Chapter 11: Firewall Configurations
A firewall configuration typically consists of packet filters and application gateways (i.e., circuit-level and application-level gateways). In theory, there are many possibilities to combine these components. In practice, however, there are only three firewall configurations that are used and widely deployed on the Internet [1, 2]. In Sections 11.1 to 11.3, we overview and briefly discuss dual-homed firewall, screened host firewall, and screened subnet firewall configurations. Furthermore, we address network address translation (NAT) in Section 11.4, possibilities to protect a firewall against denial of service attacks in Section 11.5, and firewall certification in Section 11.6.
11.1 DUAL-HOMED FIREWALL CONFIGURATIONS
In TCP/IP parlance, the term multihomed host refers to a host with multiple network interfaces. Usually, each network interface is connected to a separate network segment and the multihomed host can typically forward or route IP packets between those network segments. If, however, IP forwarding and IP routing are disabled on the multihomed host, it provides isolation between the network segments and may be used in a firewall configuration accordingly. To disable IP routing is usually a relatively simple and straightforward task. It basically means to turn off any program that might be advertising the host as a router. To disable IP forwarding is considerably more difficult and may require modifying the operating system kernel. Fortunately, a number of operating system vendors provide a simple possibility to make this kernel modification and to turn off IP forwarding accordingly.
A dual-homed host is a special case of a multihomed host, namely one that has exactly two network interfaces. Again, IP routing and IP forwarding can be disabled to provide isolation between the two network segments the dual-homed host interconnects.
As illustrated in Figure 11.1, a simple dual-homed firewall configuration may consist of a dual-homed host (i.e., a host with two network interfaces) that serves as a bastion host. IP routing and IP forwarding are disabled so that IP packets can no longer be routed or forwarded between the two network interfaces. Consequently, any data received from one network interface and sent to the other network interface must be processed by an application-level process (i.e., the application gateway) running on the bastion host. Note that Figure 11.1 is simplified in the sense that the routers are not illustrated (they are assumed to be part of the intranet and Internet environments).
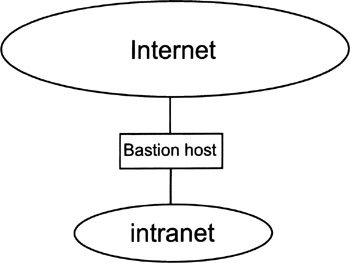
Figure 11.1: A simple dual-homed firewall configuration.
Contrary to Figure 11.1, Figure 11.2 illustrates a more realistic configuration of a dual-homed firewall. In this configuration, the bastion host's external network interface is connected to an outer network segment and the bastion host's internal network interface is connected to an inner network segment:
-
The outer network segment hosts a screening router that is interconnected (and serves as an access router) to the Internet. The aim of the screening router is to ensure that any outbound IP packet carries the IP address of the bastion host as its source IP address, and that any inbound IP packet carries the IP address of the bastion host as its destination IP address. The packet-filtering rules must be configured accordingly.
-
Similarly, the inner network segment hosts a screening router that is interconnected to the intranet. The aim of this screening router is to make sure that any outbound IP packet carries the IP address of the bastion host as its destination IP address, and that any inbound IP packet carries the IP address of the bastion host as its source IP address. Again, the packet-filtering rules must be configured accordingly.
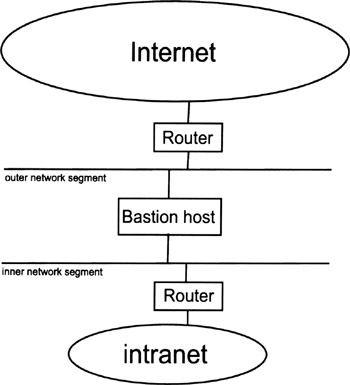
Figure 11.2: A more realistic configuration of a dual-homed firewall.
In the firewall configuration illustrated in Figure 11.2, the outer network segment can also be used to host specific (noncritical) server systems, such as public Web servers, DNS servers with public information, or access servers for other networks (e.g., modem pools for the PSTN or ISDN). This is common practice to make server systems and corresponding services publicly available and accessible from the Internet. In some literature, the outer network segment is labeled "red" and the inner network segment is labeled "blue" to refer to their different sensitivity and security status.
It is fairly obvious that the bastion host (and the application gateways running on it) can be replicated an arbitrary number of times in a dual-homed firewall configuration (e.g., to improve throughput). The resulting configuration is sometimes also called a parallel dual-homed firewall. It may consist of several bastion hosts that are all connected to the same inner and outer network segments.
The dual-homed firewall is a simple and highly secure firewall configuration. The security originates from the fact that all data must pass an application gateway to get from one network interface of the bastion host to the other. There is no possibility of bypassing the bastion host or its application gateways. There are, however, also several disadvantages that are important in practice, and that should be considered with care accordingly:
-
Performance is a problem because the bastion host may become a bottleneck (note that all data must pass the bastion host).
-
The bastion host represents a single point of failure. If it crashes, Internet connectivity is also lost.
-
There are some practical problems related to TCP/IP application protocols with no proxy support (e.g., proprietary protocols). In this case, the dual-homed firewall configuration turns out to be rather inflexible, and this inflexibility could turn out to be disadvantageous.
In summary, the dual-homed firewall configuration is used and widely deployed on the Internet. It is highly secure but rather inflexible. Contrary to this, the screened host and screened subnet firewall configurations discussed next are more flexible but also less secure. Consequently, where throughput and flexibility are important or required, these configurations may in fact be the preferable choices.
| Team-Fly |
EAN: 2147483647
Pages: 144