22.5 Evidence Eliminator
| < Day Day Up > |
| Other than the aforementioned fireplace or a large electromagnet, is there any other tool that can securely wipe a hard drive? Evidence Eliminator (http://www.evidence-eliminator.com) comes as close as possible to complete sterilization under Windows , while keeping the drive usable. This section is not just a laundry list of product features. We simply use the different features of this (rather comprehensive) product to show various Windows forensics concepts and tricks. For example, we will cover various places where the evidence might be (useful for both the attacking and defending sides), ways to clean and, obviously, preserve your drives , and so on. Figure 22-6 shows Evidence Eliminator in action. Figure 22-6. Evidence Eliminator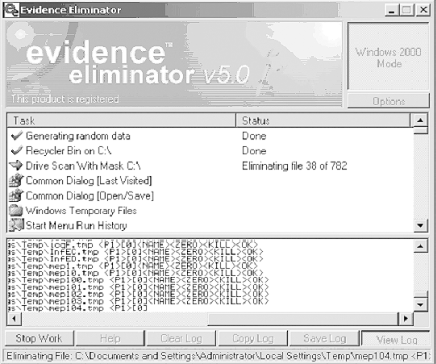 As shown in Figure 22-7, wiping utilities securely delete data by overwriting them with a series of characters . For example, the data may be overwritten with zeros or ones, multiple times. The Department of Defense recommends a wipe of seven repetitions for maximum security, but for the average user , one wipe is enough. Figure 22-7. Evidence Eliminator wiping algorithms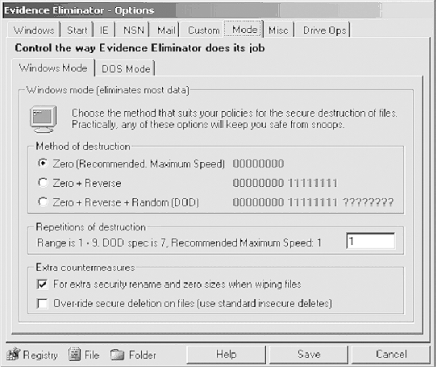 Because of the complex nature of operating systems, no drive-cleaning utility can ever be perfect, but Evidence Eliminator is very good. Among its many features, it can sanitize the Windows swap file, application logs, temporary files, and recycle bin and deleted filenames, sizes, and attributes from drive directory structures. It also cleans Windows registry backups and slack space and deleted entries in the Windows registry. Evidence Eliminator cannot delete material it does not know about, such as log entries in new or unknown programs. It may be possible for an intruder to tell the time when you last cleaned your drives. Also, when you install and then remove a program, it may leave traces in the system registry showing that it was installed at some time on that computer. Evidence Eliminator does not deal with this information, because it is difficult to automatically track every program that does not uninstall itself properly. To track such changes manually, use an uninstall manager such as the freeware InControl 5 (found at http://www.download.com), which monitors all system changes upon installation. If you are still in doubt, reformat the drive and install a fresh copy of Windows. This refreshes the system registry and clears out all traces of old program installations. The following sections briefly describe some of the recalcitrant areas on your hard drive where incriminating evidence might hide. We show how to clean these areas with Evidence Eliminator. 22.5.1 Swap FilesA swap file (more recently known as a page file ) provides your machine with virtual memory swapped from the hard disk to supplement the RAM. Swapping enhances performance by allowing the CPU to access memory beyond the physical limits of the RAM. The least recently used data in the RAM is dynamically swapped with the hard disk until the data is needed; this allows new files to be "swapped in" to the RAM. Figure 22-8 shows the Windows tab of Evidence Eliminator, which includes an option to eliminate the Windows swap file. Figure 22-8. Configuring Evidence Eliminator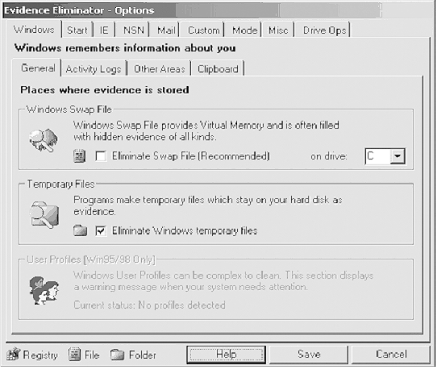 22.5.2 Temporary FilesEvidence Eliminator can also scan and wipe the Windows temporary files. Temporary files contain large amounts of evidence, and they build up quickly. Eliminating Windows temporary files, as shown in Figure 22-8, provides better security. 22.5.3 Windows Registry StreamsEvidence Eliminator can also clean Streams . Streams are history kept by Windows about your Explorer window settings. If you need to eliminate memory of file and folder accesses from Windows Explorer, it is recommended that you check these items. A side effect of cleaning Streams is that your Explorer windows will forget their appearance settings and revert to the default "Show As Web Page" settings. 22.5.4 ClipboardAfter you finish using programs or performing copy/paste operations in Windows, various data can be left behind in the system's memory. This data is vulnerable to forensic analysis and to hackers. Fortunately, you can also use Evidence Eliminator to automatically wipe clipboard memory contents. 22.5.5 Chat LogsIf you use chat or Instant Messenger programs, you must manually search under your Program Files directory for each program and view any files kept. If logs are being kept, simply add the full path of the log file to the Custom Files list in the Options window, and they will automatically be subjected to the standard data destruction process. IRC Chat users may also add their download folder to the list of Custom Folders, in order to guard against uninvited files put there by other users. 22.5.6 Browser Garbage (Internet Explorer)Evidence Eliminator also cleans the bits of garbage secretly smeared across your drive by your browser (Figure 22-9). Figure 22-9. Removing browser files Areas of cleaning include:
22.5.7 Options for Netscape Navigator UsersIf you are a user of Netscape Navigator Versions 3 or 4, you can configure Evidence Eliminator to suit the browser installed.
The default file and folder paths shown in Figure 22-10 are taken from a standard installation of Netscape, but if you have Netscape in a custom or complex configuration, you may need to change them. All evidence of your Netscape browsing will be securely eliminated if you take these steps. The hidden memory of the last download directory used to save files from Netscape will also be deleted. Figure 22-10. Browser cleanup The JavaScript section works on two files used by NSN 4. The files are prefs.js and liprefs.js . Hidden in these files is a record of web sites that you have visited. Evidence Eliminator does not delete these files, which are required by the browser: it cleans the memory URLs out of the files and leaves the rest of the data intact. Note also that the Netscape cookie function works a little differently than one in Internet Explorer. In IE, you select individual cookies to keep. But in Netscape, when you choose to keep one cookie for a domain, all cookies from that domain will be kept. For example, if you elect to save one cookie from http://www.hotmail.com , all cookies from hotmail.com will be saved. 22.5.7.1 Setting up Netscape pathsUnfortunately, Evidence Eliminator is unable to autodetect the Netscape installation folder, so it must be set up manually. The procedure is straightforward. Browse to the default installation folder for Netscape user information, C:\Program Files\Netscape\Users\ , in Windows Explorer. In there, you have folders for each user in Netscape. Go into your username folder. Username "default" will now be browsing in C:\Program Files\Netscape\Users\default\ . Open the Evidence Eliminator Options window at the NSN tab. Here are the default (standard) settings in Evidence Eliminator for Netscape. Simply change the username "default" in these paths to your own username. You may use the Browse button to easily browse to the correct files and folders.
Once they are set up, there should be no need to change these settings. If you back up your Data folder in your Evidence Eliminator installation, you may never have to change them again. |
| < Day Day Up > |
EAN: 2147483647
Pages: 211
