Policies and Procedures
|
|
The policies and procedures your organization uses have a huge impact on your ability to manage a secure environment. Although your primary role is not that of policy maker, you need to understand four critical areas to succeed. This section discusses personnel, business, certificate, and incident response policies.
Personnel Policies
Personnel policies help the organization set standards and enforce behaviors. From a security perspective, this is critical. As a security administrator, you will not generally be making policy decisions, but you have an impact on how policies are developed, and enforced.
Personnel policies that consider security requirements will make your job easier. If the people the company hires are trustworthy, internal security problems will diminish. This will free up resources to address other aspects of the business that need attention. In the following sections, we will look at each of the security policies.
Hiring Policies
Hiring policies define how individuals are brought into an organization. They also establish the process used to screen prospective employees for openings. Your organizational hiring policies should establish expectations for both the interviewer and the prospective employee.
Most organizations that work with the government have mandatory drug testing requirements. Experience and studies have shown that drug users have a tendency to perform inconsistently, have higher incidents of theft, and are vulnerable to social engineering or compromises such as blackmail.
Your organization should also investigate references, college degrees, certifications, and any other information that is provided as part of the screening process.
From a security perspective, you want to make sure that the people using your systems and accessing your information are not using it in ways inconsistent with policy.
Security professionals should be screened more thoroughly than many other employees. A special trust is being imparted to security professionals, this trust should be given only to people who are worthy of it.
Termination Policies
Termination policies involve more than simply firing a person. Your organization needs to have a clear process for informing affected departments of voluntary and involuntary terminations. When an employee leaves a company, their computer access should be discontinued immediately.
If an involuntary termination occurs, you should back up the system they use, as well as any files on servers before the termination occurs. Terminations are very emotional times. If information is archived before the termination, there is less chance that critical records will be lost if the employee does something irrational. Most people will not do anything unusual, but you are better safe than sorry.
Make sure your termination policies mandate that the appropriate staff is notified when a termination is about to occur so that accounts can be disabled, systems backed up, and any other measures taken that are deemed appropriate can be performed.
| Note | Many times a termination policy will include the clause that, upon termination, a former employee must be escorted at all times while performing post- termination activities (e.g., cleaning out their desk, hauling items to their car). |
Ethics Policies
Ethics is perhaps best described as the personnel or organizational rules about how interactions, relationships, and dealings occur. Ethics affect business practices, are the basis of laws, and are highly subjective.
Many organizations define ethical behavior and the consequences of not behaving in an ethical manner. Most professional organizations have adopted professional codes of ethics or conduct for their members. In many cases, a violation of these ethics laws will result in suspension, expulsion, or censure by the professional organization.
One organization, the Computer Professionals for Social Responsibility (CPSR) has created the Ten Commandments of computer ethics. These commandments were developed in conjunction with the Computer Ethics Institute (CEI). Their commandments (as found on their website www.cpsr.org) are listed here:
-
Thou shalt not use a computer to harm other people.
-
Thou shalt not interfere with other people's computer work.
-
Thou shalt not snoop around in other people's computer files.
-
Thou shalt not use a computer to steal.
-
Thou shalt not use a computer to bear false witness.
-
Thou shalt not copy or use proprietary software for which you have not paid.
-
Thou shalt not use other people's computer resources without authorization or proper compensation.
-
Thou shalt not appropriate other people's intellectual output.
-
Thou shalt think about the social consequences of the program you are writing or the system you are designing.
-
Thou shalt always use a computer in ways that ensure consideration and respect for your fellow humans.
This list, as you can see, outlines computer usage and ethical behavior for computer professionals. These Ten Commandments establish a code of behavior and trust that is very important for security and computer security professionals. This list is a good place to start in the development of both a personnel ethics code and an organizational ethics code.
Acceptable Use Policy
Acceptable Use policies deal primarily with computers and information provided by the company. Your policy should clearly stipulate what activities are allowed and what activities are not allowed. This policy can be as simple as a blanket statement such as "Computers provided by the company are for company business use only."
Many companies have developed comprehensive policies concerning web access, e-mail usage, and private usage. Having an Acceptable Use policy in place eliminates any uncertainty regarding is and what isn't allowed in your organization.
Acceptable Use policies should also include rules regarding telephone system usage, information usage, and other related issues. Once these policies are put into place, enforcing them is critical. If an employee is using your corporate computer systems for an unacceptable purpose such as child pornography, you must consistently enforce company policy to stop the behavior and discourage future abuses.
If your organization fails to enforce its policies consistently, it is opening itself to potential lawsuits.
Privacy and Compartmentalized Information Policies
Privacy requirements for corporate information are essential parts of the policies needed by an organization. You must clearly state what information can and cannot be disclosed. These Privacy policies must also specify who is entitled to ask for information within the organization and what types of information employees are provided. The process of establishing boundaries for information sharing is called compartmentalization. It is a standard method of protecting information.
Your policies must also clearly state that employees should have no expectations of privacy. Employers are allowed to search desks, computers, files, and any other items brought into the building. Your policy should also state that e-mails and telephone communications could be monitored. Monitoring can occur without the employee's permission or knowledge. Many employees wrongly assume they have a right to privacy when they in fact do not. By explicitly stating your policies, you can avoid misunderstandings and potentially prevent employees from embarrassing themselves.
Need to Know Policies
The need to know is a fundamental premise for security professionals. Need to Know policies allow people in an organization to withhold the release of classified or sensitive information from others in the company. The more people have access to sensitive information, the more likely it is that this information will be disclosed to unauthorized personnel. A Need to Know policy is not intended to prohibit people from accessing information they need; it is meant to minimize unauthorized access.
Many naturally curious individuals like to gain sensitive information just for the fun of it. No doubt, you have known someone who is a gossip. They will tell everybody the secrets they know. This can prove embarrassing to the organization or the people in the organization.
Background Investigations
Background investigations potentially involve more than checking references. A good background investigation should include credit history and criminal record checks, as well as information about work experience and education. These checks must be done with the permission of the employee or prospective employee. The failure to agree to this type of investigation does not mean that the individual has a problem in their background; it may mean they value their privacy.
It is a good idea for employees who deal with sensitive information, such as security professionals, to have a thorough background investigation. This ensures that employees are who they say they are and have the education they say they do. A thorough background check should weed out individuals who have misrepresented their background and experiences.
| Note | Recently, a college ran a routine check of the professors and instructors they had hired over the previous five years. Almost 20 percent of the professors had misrepresented the degrees they held and which schools they had attended. Most schools now require full school transcripts from college professors before they hire them. |
Business Policies
Business policies also affect the security of an organization. Business polices address organizational and departmental business issues, as opposed to corporate-wide personnel issues. When developing your business policy, you must consider these three primary areas of concern; separation of duties, physical access control, and document destruction. This section discusses these three areas.
Separation of Duties Policies
Separation of Duties policies are designed to reduce the risk of fraud and prevent other losses in an organization. A good policy will require more than one person to accomplish key processes. This may mean that the person who processes an order from a customer is not the same person who generates the invoice or deals with the billing.
Separation of duties helps prevent an individual from embezzling money from the company. In order to successfully embezzle funds, an individual would need to recruit others to commit an act of collusion. Collusion is an agreement between two or more parties established for the purpose of committing deception or fraud. Collusion, when part of a crime, is also a criminal act.
Separation of duty policies can help prevent accidents from occurring in an organization.
Let's say you are managing a software development project. You want someone to perform a quality assurance test on a new piece of code before it is put into production. Establishing a clear separation of duties prevents development code from entering production status until quality testing is accomplished.
Many banks and financial institutions require multiple steps and approvals to transfer money. This helps reduce errors and minimizes the likelihood of fraud.
Due Care Policies
Due Care policies identify what level of care is used to maintain the confidentiality of private information. These policies specify how information is to be handled. The objectives of Due Care policies are to protect and safeguard customer and/or client records. The unauthorized disclosure of this information creates a strong potential for liability and lawsuits. Everyone in an organization must be aware and be held to a standard of due care with confidential records.
Physical Access Control Policies
Physical Access Control policies refer to the authorization of individuals to access facilities or systems that contain information. Implementing a Physical Access Control policy helps prevent theft, unauthorized disclosure of information, and other problems from cropping up within an organization. Many organizations limit office hours of employees to prevent them from accessing computer systems during odd hours. This may not be appropriate for some positions, but it may be essential in others. What would happen in your company if a payroll clerk decided to give himself a raise? In all probability, they wouldn't do this under the supervision of the payroll manager. They would do it when no one was around. By limiting access to the physical premises and computer systems, you reduce the likelihood that an individual will be tempted to commit a crime.
Document Disposal and Destruction Policies
Document destruction policies define how information that is no longer needed is handled. You would want to ensure that financial, customer, and other sensitive information is disposed of properly when it is no longer needed. Most organizations use mountains of paper. Much of this paper needs to be shredded or burned to prevent unauthorized access to sensitive information. Investigate the process that your organization uses to dispose of business records; it may need to be reevaluated.
Certificate Policies
The advent of e-commerce has created a grave concern about trust. How does a customer know that they are really working with a legitimate supplier? How does a retailer know they are dealing with a legitimate customer? One of the major problems facing e-commerce providers, as well as other businesses, is the issue of fraud. Fraud, theft, and other illegal transactions cost businesses billions of dollars a year.
| Note | Certificate policies are not part of the Security+ exam. They are, however, an important aspect of the security policy and are presented here for your consideration. |
There are ways to minimize if not eliminate the losses that organizations and individuals face. One method entails the use of digital certificates and certificate policies.
Certificates allow e-mails, files, and other transactions to be signed by the originator. This signing process usually carries close to the same weight as a hand signature. Using digital signatures allows business transactions to occur in a manner that provides some level of trust between the parties involved.
| Note | One of the most common certificates in use today is the X.509 certificate. This certificate includes encryption, authentication, and a reasonable level of validity. In essence, a certificate issued by a valid certificate authority is valid in almost all cases. The exceptions to this are few, and far between. Most e-commerce providers accept the X.509 certificate or equivalent technologies. |
Certificate policies refer to the organization policies regarding the issuing and use of certificates. These policies have a huge impact on how an organization processes and works with certificates.
A Certificate policy needs to identify which certificate authorities (CA) are acceptable, how certificates are used, and how they are issued. An organization must also determine whether to use third-party CAs, such as Verisign, or to create their own CA systems. In either case, these policies have implications about trust and trusted transactions.
A trusted transaction is a transaction that occurs under the security policy administered by a trusted security domain. Your organization may decide that it can serve as its own trusted security domain and it can use third-party CAs, thus allowing for additional flexibility. Third-party CAs are usually accredited. The process of having an internal CA accredited is difficult. The accreditation process requires compliance with the policies and guidelines of the accrediting organization.
Transactions require the involvement of a minimum of two parties. In the CA environment, the two primary parties are identified as the subscriber and the relying party. The subscriber is the individual who is attempting to present the certificate proving authenticity. The relying party is the person receiving the certificate. The relying party is dependent on the certificate as the primary authentication mechanism. If this certificate comes from a CA, the CA is known as the third party. The third party is responsible for providing assurance to the relying party that the subscriber is genuine. Figure 9.8 illustrates these relationships between the parties.
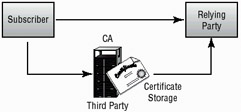
Figure 9.8: Parties in a certificate-based transaction
You may think that this sounds like a bunch of legal mumbo jumbo. Well, it is! A transaction is a legal process that is subject to dispute. If a dispute occurs, these terms will be used to identify all of the parties in the transaction. Your certificate policies should clearly outline who the valid subscribers and the third parties are in any transactions.
These policies provide your organization with a framework to identify parties, and they provide the rules detailing how to conduct transactions using e-commerce, e-mail, and other electronic media.
The practices or policies that an organization adopts for the certificate process are as important as the process that uses them. Your organization needs to develop practices and methods for dealing with certificate validity, expiration, and certificate management. These policies tend to become extremely complicated. Most CAs require a Certification Practice Statement (CPS), which defines certificate issue processes, record keeping, and legal acceptance of subscriber of the terms of the CPS.
The CA should also identify certificate expiration and revocation processes. The CA must clearly explain the certificate revocation list (CRL), and CRL dissemination policies.
Incident Response Policies
Incident response policies define how an organization will respond to an incident. These policies may involve third parties, and they need to be comprehensive. The term incident is somewhat nebulous in scope. For our purposes, an incident is any attempt to violate a security policy, a successful penetration, a compromise of a system, or any unauthorized access to information. This term includes systems failures and disruption of services in the organization.
It is important that an incident response policy minimally establish the following items:
-
Outside agencies that should be contacted or notified
-
Resources used to deal with an incident
-
Procedures to gather and secure evidence
-
List of information that should be collected about the incident
-
Outside experts that can be used to address issues if needed
-
Policies and guidelines regarding how to handle an incident
Investing time in the development process can make an incident more manageable. Many decisions about dealing with an incident will have been considered in advance. Incidents are high-stress situations; therefore, it is better to simplify the process by considering important things in advance. If civil or criminal actions are part of the process, evidence must be gathered and safeguarded properly.
Let's say that you have just discovered a situation where a fraud has been perpetrated internally using a corporate computer. You are part of the investigating team. Your incident policy lists the specialists you need to contact for an investigation. Ideally, you have already met the investigator or investigating firm, developed an understanding of how to protect the scene, and know how to properly deal with the media—if they become involved. Your policies should also outline who needs to be informed in the company, what they need to be told, and how to respond to situation.
|
|
EAN: 2147483647
Pages: 167
- Challenging the Unpredictable: Changeable Order Management Systems
- The Second Wave ERP Market: An Australian Viewpoint
- Enterprise Application Integration: New Solutions for a Solved Problem or a Challenging Research Field?
- Context Management of ERP Processes in Virtual Communities
- Development of Interactive Web Sites to Enhance Police/Community Relations