9.5 Security for Storage Networking
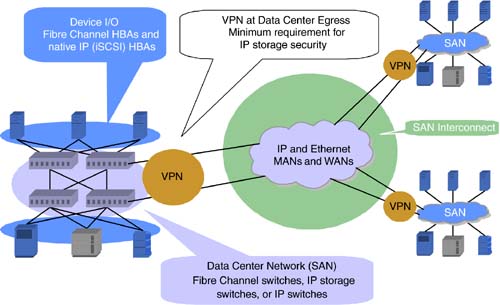
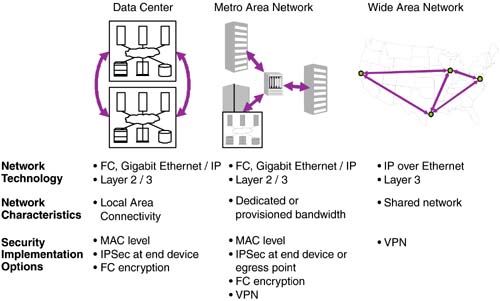
| The emergence of IP as a network transport for storage has initiated discussions about why IP is not secure for storage. While there are some valid security concerns for the merging of traditional storage and networking topologies, the vast majority of them have already been solved within the data networking community. Many storage pundits who claim IP cannot be secure seem to forget that companies have been running high-speed, secure connections for just about every other enterprise application under the sun. It is highly likely that the robust, enterprise-class security solutions companies rely on today will also work for their IP storage configurations. That said, security is a multifaceted issue that can easily conjure up fear in the mind of the consumer, which stalls adoption. On the contrary, customers should embrace the entry of IP networking to storage as a means to use the plethora of existing security solutions on the market, ranging from inexpensive, easily implemented, software-based firewalls and encryption tools to gigabit-speed, hardware-assisted 3DES encryption, the most secure commercially available encryption mechanisms. While Chapter 3, "The Software Spectrum," covered a few lower level security basics, this section clarifies the product implementations required for secure storage networking, particularly those that make use of IP storage and involve shared metropolitan- and wide-area transports. The intricacies of storage security within local environments could fill several chapters, and that discussion is intentionally left out of this section. 9.5.1 Areas of Storage SecurityThe first task in understanding IP storage security is to break down deployment areas. We can simplify these areas into device I/O, data center SANs, and the SAN interconnect. Device I/O represents the server HBAs or subsystem controllers. These could be either Fibre Channel, IP, or other interface technology. Data center SANs are generally made up of Fibre Channel switches, IP storage switches, or regular IP and Ethernet switches. The third area, SAN Extension, is typically IP- and Ethernet-focused using a layer one optical transport. Each area mandates the appropriate level of security. For the data center SAN, numerous security solutions exist within Fibre Channel fabrics and new IP storage fabrics . Features like zoning and authentication ensure that only the right users have access to the right storage at any given time. Implemented through a variety of hardware and software features, existing data center SAN security provides a high degree of protection. Often, security threats focus on mixing traditional SAN topologies with other data center networking topologies. IP storage configurations do not mandate a mix of these networks, and it is perfectly legitimate for customers to have a completely separate IP and Ethernet infrastructure for storage traffic. In fact, many customers do this today to keep heavy-load NAS traffic apart from day-to-day LAN messaging traffic. Also within the data center SAN, the device I/O components can assist in security features. Fibre Channel HBAs are recognized by Fibre Channel switches and incorporated into standard zoning features. Fibre Channel HBAs can also be recognized by IP storage switches that convert the Fibre Channel traffic to an IP core . In both cases, SAN fabric management provides for security features of zoning, authentication, and access. For IP end systems, such as iSCSI HBAs, some industry debate has taken place as to whether those devices should build in IP encryption. While some customers may want to have every IP end node encrypt traffic, the performance penalty for such security can be high. Further, it is unlikely that in a small, data center IP SAN, IP storage traffic between a server and a storage subsystem is vulnerable to attack ”at least, it is no more vulnerable than any other type of IP traffic within the company's network. Most frequently, companies protect their LANs and similarly can protect their IP storage networks with IP security protection that resides at the egress point of the data center. In networking terms, the demarcation point is often referred to as the firewall between the internal corporate systems and external Web-focused systems. This demarcation point can be effectively used for IP security solutions as well. Figure 9-11 shows the different areas of storage security and where VPN equipment comes into play for protecting data center SANs. VPNs allow customers to create secure, encrypted connections between two identified end points. This is an economical security solution when combined with shared metropolitan- and wide-area IP transport. Figure 9-11. Areas for storage security. Other security solutions can be implemented across local-, metropolitan-, and wide-area topologies. In layer one networks the security is physical ”different links or optical wavelengths keep data paths separate. In layer two networks the security may use the Media Access Control (MAC) layer. Each end device has a unique MAC address, such as Ethernet MAC or Fibre Channel MAC, that can be used to assist with authentication. Fibre Channel encryption and IP encryption (IPSec) are possible within data center SANs and can be implemented either on the end-node device or within the switching network. For layer three transports, often used in the wide area, VPNs are the most common form of security. These implementations are outlined in Figure 9-12. Figure 9-12. Sample security implementation across data center, MANs, and WANs. |
EAN: 2147483647
Pages: 108