Privilege Management
|
|
Privilege management involves making decisions about what information is accessed, how it is accessed, and who is authorized to access it. Unlike hardware access control, these concerns deal with policy and implementation issues. Additionally, the issue of auditing is a key factor. You want to ensure that your organization does not provide more access or privileges than the individuals in the company actually need to have to do their work.
The following sections cover user and group roles, single sign-on initiatives, auditing, and access control. Each of these considerations can be used to form an effective and coherent privilege management process. These processes allow users to gain access to the information they need, to be denied access to information they do not need, and to effectively gain access to system resources.
User and Group Role Management
The process of user, group, and role management involves recognizing how work is accomplished in the organization. Most organizations have a high level of standardized tasks that do not require a great deal of privileged information in order to be accomplished. Some departments in an organization may routinely work with sensitive information about the organization or its customers. A clear set of rules specifying and limiting access can make the job of managing the process much simpler.
Let's take the example of a small business. Company XYZ has departments that are involved in sales, finance, manufacturing, vendor relations, and customer relations. Each of these departments has different information needs.
The sales department may not need to access all of the company's financial information. Someone in manufacturing might need that information. The job of establishing the various privilege levels in a company can become quite complicated. Some individuals may need to view certain information but should be prohibited from changing it. Other individuals may need to update that same information.
In a company of several dozen employees, establishing access control can be quite unmanageable. In a company of thousands, establishing access control at an individual level can be overwhelming. If each individual needs different access capabilities, thousands of access rules are required. Many operating systems and applications allow you to organize users into common groups with similar access needs so that you can more easily manage an otherwise cumbersome access puzzle.
Most operating systems allow individuals and groups to be embedded into groups. These groups are referred to as security groups. A security group can have predefined access capabilities associated with it. In this way, a comprehensive security model can be developed that addresses the accessibility needs of everyone in an organization. Figure 9.9 illustrates the group process. In this example, most individuals are placed into two departmental groups. The top user in the picture only has access to accounting applications on the ACCTG server, the middle user has access to both, and the bottom user only has access to the OFFICE server. Departmental groups access information based on established needs and predefined access.
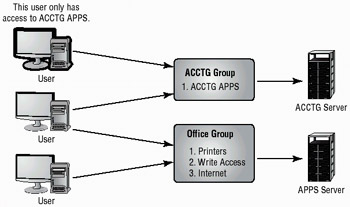
Figure 9.9: Privilege grouping
Each department may have different access capabilities. In some cases, different roles within a department will have different needs. While you may want a supervisor to have access to information about a department's performance, you may not want a clerical worker to have that same access. It comes down to an issue of trust, experience, and need.
Single Sign-On
One of the big problems that larger systems must deal with is the need to access multiple systems or applications. This may require a user to remember multiple accounts and passwords. The purpose of a single sign-on (SSO) is so that a user gains access to all of the applications and systems they need when they log on. This is becoming a reality in many environments, including Kerberos, Microsoft Active Directory, Novell eDirectory, and some certificate model implementations.
In the case of Kerberos, a single token allows any Kerberized applications to accept a user as valid. You read about Kerberos in Chapter 1, "General Security Concepts." The important thing to remember in this process is that each application that wants to use SSO must be able to accept and process the token presented by Kerberos.
Active Directory (AD) works off a slightly different method. A server that runs AD retains information about all access rights for all users and groups in the network. When a user logs on to the system, AD issues the user a globally unique identifier (GUID) that contains information about access privileges and group memberships. Applications that support AD can use this GUID to provide access control. The process of acquiring a GUID occurs when the user logs on. Figure 9.10 illustrates this process in more detail. In this instance, the database application, e-mail client, and printers all authenticate with the same log on. Like Kerberos, this process requires all of the applications that want to take advantage of AD to accept AD controls and directives.
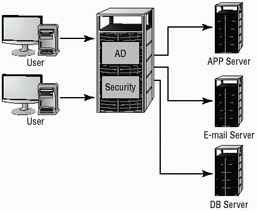
Figure 9.10: AD logon process validating a user
In this way, the user does not have to have separate sign-on, e-mail, and applications passwords. This simplifies the sign-on process for users, and it lowers the support requirements by administrators. Access can be established through groups, and it can be enforced through group memberships.
Privilege Decision Making
The process of making decisions about privilege is an important one. The process of decision making must be clear and unambiguous to be effective. In the case of a highly centralized environment, a single department or person is responsible for making decisions about access that affect the entire organization. In a decentralized organization, decision making is spread throughout the organization.
The decision-making process should be conducted by the people who are the most aware of the security needs. This process can involve everyone in the organization. If someone is unable to accomplish the work they need to do, the security system is not working.
On the other hand, it is important that personnel in the organization receive access only to the information they really need. Herein lies the problem. Establishing a standardized policy or set of policies is important. These policies, and the effects of these policies, must be well documented and enforced.
| Note | Many operating systems automatically replicate or send changes in access throughout an organization. A single change in a user's access may inadvertently give them access to sensitive information. Careful study of privileges is needed for an effective security policy. |
From time to time, individuals may need special access to information that they would not normally be given. For example, an office or clerical person might need to gather information for a special report. Specialized access should be granted only for the period of time during which they need the access. A separate account with these special privileges is usually the best way to manage these types of situations. When the special project is finished, the account can be disabled or deleted. This ensures that privileges do not permanently become associated with a user or a department. Special accounts can be monitored by security professionals who ensure that only authorized access occurs. This reduces the potential of a security violation from occurring.
Systems administrators are also subject to privilege issues. If an organization has multiple servers, a company may not want administrators to have access to all of its servers for administrative purposes. In larger organizations, company-wide access could create a very serious security risk. As a rule, you will want to grant administrative access only to specific systems and possibly grant it only at specific times. Again, this limits a company's exposure to security violations.
Auditing
Auditing is the process of ensuring that policies, procedures, and regulations are carried out in a manner consistent with organizational standards. A security audit would help determine whether privilege-granting processes are appropriate, and whether computer usage and escalation processes are in place and working. An auditor can be thought of as a consultant in your organization charged with helping to ensure that procedures are followed.
An auditor who is doing a good job should pull no punches, and she should offer concrete suggestions on how to improve. These suggestions may pertain to areas of improvement in contingency planning, to security and access problems, or to physical control issues. The information an auditor provides is extremely valuable; acting on it can save your organization time and aggravation. You may not like the results of the audit, but they can be used as a valuable tool to help improve the organization.
The following sections discuss the need to verify that users are given appropriate permissions to accomplish the work they are assigned.
Privilege Auditing
Privilege audits verify that accounts, groups, and roles are correctly assigned and verify that policies are being followed. An audit should verify that access is established correctly, security is in place, and policies are effective. A privilege audit might entail a complete review of all accounts and groups to ensure they are correctly implemented and up-to-date.
The problems associated with the transfer of an individual in an organization are common. When a personnel transfer occurs, the transferred user needs to be removed from old groups. Failing to do so can cause privilege creep to become a problem. Privilege creep occurs when an individual accidentally gains a higher level of access than they would normally be entitled to or need.
Usage Auditing
Usage auditing verifies that systems and software are used appropriately and consistently with organizational policies. A usage audit may entail physically inspecting systems, verifying software configurations, and other activities intended to prove that resources are being used appropriately.
A major concern, while not primarily a security concern, is the issue of installed software and licensing. Illegal use of unlicensed software can carry very stiff penalties. Examining systems on a periodic basis verifies that only the software that an organization is licensed to use is installed.
From a security perspective, some software is more vulnerable to software exploitation than other software. If vulnerable software is installed, it may create a backdoor or other unauthorized usage problem. Periodically inspecting systems to ensure that software updates are current and that only approved software is installed is a good idea. Usage audits also examine network usage. Is your network being used for illicit purposes? Is pornography present in your environment? Any number of other problems can be discovered. By performing audits, you can help deter potentially embarrassing or even illegal activities from occurring in your environment.
Your company has undergone its umpteenth reorganization. Many people have been moved to new positions within the new organizational chart. You have been asked to verify that users can access the information they need to perform their jobs. You also need to make sure that any inappropriate access is removed.
To successfully complete your assignment, you will need to inspect every user account and group to verify which user accounts belong to which groups. You also need to verify that each group has the appropriate access to the servers and other resources needed to accomplish their assignments.
In many newer systems, you can accomplish this by inspecting the access groups they belong to and by adding or deleting user accounts as appropriate. If you are using a network that does not support security groups, you will need to modify the access rights of each account individually.
Escalation Audits
Escalation audits help ensure that procedures and communications methods are working properly in the event of a problem or issue. Escalation is primary focused around the issue of gaining access to decision makers in a time of crisis to make decisions. These types of audits test your organization to ensure it has the appropriate procedures, policies, and tools to deal with any problems in the event of an emergency, catastrophe, or other need for management intervention.
Disaster recovery plans, business continuity plans, and other plans are tested and verified for accuracy. These types of plans require constant care or they become dated and ineffective. An audit can help ensure that all bases are covered and that the plans have a high likelihood of success when needed.
A good way to determine if your escalation processes are working is to test them. Many organizations develop scenarios to verify that mechanisms are in place to deal with certain situations. If the president of the organization is out of town or unavailable, who has the authority to make a decision about transitioning to an alternative site? If these issues can be worked out in advance, they are much less difficult to deal with in emergencies.
Reports to Management
An audit should always conclude with a report to management. This report should outline any strengths and weaknesses in the organization as they existed at the time of the audit. The audit should also explain any violations of policy, recommendations for improvement, and recommendations for the organization overall. This report is a vital part of the process, and it provides a mechanism that can be used to develop corrective action plans and updated policies.
Access Control
The last section of this chapter deals with access control methods from a business perspective. The three primary methods of access control are mandatory (MAC), discretionary (DAC), and role based (RBAC). Each of these methods has advantages and disadvantages to the organization from a security perspective.
The method you choose will be greatly affected by your organization's beliefs about how information needs to be shared. In a high security environment, the tendency would be to implement either a MAC or RBAC method. In a traditional business environment or school, the tendency would be to implement a DAC method. You should do some consulting within the organization to understand how a particular department and how the entire organization wants to implement access control models. This will allow you to gather input from all concerned parties regarding how access guidelines should be established and how security should be implemented.
In the following sections, we will take a look at each of these methods from a business perspective. You learned about the technical aspects in earlier chapters.
Mandatory Access Control
Mandatory Access Control (MAC) is a method that clearly defines an inflexible manner of how information is accessed. In a MAC environment, all access capabilities are predefined. Users do not have the ability to share information that was not established by administrators. Systems administrators must make any changes that need to be made. This enforces a rigid model of security. For a MAC model to work effectively, administrators and network designers must think relationships through very carefully. The advantage of this model is that security access is well established and defined, making security breaches easier to investigate and correct. A well- designed MAC model can make the job of information control easier and it can essentially lock down a network. The major disadvantages of this model are the lack of flexibility and the fact that its needs change over time. The inability of administrative staff to address these changes can sometimes make it hard to keep up.
Discretionary Access Control
In a Discretionary Access Control (DAC) model, network users have some flexibility regarding how information is accessed. This model allows users to dynamically share information with other users. The process allows a more flexible environment, but it increases the risk of unauthorized disclosure of information. Administrators will have a more difficult time ensuring that information access is controlled and that only appropriate access is given.
Role-Based Access Control
Role-Based Access Control (RBAC) models approach the problem of access control based on established roles in an organization. RBAC models implement access by job function or by responsibility. Each employee will have one or more roles that allow access to specific information. If a person moves from one role to another, the access for the previous role will no longer be available. RBAC models provide more flexibility than a MAC model and less flexibility than the DAC model. They do, however, have the advantage of being strictly based on job function, as opposed to individual needs.
|
|
EAN: 2147483647
Pages: 167