5.1 Buffer Overflows
| < Day Day Up > |
| To exploit an overflow, you need a thorough knowledge of assembly language, C++, and the operating system you wish to attack. This chapter describes buffer overflows, traces their evolution, and even walks you through a live sample. A buffer overflow attack deliberately enters more data than a program was written to handle. The extra data overflows the region of memory set aside to accept it, thus overwriting another region of memory that was meant to hold some of the program's instructions. In the ideal version of this attack, the overflow values introduced become new instructions that give the attacker control of the target processor. Buffer overflow attacks are not a new phenomenon . For example, the original Morris worm in 1988 used a buffer overflow. In fact, the issue of buffer overflow risks to computer systems has been recognized since the 1960s. 5.1.1 A Sample OverflowBuffer overflows result from an inherent weakness in the C++ programming language. The problem (which is inherited from C and likewise found in other languages, such as Fortran) is that C++ does not automatically perform bounds-checking when passing data. To understand this concept, consider the following sample code that illustrates how a C/C++ function returns data to the main program: // lunch.cpp : Overflowing the stomach buffer #include <stdafx.h> #include <stdio.h> #include <string.h> void bigmac(char *p); int main(int argc, char *argv[]) { bigmac("Could you supersize that please?"); // size > 9 overflows return 0; } void bigmac(char *p) { char stomach[10]; //limit the size to 10 strcpy(stomach, p); printf(stomach); } To test this program, you compile it using a C++ compiler. Although the program compiles without errors, when we execute it we get a program crash similar to Figure 5-1. Figure 5-1. Buffer overflow crash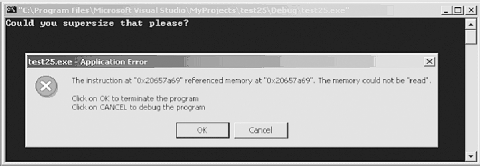 What happened ? When this program executes, it calls the function bigmac and passes it the long string "Could you supersize that please?" Unfortunately, strcpy( ) never checks the string's length. This is dangerous, because in this case passing a string longer than nine characters generates a buffer overflow. Like several other C++ functions, strcpy( ) is inherently weak, in that it will write the extra characters past the variable end. This usually results in a program crash. In this particular case, the crash was an error in reading past the end of the statically allocated string. In a worst-case scenario, such an overflow might allow you to execute arbitrary code on the target system, as discussed later in this chapter. |
| < Day Day Up > |
EAN: 2147483647
Pages: 211