etc/services file should contain a listing of all Kerberized services. These are services such as kftp or klogin that provide Kerberos FTP and login services. To run Kerberos, you start the Kerberos server with service command and the krb5kdc, kadmin, and krb524 scripts.
| Tip | Check the Red Hat Linux Reference Manual for more detailed instructions on setting up Kerberos servers and clients on your system. |
Consult the Red Hat Linux Reference Guide for detailed instructions on how to install and configure Kerberos on Red Hat. You will need to configure the server for your network, along with clients for each host. To configure your server, you first specify your Kerberos realm and domain by manually replacing the lowercase example.com and the uppercase EXAMPLE.COM entries in the /etc/krb5.conf and /var/kerberos/krb5kdc/kdc.conf files with your own domain name. Maintain the same case for each entry. Realms are specified in uppercase, and simple host and domain names are in lowercase. You then create a database with the kdb5_util command and the create option. You will be prompted to enter a master key.
kdb5_util create -s
Full administrative access to the server is controlled by user entries in the var/kerberos/krb5kdc/kadm5.acl file. Replace the EXAMPLE.COM text with your Kerberos realm (usually your domain name in uppercase). You then need to add a local principal, a local user with full administrative access from the host the server runs on. Start the kadmin.local tool and use the addprinc command to add the local principal. You can then start your krb5kdc, kadmin, and krb524 servers.
On each client host, use the kadmin tool with the addprincipal command to add a principal for the host. Also add a host principal for each host on your network with host/ qualifier, as in host/rabbit.mytrek.com. You can use the -randkey option to specify a random key. Then save local copies of the host keys, using the ktadd command to save them in its /etc/krb5.keytab file. Each host needs to also have the same /etc/krb5.conf configuration file on its system, specifying the Kerberos server and the kdc host.
| Note | When you configure Kerberos with the Authentication tool, you will be able to enter the realm, kdc server, and Kerberos server. Default entries will be displayed using the domain "example.com." Be sure to specify the realm in uppercase. A new entry for your realm will be made in the realms segment of the /etc/krb5.conf, listing the kdc and server entries you made. |
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 328