Background and Function
| | ||
| | ||
| | ||
To understand how e-mail works, one must understand the protocols in use. Simple e-mail Transport Protocol (SMTP) and Enhanced SMTP (eSMTP) are the protocols primarily responsible for transporting e-mail between servers on the Internet. Other protocols such as Post Office Protocol Version 3 (POP3) and Internet Message Access Protocol Version 4 (IMAP4) are used to gain access to e-mail once it is delivered to the final e-mail server store. The Domain Name Service (DNS) is used by e-mail systems to determine e-mail routing (through mail exchanger, or MX, records) and to conduct name -to-IP address resolution. E-mail exchangers are used by organizations worldwide to transfer electronic e-mail across domain boundaries. The Message Transfer Agent (MTA) of an e-mail exchanger is responsible for delivering and accepting e-mail. The following steps summarize how an e-mail message is transferred between organizations:
-
A message is sent by a user from Organization A destined for "recipient@organizationB."
-
The e-mail client sends the message to Organization A's e-mail server.
-
Organization A's e-mail server conducts a series of name lookups through DNS to determine the publicly available e-mail server for Organization B.
-
The first lookup is for an MX record or records for Organization B.
-
The second is a name lookup to determine the numeric IP address.
-
-
Organization A's e-mail server then opens an SMTP connection on port TCP/25 to Organization B's e-mail server (as defined in the name lookups).
-
Through a series of SMTP commands, Organization A transfers the message to Organization B.
-
Organization B's e-mail server transfers the e-mail message to the appropriate e-mailbox within the organization.
-
Recipient@organizationB opens his or her e-mail client and the message is delivered to the e-mail client by Organization B's e-mail server.
A graphical example of e-mail exchanger and MTA workings is shown here:
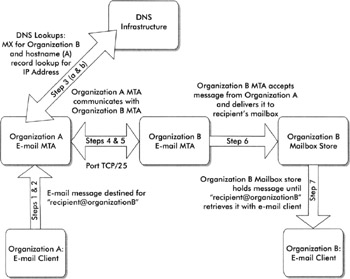
There are several more detailed steps for an e-mail message to be delivered; however, the basic summary above provides information pertinent to the topics of this chapter. The purpose of this chapter is to provide information regarding the public e-mail infrastructure and how to secure it within your organization. You may have servers provisioned for delivering and accepting e-mail (mail relays and exchangers) and separate e-mail server infrastructure only available on your private local area network (LAN) for internal e-mail storage and collaboration. While many of the techniques used for mail relays and exchangers also apply to your internal mail servers, these internal servers are not part of the scope of this chapter's discussion as we are focused on MTA services available publicly.
The public e-mail infrastructure design considerations we will explore include e-mail gateways and relays, filtering e-mail at the border (anti-virus, anti-spam, and so on), public e-mail infrastructure redundancy, and finally remote e-mail security (that is, remote users, POP3, IMAP, web access). Each area of discussion includes techniques to minimize security exposure and maximize functionality and availability. A robust and secure e-mail infrastructure is an infrastructure that can process thousands (or even millions) of message transfers per day, stand up to attacks, and sustain a chaotic disaster at one or more locations and still continue to operate . Demonstrating how to achieve public e-mail infrastructure of this caliber is the goal of this chapter.
| | ||
| | ||
| | ||
EAN: 2147483647
Pages: 120