Chapter 7. Wireless Attacks
| IN THIS CHAPTER
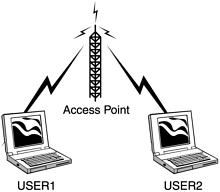
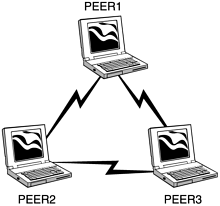
CAUTION Disclaimer: Information presented in this book is to help you protect your own networks only. Consult with your company's counsel, and be sure to get permission in writing from your supervisor, before attempting any of these techniques. This book provides examples of how hackers perform their attacks solely to help you anticipate them and to defend your wireless networks against them. You are responsible for knowing your local and regional laws and for obeying them at all times. The techniques for wireless attacks are not new. Indeed, they are based on the ancient attacks that have been used on wired networks from time immemorial, with only minor updates. In fact, the goal of attacking a wireless network is usually not to compromise the wireless network itself, but rather to gain a foothold into the wired network within. Because traditional wired networks have been hardened from repeated attacks for more than thirty years , many are beginning to evolve formidable defenses. For example, a properly configured firewall can provide much security. However, consider what happens when you have an unsecured wireless access point sitting within the firewall ”you have just effectively opened a back door right through your firewall. Thus, the proliferation of wireless networks has set the state of information security back more than a decade ”almost to the 1980s, when computer systems were wide open to attack via modems and war dialing. In time, most wireless networks will fall victim to at least one type of wireless attack. These attacks are not limited to just the corporate world, either. One of the largest consumers of wireless networks is the residential customer. These consumers are typically looking for a way to use their broadband connection in any room of the house. Worse, the vast majority of consumers are not aware of security issues. You can now buy access points from the local electronic store for less than $200, but many of these do not have the same security features of the corporate or professional models that run $800 and up. With more users installing these low-end access points, both on personal networks and within small businesses, the number of easy targets is growing exponentially. There are many different models of 802.11b Wireless Network Interface Cards (WNICs). One thing common to all is the capability to put them into Infrastructure and peer-to-peer mode. The IEEE defines Infrastructure mode utilizing a Basic Service Set (BSS; that is, an access point. In this case, it is used to connect a client to an access point on an established network (Figure 7.1). Peer-to-peer mode, also known as ad-hoc mode, is known as Independent Basic Service Set (IBSS). This mode is used to connect two or more wireless devices to form a small close range network, much like peer-to-peer networking on wired networks (Figure 7.2). Figure 7.1. Common Infrastructure mode setup. Figure 7.2. Common peer-to-peer/ad-hoc mode setup. One of the major disadvantages of this type of wireless network is that there is no central security control; in fact, there is very little security at all. The most difficult part of launching an attack on this type of network is finding one to attack. Since they are informally deployed, they can pop up and disappear overnight. Examples of such networks can be found at conventions and coffee shops , as well as any situation that requires Internet connection sharing (that is, splitting a single Internet connection among several users). |
EAN: 2147483647
Pages: 171