Chapter 13: Network Access Layer Security Protocols
In this chapter, we focus on some security protocols that have been proposed, specified, implemented, and deployed for the network access layer of the Internet model. More specifically, we introduce the topic in Section 13.1, elaborate on three conceptually similar network access layer security protocols in Sections 13.2 to 13.4, and draw some conclusions in Section 13.5.
13.1 INTRODUCTION
As mentioned in Chapter 2, the network access layer handles issues related to local area networking and dial-up connectivity in the Internet model and the corresponding TCP/IP communications protocol stack. Protocols that operate at this layer[1] include Ethernet (IEEE 802.3), token bus (IEEE 802.4), token ring (IEEE 802.5), FDDI, and protocols for serial line dial-up networking, such as the Serial Line IP (SLIP) protocol [1] and the Point-to-Point Protocol (PPP) [2]. SLIP and PPP both define encapsulation mechanisms for transporting multiprotocol data across layer two point-to-point links (e.g., serial lines). For all practical purposes, Ethernet is the most widely used and deployed technology for local area networking, and PPP is the most widely deployed protocol for dial-up networking.
In the late 1980s, the IEEE started to address issues related to LAN and metropolitan area network (MAN) security. In particular, the IEEE 802.10 working group (WG) was formed in May 1988 to address LAN and MAN security. Meanwhile, the IEEE 802.10 WG specified several standards for interoperable LAN/MAN security (SILS) that are compatible with existing IEEE 802 and OSI specifications [3, 4]. Unfortunately, SILS has not been commercially successful, and there are hardly any products that implement the SILS specifications. Consequently, we do not address the work of the IEEE 802.10 WG in this book. Instead, we elaborate on recent work that was done to secure dial-up connections using PPP with some security enhancements.
First of all, we consider the problem that a European conference attendee traveling in the United States faces if he or she wants to connect his or her laptop computer to his or her corporate intranet in Europe (e.g., to read e-mail messages or download a PowerPoint presentation). The situation is illustrated in Figure 13.1. There are at least two solutions for this problem:
-
A very obvious solution for the problem is to use the public-switched telephone network (PSTN) or the integrated switched digital network (ISDN) to connect to a remote access server (RAS) located on the corporate intranet (e.g., a modem pool), to set up a PPP connection, and to use this connection to log into the destination server located on the corporate intranet. The major advantages of this solution are availability and simplicity, whereas the major disadvantages are related to security and costs:
-
The problem related to security is that the data traffic between the laptop computer and the intranet server goes unencrypted and unprotected.
-
The problem related to costs is that the user is charged a long-distance call (or the company is charged the fees in the case of a modem pool with free charging or dial-back facilities).
-
-
A more sophisticated solution for the problem is to use a virtual private network (VPN) channel or tunnel. As we discuss later, there are many technologies that refer to and make use of the term VPN. Some of these technologies use cryptography to encapsulate data traffic and to establish and maintain cryptographically protected tunnels between the communicating peers. There are basically two approaches to create a VPN tunnel:
-
One possibility is to encapsulate a given network layer protocol, such as IP, IPX, or AppleTalk, inside PPP, to cryptographically protect the PPP frames and to encapsulate the data inside a tunneling protocol, which is typically IP (but could also be ATM or Frame Relay). This approach is commonly referred to as "layer 2 tunneling" because the passenger of the tunneling scheme is actually a layer 2 protocol (i.e., PPP).
-
Another possibility is to encapsulate a given network layer protocol, such as IP, IPX, or AppleTalk, directly into a tunneling protocol, such as 3Com's Virtual Tunneling Protocol (VTP), and to encapsulate the data inside a tunneling protocol (e.g., IP). This approach is commonly referred to as "layer 3 tunneling" because the passenger of the tunneling scheme is actually a layer 3 protocol (i.e., VTP).
-
Figure 13.1: Graphical illustration of the problem facing a conference attendee who is traveling in the United States and wants to connect his or her laptop computer to his or her corporate intranet in Europe.
Figure 13.2 illustrates and puts into perspective the layer 2 tunneling and layer 3 tunneling encapsulation schemes (for IPX encapsulated inside IP). The major advantages of VPN tunnels are related to the fact that data traffic is encapsulated in IP packets that can be routed over the Internet and that cryptographic techniques can then be used to protect the IP packets.
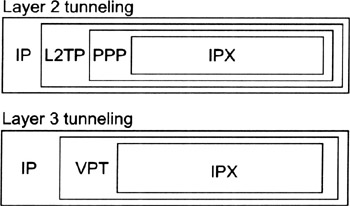
Figure 13.2: The layer 2 and layer 3 tunneling encapsulation schemes.
The first solution is simple and straightforward; it does not deserve further explanation. In the following sections we elaborate on the second solution. In particular, we briefly overview and partly discuss the layer 2 forwarding/tunneling protocols that have been proposed and deployed in the past (layer 3 tunneling protocols are addressed in Chapter 14). Today, there is a strong consensus that the Layer 2 Tunneling Protocol (L2TP) is the preferred choice for applications that want to use layer 2 tunneling. Therefore, the layer 2 tunneling protocol used in Figure 13.2 is the L2TP.
Figure 13.3 illustrates the layer 2 forwarding/tunneling solution to the conference attendee problem previously mentioned. In this solution, the connection is tunneled from the Internet service provider's point of presence (POP) to the RAS or network access server (NAS) that is typically located at the firewall of the corporate intranet.
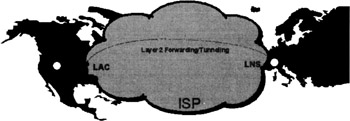
Figure 13.3: Graphical illustration of the layer 2 forwarding/tunneling solution for the conference attendee problem.
Following the terminolgy introduced by the L2TP specifications, the following terms and acronyms are used in Figure 13.3 and the remainder of this chapter (instead of POP and RAS[2]):
-
A remote system or dial-up client is a computer system or router that is either the initiator or recipient of a layer 2 tunnel. In Figure 13.3, the white bullet on the left represents the remote system or dial-up client.
-
An L2TP access concentrator (LAC) is a node that acts as one side of a layer 2 tunnel endpoint and is a peer to the layer 2 tunneling protocol server (e.g., the L2TP network server discussed next). As such, the LAC sits between the remote system or dial-up client and the server and forwards packets to and from each. The connection from the LAC to the remote system is either local or a PPP link. In Figure 13.3, the second case is illustrated, meaning that the remote system uses PPP to connect to the LAC. Contrary to that, IP packets exchanged between the LAC and the server require tunneling with a layer 2 forwarding/tunneling protocol.
-
Finally, an L2TP network server (LNS) is a node that acts as one side of a layer 2 tunnel endpoint and is a peer to the LAC. As such, the LNS is the logical termination point of a PPP session that is being tunneled from the remote system by the LAC.
Note that the LAC and the LNS require a common understanding of the encapsulation protocol so that layer 2 frames (e.g., PPP frames) can be successfully transmitted and received across the Internet. Also note that in this terminology, an NAS is a device providing local network access to users across a remote access network, such as the PSTN or ISDN. As such, an NAS may serve as either a LAC, LNS, or both.
In the following sections, we briefly overview and discuss three layer 2 forwarding/tunneling protocols that have been developed, proposed, implemented, and deployed in the past.
[1]Remember that the protocols that operate at this layer are generally referred to as media access layer protocols or network access layer protocols.
[2]Because the term RAS is heavily used in the PPTP implementation of Microsoft, we use it when we discuss MS-PPTP later in this chapter.
| Team-Fly |
EAN: 2147483647
Pages: 144
- Chapter VI Web Site Quality and Usability in E-Commerce
- Chapter VIII Personalization Systems and Their Deployment as Web Site Interface Design Decisions
- Chapter XIII Shopping Agent Web Sites: A Comparative Shopping Environment
- Chapter XVI Turning Web Surfers into Loyal Customers: Cognitive Lock-In Through Interface Design and Web Site Usability
- Chapter XVIII Web Systems Design, Litigation, and Online Consumer Behavior