Information Security
|
|
The term information security covers a wide array of activities in an organization. It includes both products and processes to prevent unauthorized access, modification, and deletion of information, knowledge, data, and facts. This area also involves the protection of resources by preventing them from being disrupted by situations or attacks that may be largely beyond the control of the person responsible for information security.
From the perspective of a computer professional, you are dealing with issues that are much bigger than merely protecting computer systems from viruses. You are protecting many of the most valuable assets of an organization from people who are highly motivated to misuse those assets. Some of these people may already be inside your organization. Fortunately, most of them will be outsiders.
Unfortunately, this job is not getting any easier to do. Information about weaknesses and vulnerabilities in most commercial systems are well known and documented. Your adversaries can use search engines to find vulnerabilities on virtually any product or operating system. They can learn how to exploit the most likely weaknesses that exist in that system. You can buy books on computer hacking, join newsgroups on the Internet, and access websites that detail how to exploit system weaknesses.
In many situations, you will find yourself dealing with inherent weaknesses in the products you use. In short, you must assume that you are under attack right now, even as you read this book. The next section discusses in more detail the considerations you must make in order to have a reasonable chance of securing your information, networks, and computers. Make sure you understand that we are talking about reasonable. There is no such thing as a completely secure network. One of the first things you must develop is a bit of paranoia. It is important to remember that you are dealing with both systems' vulnerabilities, and human vulnerabilities. While they are not the same, they certainly affect the organization significantly.
Information security includes three areas of primary focus. These areas address different parts of computer security. An effective computer security plan and process must evaluate the risks and create strategies and methods to address them. This section focuses on three areas:
-
Physical Security
-
Operational Security
-
Management and Policies
Each of these areas is vital to assure security in an organization. You can think about this as a three-legged stool. If any one of the legs of your stool breaks, you will fall down and hurt yourself. You must look at the overall business and address all the issues the business faces concerning computer security. Figure 1.1 shows how these three components of computer security interact to provide a reasonably secure environment.
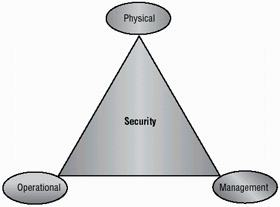
Figure 1.1: The security triad
Part of your job is to make recommendations to management about needs and deficiencies, take action to minimize the risks and exposure of your information and systems, and establish, enforce, and maintain the security of the systems with which you work. This is no small task, and you must do each element well in order to have a reasonable chance of maintaining security in your organization.
Physical Security
Physical security involves the protection of your assets and information from physical access by unauthorized personnel. These threats often present themselves as service technicians, janitors, customers, vendors, or even employees. They can steal your equipment, damage it, or take documents from offices, garbage cans, or filing cabinets. Their motivations may be as simple as greed or as complicated as a desire to steal your trade secrets to sell to a competitor as an act of vengeance.
Physical security is relatively easy to accomplish. You secure facilities by controlling access to the office, shredding unneeded documents, installing security systems, and limiting access to sensitive areas in the business. Most office buildings provide perimeter and corridor security during unoccupied hours.
Many office complexes also offer roving security patrols, multiple lock access control methods, and electronic or password access. Typically, the facility managers handle these arrangements. They will not generally deal with internal security as it relates to your records, computer systems, and papers. That is clearly your responsibility in most situations.
The first component of physical security involves making a physical location less tempting as a target. If the office or building you are in is open all the time, gaining entry into a business in the building is easy. You must prevent people from seeing your organization as a tempting target. Locking doors and installing surveillance or alarm systems can make a physical location a less desirable target. Enough "wide-open" targets involving less risk on the part of the people involved are available. Try to make your office not worth the trouble.
The second component of physical security involves detecting a penetration or theft. You want to know what was broken into, what is missing, and how the loss occurred. Passive videotape systems are one good way to do this. Most retail environments routinely tape key areas of the business to identify how thefts occur and who did them. These tapes are admissible as evidence in most courts. Law enforcement should be involved as soon as a penetration or theft occurs.
The third component of physical security involves recovering from a theft or loss of critical information or systems. How will the organization recover from the loss and get on with the normal business of the organization? If a vandal destroyed your server room, how long would it take your organization to get back into operation, and fully productive?
Recovery involves a great deal of planning, thought, and testing. What would happen if the files containing all of your bank accounts, purchase orders, and customer information became a pile of ashes in the middle of the smoldering ruins that used to be your office? Ideally, critical copies of records and inventories should be stored off site in a secure facility.
Operational Security
Operational security deals with how your organization does things. This includes computers, networks, and communications systems as well as the management of information. Operational security encompasses a large area, and as a security professional you will be primarily involved in this area.
Operational security issues include access control, authentication, and security topologies after network installation is complete. Operational issues include the daily operations of the network, connections to other networks, backup plans, and recovery plans. In short, operations security encompasses everything that is not related to design or physical security in your network. The issues you address in an operational capacity can seem overwhelming at first. Many of the areas you will address are vulnerabilities in the systems you use and weak or inadequate security policies.
For example, if you implemented a comprehensive password expiration policy, you could require users to change their passwords every 30 or 60 days. If the system does not require password rotations, in that it allows a password to be reused, you have a vulnerability that you will not be able to eliminate. From an operational perspective, the system has weak password protection capabilities. There is nothing you can do short of installing a higher security logon process or replacing the operating system. Either solution may not be feasible given the costs, conversion times, and unwillingness of an organization to make this switch. You have a vulnerability that you cannot effectively counter. Most companies use software that has already been developed. These packages may require a specific operating system to be used. If that operating system has significant security problems or vulnerabilities, you will still be responsible for providing security in that environment.
Your corporate network, when connected to the Internet, becomes a potential vulnerability. You can install hardware and software to improve security, but the management may decide these measures cost too much to implement. Again, operationally there may be very little you can do about this. Much of this book will be involved in the technologies and tools used to help assure operational security. Figure 1.2 illustrates the various vulnerabilities you face from an operational perspective. One of the most effective things you can do to improve operational security is to emphasize security training for everyone in the organization.
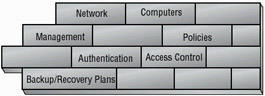
Figure 1.2: Operational Security Issues
Management and Policies
Management and policies provide the guidance, rules, and procedures for implementing a security environment. Policies, to be effective, must have the full and uncompromising support of the management team of the organization. Management directions give security initiatives the teeth they need to be effective. Information security professionals can recommend policies, but they need management support to implement them. There is nothing worse than a self-proclaimed security "czar" who has no support from management.
The issues that must be decided at the management and policy level affect the entire company and can greatly impact productivity, morale, and corporate culture. Policies also establish expectations about security related issues. These policies should treated be no differently than an organization's vacation, sick leave, or termination policies. Most people can tell you exactly how many days of vacation they get per year; however, many cannot tell you what the information usage or security policies are.
A number of key policies are needed to secure a network. The list below identifies some broad areas that require thought and planning:
-
Administrative Polices
-
Design Requirements
-
Disaster Recovery Plans
-
Information Policies
-
Security Policies
-
Usage Policies
-
User Management Polices
Administrative Policies
Administrative policies lay out guidelines and expectations for upgrades, monitoring, backups, and audits. Systems administrators and maintenance staff use these to conduct business. The policies should clearly outline how often and when upgrades appear, when and how monitoring occurs, and log reviews.
The policies must be specific enough to help the administrative staff keep focused on the business of running the systems and networks. At the same time, they must be flexible enough to allow for emergencies and unforeseen circumstances.
Design Requirements
Design requirements outline what the capabilities of the system must be. These requirements are typically part of the initial design and greatly affect what solutions you can use. Many vendors will respond to every bid and assure you that they are secure. You can use the requirements to have vendors explain proposed solutions. This policy should be very specific about security requirements. If your design does not include security as an integral part of the implementation, you can bet that your network has vulnerabilities.
Disaster Recovery Plans
Disaster recovery plans (DRP) are one of the biggest headaches that IT professionals face. The DRP is expensive to develop, expensive to test and must be kept current. Most large companies invest huge amounts of money into DRP including backup or hot sites. A hot site is a facility that is designed to provide immediate availability in the event of a system or network failure. This is covered in more depth in Chapter 9, "Security Policies and Procedures". These sites are expensive to maintain and sometimes hard to justify. The likelihood that an organization will actually need a hot site is relatively small and may seem unimportant, right up to the point when you don't have one and need one.
A good DRP will take into consideration virtually every type of occurrence or failure possible. It may be as simple as a single system failing, or as complicated as a large multinational company needing to recover from a cataclysmic disaster or event.
Information Policies
Information policies refer to the various aspects of information security. This includes access, classifications, marking and storage, and the transmission and destruction of sensitive information. The development of information policies is critical to security.
Security Policies
Security policies define how the configuration of systems and network occur. This includes the installation of software, hardware, and network connections. Security policies also define how Identification and Authorization (I&A) occurs, and they determine access control, audits, and network connectivity. Encryption and antivirus software are usually covered in these policies. The security policies also establish procedures and methods used for password selection, account expiration, failed logon attempts, and related areas.
Usage Policies
Usage policies cover how information and resources are used. You need to explain to users how they can use the organizational resources and for what purposes. These policies lay down the law about computer usage. Usage policies include statements about privacy, ownership, and consequences of improper acts. Your usage policies should clearly explain usage expectations about the Internet and e-mail.
User Management Policies
User management policies identify the various actions that must occur in the normal course of employee activities. These policies must address how new employees are added to the system. The policy should address training and orientation, as well as equipment installation and configuration.
Employee transfers are a normal part of a company. If an employee transfers to a new job, the privileges and access that they had from the old position may be inappropriate for the new position. Establishing new access rights allows the employee to continue working. If you forget to revoke the old privileges, this user may have access to more information than they need. Over time, this can result in a situation called privilege creep. The user may acquire administrative privileges to the system by accident.
Terminated employees pose a threat to information security. In some cases, a terminated employee may seek to gain access to customer lists, bank accounts, or other sensitive information. It is imperative that employees who leave the company have their accounts either disabled or deleted, and access turned off. You would be amazed at how many times the systems administrators don't know about personnel changes. Your user management policies should clearly outline who notifies the IT department about employee terminations and when it occurs.
|
|
EAN: 2147483647
Pages: 167