6.1 Assessing Business Continuity Objectives
| Anyone even peripherally connected to information technology recognizes that the number of business continuance-level applications has dramatically increased in the last few years . However, the levels of availability required for each application vary dramatically. Assessing each application's availability requirements allows storage and networking administrators to target appropriate solutions. While assessment of application criticality may be relatively simple for some businesses, in most cases the process can be complex and time-consuming . This is especially true of applications that have evolved over a period of time with nonuniform development processes. Dependency between applications contributes significantly to this complexity. For example, if application A relies on a feed from a database controlled by a separate application B to provide mission-critical information, having complete redundancy for A will be of no use if B is not available. An application itself could physically be running on several servers with their associated storage systems. For example, a client-server ERP application could consist of Web servers, front-end application servers, and a back-end database server. For complex, interdependent application systems, a single individual or group will not likely have complete information to assess the various components ' availability needs. In such cases, a cross-departmental internal task force or outsourced third-party business continuance specialist may undertake the assessment project. Some of the steps to be taken in the assessment process include
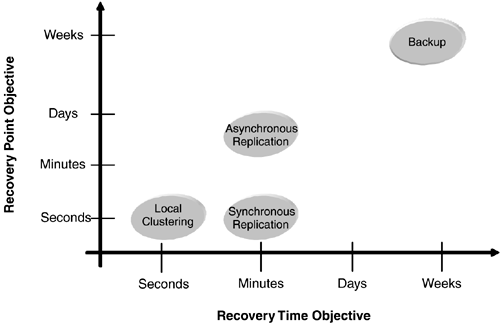
Two key metrics that identify the level of availability required for applications and data, especially in a disaster recovery scenario, are recovery time objective (RTO) and recovery point objective (RPO). 6.1.1 Recovery Time ObjectiveRTO measures the acceptable time for recovery. It poses the question, How long can the application be down? Cost and downtime implications determine RTO for a given application. There have been several studies on the cost of downtime for specific market segment applications in retail, telecommunications, manufacturing, e-commerce, energy, and financial services. These studies often take into account not just the short-term tangible loss in revenue, but also the intangible long- term effects. While these studies provide useful data, organizations can greatly benefit by performing a thorough assessment customized to their environment. RTO for an application in turn helps determine the tools and technologies required to deploy the appropriate availability level. For example, if the RTO for a given application is seven days, then restoring from backup tapes may be adequate. If the RTO is a few minutes, wide-area replication and failover may be required in case of a disaster. 6.1.2 Recovery Point ObjectiveRPO measures the earliest point in time to which the application and data can be recovered. Simply put, how much data can be lost? The nature of the particular application typically determines the RPO. In case of a major data center outage , it may be acceptable for certain applications to lose up to one week's worth of data. This could be from a human resources application in which data can be reentered from other document sources. Once again, as in the case of RTO, RPO helps determine the tools and technologies for specific application availability requirements. If, for example, the RPO for our human resources application is indeed determined to be seven days, then restoring from backup tapes may be adequate. However, for a banking application that deals with electronic funds transfer, the RPO is likely to be secondsif that. In this case, in the event of a data center outage, nothing short of synchronous data replication may suffice. Sample storage application placements against RTO and RPO are outlined in Figure 6-2. Figure 6-2. Sample storage application placements against RPO and RTO. 6.1.3 Factors Affecting the Choice of SolutionSeveral factors must be considered when determining the criticality and design of business-continuance solutions for specific applications.
|
EAN: 2147483647
Pages: 108